Your iPhone’s Data Isn’t as Private as You Think It Is | Here’s What Apple Can See and How You Can Stop It
 Credit: A. Aleksandravicius / Shutterstock
Credit: A. Aleksandravicius / Shutterstock
Toggle Dark Mode
Apple’s recent and highly controversial announcement that it will soon implement a new way of scanning for Child Sexual Abuse Material (CSAM) in iCloud Photos has also prompted some interesting and important discussions about privacy. Unfortunately, it’s also stoked the fears of many iPhone users, who fear their devices are becoming participants in a new “surveillance state.”
While Apple has been going to great lengths to assuage these concerns — even to the point of admitting that it messed up on how the new feature was announced — the initiative has also shown how many folks have erroneously believed that the information they store on their iPhone was inherently secure to begin with.
It’s an understandable belief, of course. After all, Apple is the company that posts strong privacy marketing on billboards for all to see, with the most famous of them being the Vegas-inspired slogan that, “What Happens on Your iPhone, stays on your iPhone.”
To be fair, that statement is technically true, but it carries a level of nuance that many users don’t necessarily understand. Yes, what happens on your iPhone stays on your iPhone — until it leaves your iPhone to go into iCloud.
Is iCloud Really Private?
Since iCloud is effectively on by default for most iPhone users, this means that there are a lot of things happening on your iPhone that are not actually staying on your iPhone. Technically speaking, Apple doesn’t force anybody to use iCloud, but it most definitely encourages it; when you set up a new iPhone, almost everything in iCloud is automatically enabled — including iCloud Backups and iCloud Photo Library.
While everything on your iPhone is securely encrypted — to the point where Apple is routinely pilloried by the FBI and lawmakers for making it too secure — this is not actually the case with much of what you store in iCloud.
Apple uses end-to-end encryption (E2EE) only for a few specific areas of particularly sensitive content, such as your passwords, health data, and HomeKit data, but vast swaths of personal information, including your iCloud Backups and your iCloud Photo Library are merely “encrypted at rest.”
This means that although they are stored on Apple’s servers in encrypted form, this is done using a generic encryption key that Apple has access to. This type of encryption is designed to prevent disclosure as a result of data breaches, but it doesn’t truly protect your privacy from Apple or anybody else who can legally compel Apple to give them access to your data.
This is ultimately why much of the controversy over Apple’s new CSAM Detection features is a tempest in a teapot. Apple already has full access to every photo you store in iCloud, and has been scanning those for CSAM in the cloud for at least two years now — and probably quite a bit longer.
Update: It appears that the comments Jane Horvath made during the Chief Privacy Officer Roundtable at CES 2020 were misconstrued. Horvath was asked about whether content uploaded to iCloud should be screened for CSAM, but she responded rather obliquely by saying Apple was “utilizing some technologies to help screen for child sexual abuse material.” However, Apple recently clarified to Ben Lovejoy at 9to5Mac that this was in reference to scanning iCloud Mail attachments, which have always been completely unencrypted to begin with — even “at rest” on Apple’s servers.
The newly announced CSAM Detection features simply move that scanning to the user’s device, checking photos before they’re uploaded to iCloud.
In fact, the same logic applies to iCloud Backups, which aren’t encrypted in any way either. If you’re not using iCloud Photo Library, all the photos on your device will be included in your iCloud Backups by default (unless you turn them off — see below).
To the best of our knowledge, Apple doesn’t scan photos within iCloud Backups; since everything is just stored as a big blob of data, your photos aren’t indexed by Apple, although it would still be possible for Apple to scan them if it really wanted to.
More importantly, however, since this data isn’t encrypted, Apple can and does provide it to law enforcement and other government agencies, since it has to comply with local laws. In fact, rumour has it that it was pressure from the FBI that caused Apple to abandon plans for fully encrypted iCloud Backups.
What’s Really Encrypted in iCloud?
In its iCloud Security Overview, Apple provides a detailed list of what is and what isn’t encrypted using E2EE. Don’t be misled here, however, since almost everything on this list is encrypted “on server,” but as we just noted, that simply means that somebody who steals a hard drive or server from one of Apple’s data centres — or third-party cloud providers that Apple uses — can’t read this data. Apple most certainly still can.
The only data that’s truly secured in such a way that even Apple can’t read it are the following categories:
- Apple Card transactions
- Home data
- Health data
- iCloud Keychain (saved accounts & passwords)
- Maps Favourites, Collections, and search history
- Memoji
- Payment information
- QuickType Keyboard learned vocabulary
- Safari History and iCloud Tabs
- Screen Time
- Siri information
- Wi-Fi passwords
- W1 and H1 Bluetooth keys for AirPods and Beats Headphones
It’s also worth reading the fine print here, as many of these weren’t stored encrypted until later versions of iOS. For example, Maps and Safari data are only encrypted in iOS 13 or later.
That said, this does show an increasing focus on using E2EE for data stored in iCloud, and as we said when Apple first announced the CSAM Detection feature, we’re really hoping that this is actually the first step to moving iCloud Photo Library to full E2EE. In fact, it seems really odd that Apple would go to all of this trouble otherwise, since as things stand now it can already scan everything in your iCloud Photo Library anyway.
What About Messages?
You may have noticed that Messages is missing from the above list. That’s because there’s actually a catch to how E2EE works in this case.
When Apple debuted Messages in the Cloud back in iOS 11.4, it made the point that all of your Messages app data is stored using the same end-to-end encryption as other sensitive data, and while this is technically true, your Messages in the Cloud data is still forensically accessible if you’re using iCloud Backups.
This is because the end-to-end encryption key for your Messages data is actually stored in your iCloud Backup.
In other words, if you’re using iCloud Backups, your Messages data isn’t as encrypted as you think it is. Apple does explain this in its iCloud Security Overview, but it’s obviously not something the company really advertises.
Messages in iCloud also uses end-to-end encryption. If you have iCloud Backup turned on, your backup includes a copy of the key protecting your Messages. This ensures you can recover your Messages if you lose access to iCloud Keychain and your trusted devices. When you turn off iCloud Backup, a new key is generated on your device to protect future messages and isn’t stored by Apple.
Apple’s iCloud Security Overview
Apple’s reasons for doing this are somewhat altruistic, since they want to avoid the risk of locking you out of your data, but it does mean that as long as you’re backing up your iPhone or iPad to iCloud, your Messages conversation history isn’t technically secure.
As with iCloud Photo Library, if you’re not using Messages in the Cloud, then your messages will be in your iCloud Backup, and if you are using Messages in the Cloud, then the key to decrypt them is in your iCloud Backup.
Fortunately, if you disable iCloud Backups, a new key is automatically generated, so Messages in the Cloud will be secure, provided you leave iCloud Backups off.
How to Disable iCloud Backups
As we noted earlier, when you set up a brand-new iPhone or iPad, iCloud Backups are enabled by default. If you’re not a paying iCloud customer, there’s a good chance they’ll start failing, as the free 5GB that Apple gives you will get eaten up pretty quickly. If you’re on a paid storage plan, however, either individually or as part of an Apple One bundle, then your device has likely been backing itself up to iCloud all along without you even realizing it.
For most users, this is a good thing. We’ve helped a number of less tech-savvy friends and family over the years who were saved from losing precious memories only because of iCloud Backups.
While many of us are perfectly comfortable leaving iCloud Backups enabled for this reason, we also understand that privacy-conscious users may not be too keen on the idea of having some of their data stored on Apple’s servers in a human-readable form. Fortunately, that’s easy to fix.
The most direct way of dealing with this is to simply disable iCloud Backups entirely. Here’s how to do this:
- On your iPhone or iPad, open your Settings app.
- Tap your name at the very top of the screen.
- Tap iCloud.
- Tap iCloud Backup.
- Toggle the iCloud Backup setting off.
- Repeat these steps for your other iOS devices.
Unfortunately, this won’t remove your existing iCloud Backups. That’s a separate part:
- On your iPhone or iPad, open your Settings app.
- Tap your name at the very top of the screen.
- Tap iCloud.
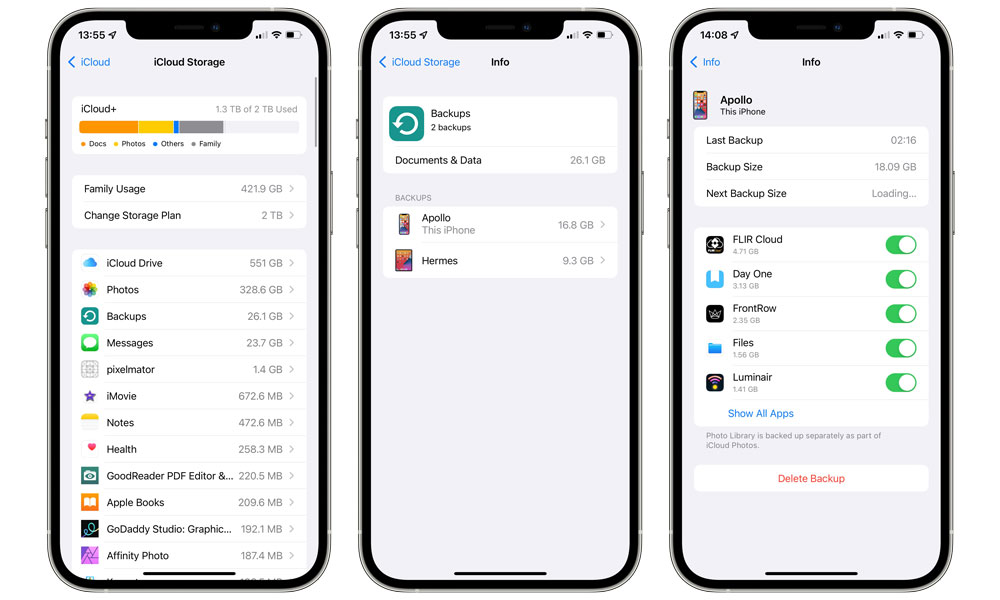
- Tap Manage Storage.
- Tap Backups. You’ll see a list of backups for all your devices associated with your iCloud account.
- Tap on the name of a backup.
- At the bottom, tap Delete Backup.
- Repeat steps 6 & 7 for any additional iCloud Backups you want to remove.
Note that you can also use the Manage Storage section above to selectively remove content from your iCloud Backups. This can be useful in situations where you might have no problem with a general backup of your device, but there are certain sensitive items that you don’t want included in your iCloud Backup, such as photos and videos or data from third-party messaging apps.
The good news is that if you do decide to eschew iCloud Backups entirely, you can still backup your iPhone and iPad directly to your computer. It’s a more manual process, but at least all of your data will remain under your direct control — and you can even encrypt your local backup for added security.
Getting Your Photos Out of iCloud
In the case of data in your Photos app, however, if you’re using iCloud Photo Library, these aren’t included in your iCloud Backup, but they are stored on Apple’s servers, and just like iCloud Backups, they’re not end-to-end encrypted. To remove this content entirely, you need to first disable iCloud Photo Library:
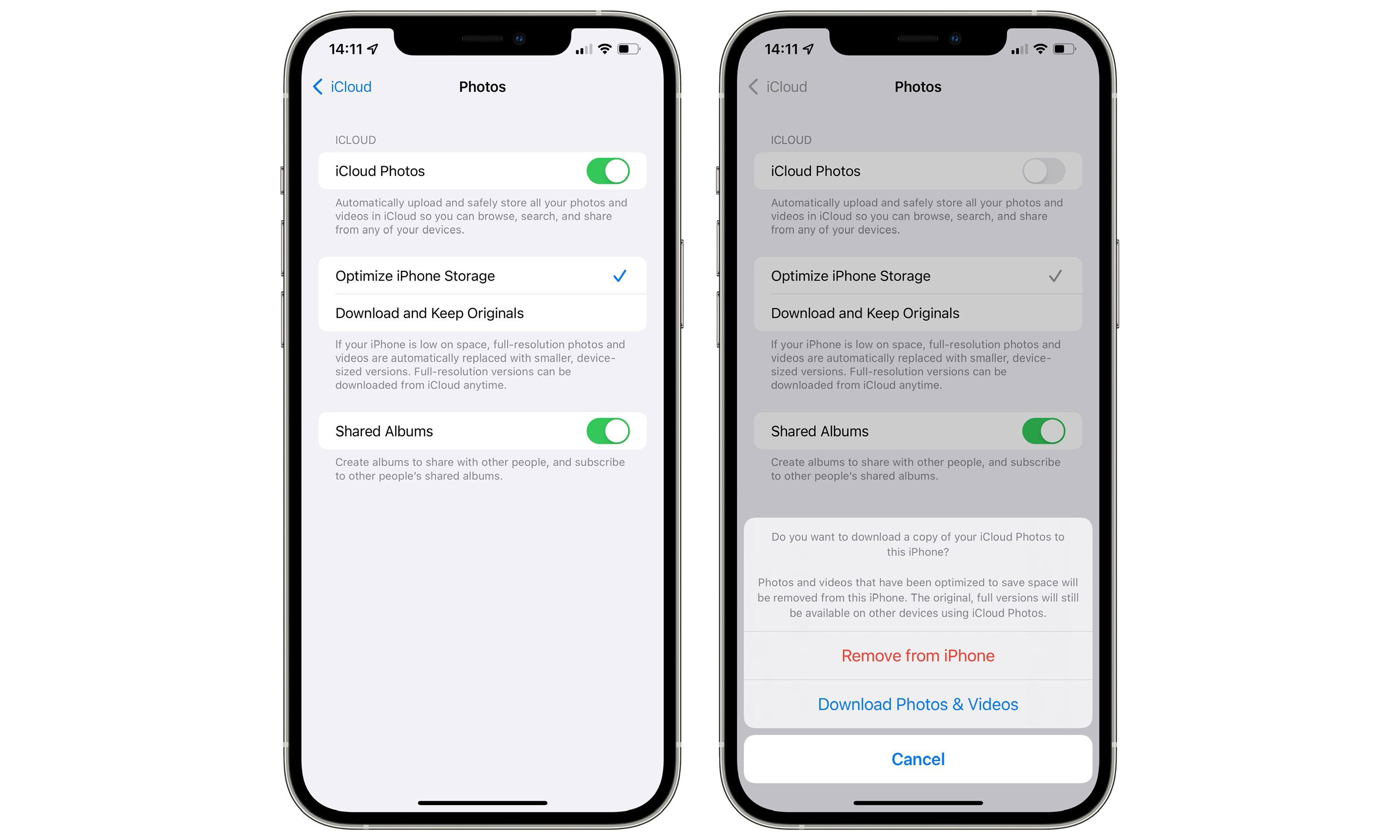
- On your iPhone or iPad, open your Settings app.
- Tap your name at the very top of the screen.
- Tap iCloud.
- Tap Photos.
- Tap iCloud Photos to toggle it off.
- From the next screen, chose Download Photos & Videos to download everything in your iCloud Photo Library to your iPhone or iPad (if you have enough free storage) or choose Remove from iPhone/iPad if you plan to download them to another device like your Mac.
Repeat these steps from your other devices, making sure that you choose the Download Photos & Videos option from at least one of them to preserve a copy of all of your media.
As with iCloud Backups, disabling iCloud Photo Library doesn’t remove your photos from iCloud — it just stops syncing them, leaving the iCloud Photo Library as-is.
However, if you don’t want any of your photos stored on Apple’s servers at all, then you’ll have to go and remove them manually. Before doing this, make sure iCloud Photo Library has been disabled on all of your devices that share the same iCloud account and that you’ve safely downloaded all of your photos to at least one of your devices. Then follow these steps:
- On your iPhone or iPad, open your Settings app.
- Tap your name at the very top of the screen.
- Tap iCloud.
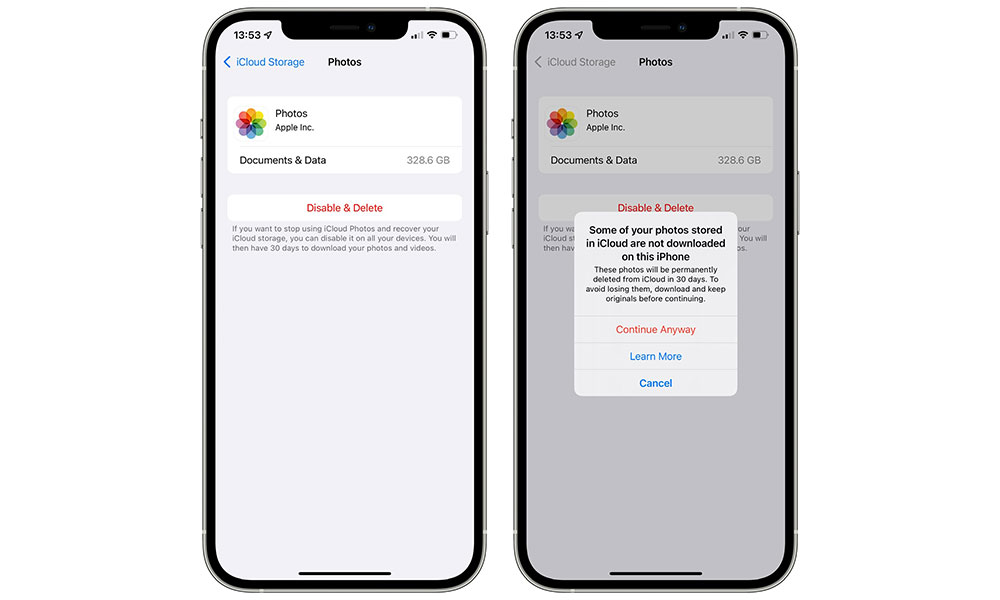
- Tap Manage Storage.
- Tap Photos.
- Tap Disable & Delete. You will be warned if some of your photos have not been downloaded onto the current device.
- Again, before proceeding, make absolutely sure that you’ve downloaded all of your photos to at least one of your devices.
- If you’re sure you have all of your photos downloaded, tap Continue Anyway.
Note that if you’re still using iCloud Backups, disabling iCloud Photo Library will begin including your photos in your iCloud Backups. You’ll need to disable this manually:
- On your iPhone or iPad, open your Settings app.
- Tap your name at the very top of the screen.
- Tap iCloud.
- Tap Manage Storage.
- Tap Backups. You’ll see a list of backups for all your devices associated with your iCloud account.
- Tap on the name of your device.
- Tap on the switch beside Photo Library to toggle it off.
Note that your photos won’t be removed from your existing iCloud Backups that are already stored on Apple’s servers, but since Apple only keeps your last three iCloud Backups, they’ll eventually be overwritten by future backups. Since Apple retained your iCloud Photo Library for thirty days after you disable it, chances are that your photos will disappear from your backups much sooner anyway.