Apple Hardens iMessage Against Quantum Computing Attacks
 Credit: Getty Images / Unsplash+
Credit: Getty Images / Unsplash+
Toggle Dark Mode
There’s little doubt that the iPhone has become prey for serious attacks by state-sponsored agencies with nearly unlimited resources at their disposal. Apple has been playing a cat-and-mouse game with iPhone security for years, with iMessage on the front lines of that war.
While most of us will (hopefully) never be important enough to become targeted by the likes of military-grade spyware like Pegasus or Predator, the “zero-day” vulnerabilities that these tools expose and exploit can easily fall into the hands of more mundane cybercriminals if they’re left unpatched.
As a result, Apple not only has to be quick to respond to such reports, but also, over the past few years, it’s realized that a purely reactive or defensive approach isn’t enough. With iOS 14, Apple went on the offensive with BlastDoor a new iOS security feature that would isolate incoming messages and examine them in an isolated and secure area of memory before letting them through. As the name suggests, this is akin to taking suspicious parcels into a bomb-proof room to check them for explosives.
Since iMessage is the most common attack vector for zero-click exploits — most of these are received in the Messages app — BlastDoor and other hardening of the iOS messaging environment helped to protect against these attacks. However, it wasn’t long before mercenary hackers found ways around it, leading Apple to try to sue the most prominent of these companies out of existence.
However, zero-click exploits are only part of the problem. With iOS 16 and iOS 17, Apple tightened things up even further, adding a new Lockdown Mode, iMessage Contact Key Verification, full end-to-end encryption for nearly everything in iCloud, and support for hardware security keys.
With all that in play, it’s fair to say that the iPhone is the most secure consumer platform on the market and iMessage is easily among the most secure messaging platforms. However, Apple isn’t stopping there.
Skating to Where the Puck Is Going To Be
One of Steve Jobs’ favorite quotes was from The Great One, hockey legend Wayne Gretzky: “I skate to where the puck is going to be, not where it has been.” It’s no surprise that’s still in Apple’s DNA, and it’s especially salient in this case, as it’s the only way to stay ahead of the well-funded black hat hackers, mercenaries, and cyber criminals that are constantly trying to rip the iPhone’s security wide open.
As a result, the company’s engineers and security experts are working on defenses against attacks that might still be years away from becoming practical — specifically, those that could someday be waged by powerful quantum computers — and those are already being incorporated into iOS 17.4.
The new techniques promise to strengthen iMessage encryption well beyond anything we’ve ever seen in the public sphere with the goal of protecting against the technology of the future.
It’s already virtually impossible to decrypt iMessage conversations today — at least in anyone’s lifetime. However, Apple recognizes that won’t be the case forever. Technology marches on, and encryption protocols that were state-of-the-art 20–30 years ago can now be sliced through almost effortlessly by modern computing systems.
Not unlike a physical lock, the trick to encryption algorithms isn’t to make something that’s 100% unbreakable but rather to create something that takes so much effort to break that it’s simply not worth anybody’s time. Public key cryptography techniques have evolved over the past few decades, but the goal has always been to create mathematical equations that are so complex and computationally intensive that computers will take thousands of years to unravel them without the necessary keys.
When building encryption algorithms, security researchers also account for Moore’s Law, which reflects the normal trend of how computing power increases year over year. However, Apple’s concern is that the rise of quantum computing will change the equation by opening up more creative methods for unraveling encryption algorithms.
A sufficiently powerful quantum computer could solve these classical mathematical problems in fundamentally different ways, and therefore — in theory — do so fast enough to threaten the security of end-to-end encrypted communications. Apple
Such quantum computers don’t exist today, and most experts agree that we won’t see them anytime soon. Apple isn’t taking any chances, though, as it recognizes that the iMessage conversations of today could still be decrypted in a far-off tomorrow.
The risk here is what’s known in the security community as a “harvest now, decrypt later” attack. In broad terms, this refers to collecting encrypted data without necessarily having the ability to decrypt it on the spot. In simplest terms, “later” could be a few days or hours after the data is stolen, but in this case, Apple is looking at what could be possible years from now.
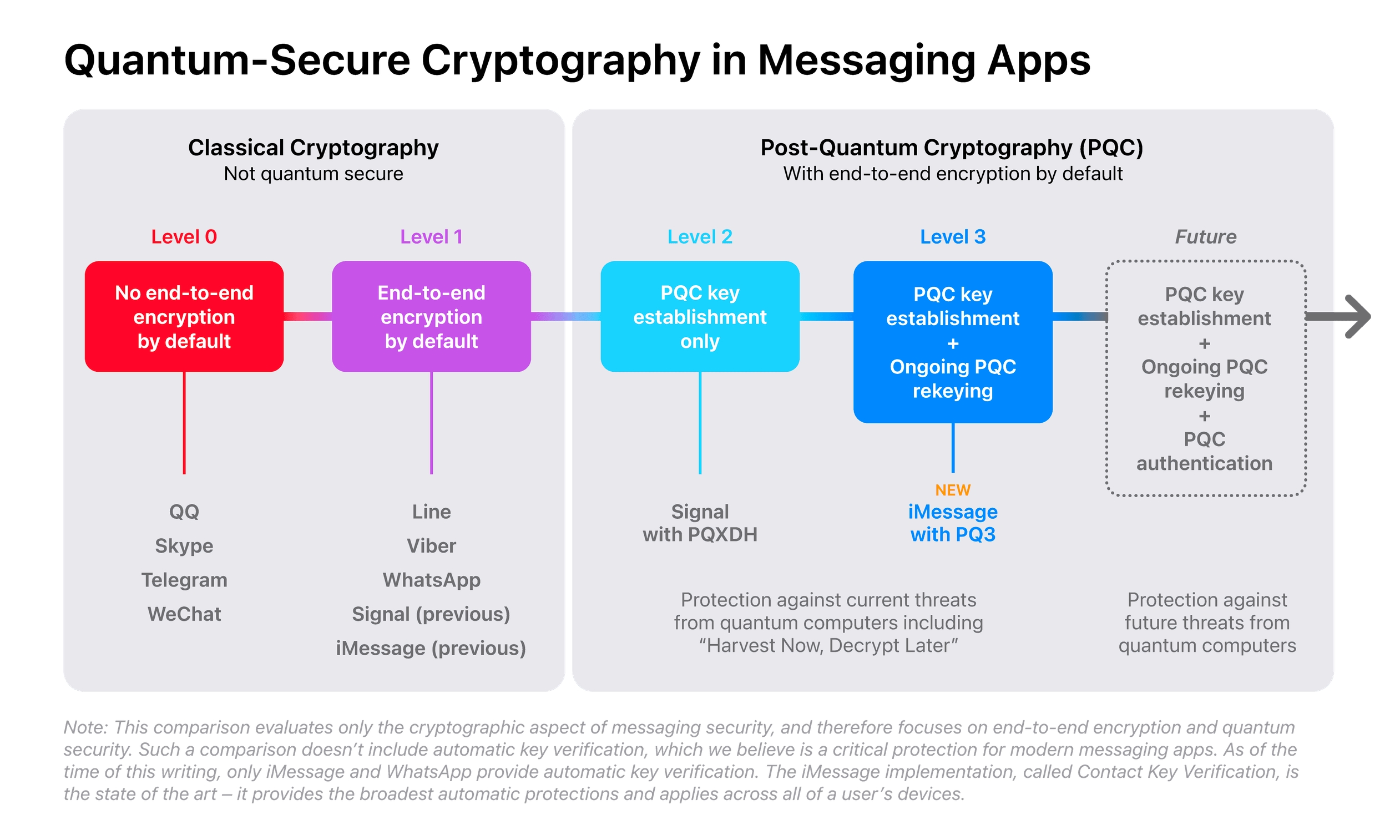
The changes are part of a new system Apple has designated as PQ3, which it calls “a groundbreaking post-quantum cryptographic protocol that advances the state of the art of end-to-end secure messaging.”
PQ3 is the first messaging protocol to reach what we call Level 3 security — providing protocol protections that surpass those in all other widely deployed messaging apps. To our knowledge, PQ3 has the strongest security properties of any at-scale messaging protocol in the world. Apple
Apple has published a post on its security blog for those interested in the nitty-gritty details of how this all works, but suffice it to say, what Apple is aiming for is an encryption protocol that won’t be crackable by even the most sophisticated quantum computers imagined today.
While the attacks may not be here, the security is starting to roll out already. The PQ3 protocol is in the latest iOS 17.4, iPadOS 17.4, macOS 17.4, and watchOS 10.4 betas, and it’s expected to start rolling out officially with the launch of those versions next month.
Once everything is in place, Apple says the iMessage conversations between devices that support PQ3 will be “automatically ramping up to the post-quantum encryption protocol.” Apple expects PQ3 will fully replace the existing protocol “within all supported conversations this year.”