How Apple Will Notify You If You’re a State-Sponsored Spyware Target
 Credit: Robert Coolen
Credit: Robert Coolen
Toggle Dark Mode
Yesterday Apple announced it’s launching a lawsuit against NSO Group, the Israeli firm responsible for Pegasus, the industrial spyware that’s been used to hack into the iPhones of journalists, activists, dissidents, and even government officials.
Although Pegasus was ostensibly never supposed to be used for anything other than counterterrorism and fighting crime, it’s fair to say that many governments have different ideas of what constitutes terrorism or criminal activity. Even beyond this, however, it’s clear that some state actors have pushed the limits of even that.
With yesterday’s lawsuit, Apple aims to put an end to this once and for all, and the company isn’t mincing words about it either.
The steps we’re taking today will send a clear message: In a free society, it is unacceptable to weaponize powerful state-sponsored spyware against those who seek to make the world a better place.
Ivan Krsti?, head of Apple Security Engineering and Architecture
In fact, the lawsuit opens by calling out NSO Group, the defendants, as “amoral 21st century mercenaries who have created highly sophisticated cyber-surveillance machinery that invites routine and flagrant abuse.”
Apple also points out that the U.S. Government has already imposed sanctions against NSO, confirming that Pegasus has “enabled foreign governments to conduct transnational repression, which is the practice of authoritarian governments targeting dissidents, journalists, and activists outside of their sovereign borders to silence dissent.”
Warning Users
As John Gruber points out, it’s clear that Apple is absolutely furious about NSO Group, and trying to sue the company out of existence is just a start. Apple also shared in its press release that it’s already notifying the users who may have been targeted by the most recent FORCEDENTRY Pegasus exploit. It plans to continue monitoring for similar attacks and letting users know if they’ve potentially fallen victim to them.
Apple is notifying the small number of users that it discovered may have been targeted by FORCEDENTRY. Any time Apple discovers activity consistent with a state-sponsored spyware attack, Apple will notify the affected users in accordance with industry best practices.
Apple
The company is making good on this promise right away, with a new support document published yesterday outlining how these “threat notifications” will work.
While Apple doesn’t go into exactly how it determines one of its users may have been targeted by a state-sponsored attack, it does explain that users will be notified in three ways:
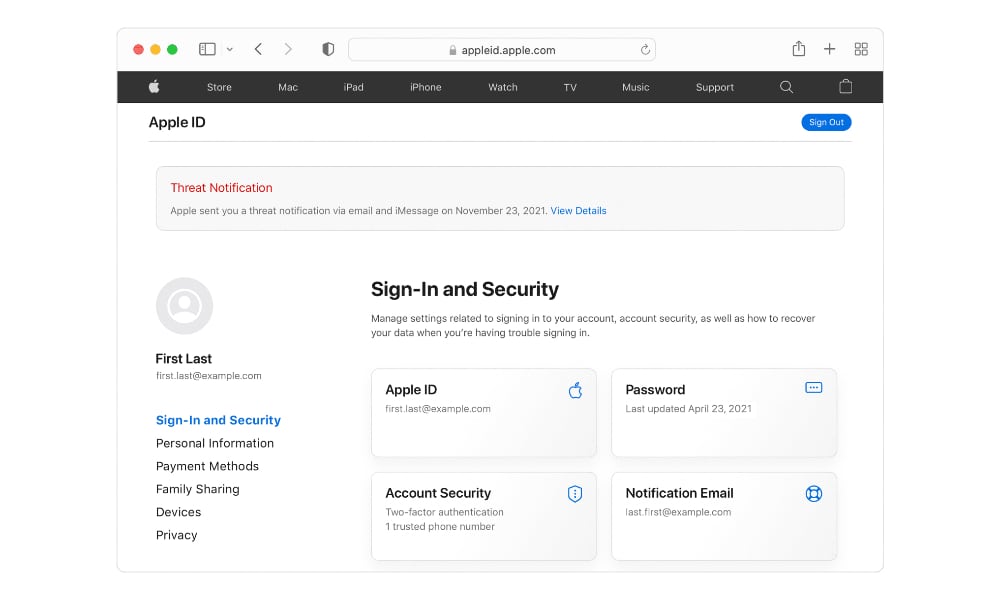
- A Threat Notification will be displayed at the top of the user’s Apple ID page at appleid.apple.com.
- An email notification will be sent to the email address(es) associated with the user’s Apple ID.
- An iMessage notification will also be sent to the phone number(s) associated with the user’s Apple ID.
The use of plural language in Apple’s support document suggests that these alerts will basically go out as an email and iMessage blast to every address and phone number you have on file, so you’ll have little to no chance of missing them. However, if you miss all these — after all, it’s not hard to imagine NSO Group taking steps to have Pegasus suppress them — you’ll still have a warning banner on your Apple ID home page. Plus, since such spyware runs directly on your iPhone, there’s not much it can do about email messages sent to accounts that aren’t configured on your mobile devices.
The threat notification banner on your Apple ID homepage is also important to prevent scammers from trying to exploit users through fake messages purporting to be Apple’s threat notifications. Apple notes that its legitimate notifications will never ask you to “click any links, open files, install apps or profiles, or provide your Apple ID password or verification code by email or on the phone.” If you receive a threat notification, you can verify its legitimacy by signing in to appleid.apple.com to see if it’s also listed there.
In the support document, Apple once again emphasizes that most people are very unlikely ever to be targets of such an attack, but those who are can rest a bit easier in knowing that Apple has their backs.
Unlike traditional cybercriminals, state-sponsored attackers apply exceptional resources to target a very small number of specific individuals and their devices, which makes these attacks much harder to detect and prevent. State-sponsored attacks are highly complex, cost millions of dollars to develop, and often have a short shelf life. The vast majority of users will never be targeted by such attacks.
Apple
Apple isn’t explaining what causes it to issue threat notifications, as it wants to avoid tipping its hand to state-sponsored attackers, who might use that information to evade detection in the future.
As Apple noted in yesterday’s announcement, it has already begun sending out these notifications. According to Reuters, at least six Thai activists and researchers were alerted that their iPhones may have been targeted by “state-sponsored attackers.” A political scientist, security researcher, two activists, a politician, and a rapper were among the group. The six were not directly related, except that they are all perceived as critical of the Thai government.
The messages, which were shared with Reuters, read in part, “if your device is compromised by a state-sponsored attacker, they may be able to remotely access your sensitive data, communications, or even the camera and microphone.” It’s not clear from the alerts if Apple believed that the Thais were being targeted specifically by Pegasus or if another state-sponsored spyware tool was involved.