Your Apple ID Is Extremely Valuable to Hackers — Here’s How to Protect Yourself
 Credit: Hadrian / Shutterstock
Credit: Hadrian / Shutterstock
Toggle Dark Mode
Apple works hard to make the iPhone one of the most secure mobile devices available, with industry-leading hardware security features, a tightly locked-down operating system architecture, a strong focus on privacy features, and a well-regulated App Store.
These are all huge advantages of owning an iPhone, and extremely important considering that the popularity of Apple’s mobile devices makes them a very attractive target for hackers and malware developers. Unfortunately, the same popularity leaves users vulnerable in an area that it’s much more difficult for Apple to defend against without user education and cooperation: phishing attacks.
In fact, according to a new report by Check Point Research on “brand phishing,” Apple IDs are the single most attractive item for hackers, with 10% of all phishing attempts targeted at stealing Apple ID usernames and passwords.
This beat out Netflix at 9% and the very odd third-place contender, Yahoo, which came in at 6%, slightly edging out WhatsApp and PayPal. Facebook, Microsoft, and eBay each accounted for only 3% of recent phishing attempts, while Amazon came in at a mere 1%.
As Check Point explains, “brand phishing involves the attacker imitating an official website of a known brand by using a similar domain or URL, and usually a web page similar to the original website.”
The goal, of course, is to manipulate users into thinking that they’re logging in to a legitimate website, thereby giving up their credentials to criminals who will, in turn, sell them on the dark web.
One of the reasons Apple is the most common phishing target is because Apple IDs apparently sell for much higher values on the dark web than any other credentials except those for banks and other financial institutions. However, as the most recent report shows, phishing attacks against Apple IDs have recently outpaced even those seeking banking credentials, with Chase and PayPal being the only financial institutions in the list, each coming in at 5% — about half the popularity of Apple IDs.
Why Apple IDs?
You may not think that your Apple ID is that big of a deal, especially if you don’t use iCloud for email, but there are still a lot of reasons why a hacker might want to get their hands on yours, as a lot of your digital life is still wrapped up within your Apple ID.
For example, with access to your Apple ID, a hacker can track your location, remotely wipe all of your devices, intercept your iMessages, SMS messages, and even FaceTime calls, potentially reset other passwords, and access almost anything that’s stored in your iCloud Backups, including call history, web browsing history, and much more.
While highly sensitive information like health data and Apple Pay cards are stored with higher levels of encryption, security researchers have found ways to get access to at least some of this data once your Apple ID password is known.
This also doesn’t include the wealth of data that gets stored in your iCloud Backups by third-party apps, many of which aren’t nearly as concerned about security and privacy as Apple is.
How to Protect Yourself
These kinds of phishing attacks most commonly come in the form of email or text messages that try to direct unsuspecting users to a fake website that looks like an official Apple ID login page. Hackers can also plant redirects on various websites that could deceive users into thinking that they need to log into their Apple ID for some seemingly valid reason, such as displaying a security alert that makes them think that their account has already been compromised.
Some of the most common types of social engineering attacks will claim that your Apple account is “locked” and that you need to log in and confirm your password to restore access, sending a receipt claiming that you purchased something and offering a “Cancel” link, or a message or pop-up claiming to be from Apple Support and offering to help “fix” your Mac or iPhone.
So the first and most obvious way to avoid scams like these, and to help your friends do so as well, is to be extremely suspicious about any emails, text messages, or warnings that you receive. In much the same way that your bank has been telling you for years that it will never ask you to divulge your PIN, Apple will never send you an email asking you to click a link to log into your Apple ID and “verify” your information.
If you’re concerned that there might be a problem, simply open a separate browser window — preferably a private browser window — and visit Apple’s website directly to log into your Apple ID and check if there’s anything going on that you need to deal with.
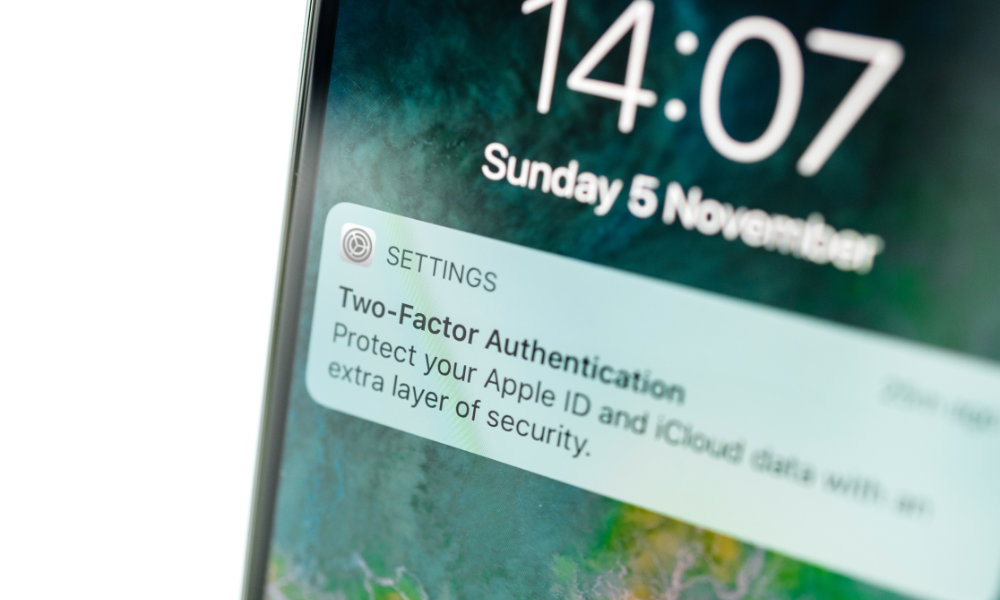
We also continue to strongly recommend that you enable two-factor authentication (2FA) on your Apple ID.
Once configured, 2FA requires that you enter a six-digit verification code that gets sent to your iPhone each time you (or somebody else) tries to sign in with your Apple ID from a device that you haven’t already explicitly trusted.
While this isn’t completely foolproof in protecting you against phishing attacks, it makes it a significant order of magnitude more difficult for hackers to actually gain access to your Apple ID, since they would need to create a “man-in-the-middle” fake website that would pass on your credentials to the real Apple servers in order to get Apple to send you a valid two-factor code. Then, on top of that, they’d have to use the intercepted code within about 30 seconds before it became invalid.
Further, as an added security measure, Apple’s verification code notification also shows you the location where the person is trying to sign in from, which can be a huge red flag if it’s nowhere near where you’re actually located. So even if you’re tricked into signing in to a phishing website, if you’re located somewhere in North America and the notification says that somebody is trying to log in to your account from Eastern Europe, alarm bells should go off.







