Google Is Making It Easier for iPhone Users to Secure Their Accounts
 Credit: OpturaDesign / Shutterstock
Credit: OpturaDesign / Shutterstock
Toggle Dark Mode
Perhaps ironically, Google actually leads the pack when it comes to helping you keep your online data secure from hackers. It was one of the first major online service providers to embrace strong two-factor authentication many years ago, and has also worked with and supported physical USB, NFC, and Bluetooth security keys for longer than just about anybody else.
A couple of years ago, Google took this a step further and wrapped it all up into a package known as its Advanced Protection Program (APP) — a feature that’s freely available to any Gmail or G Suite user for nothing more than the cost of the physical security keys necessary for highly-secure authentication.
Of course, even the best security isn’t going to work very well if you can’t use it on all of your devices, either because it’s not possible or simply too cumbersome to bother with, so Google has been making some great strides in welcoming iPhone users into the fold, quickly adapting new capabilities as iOS begins to open them up.
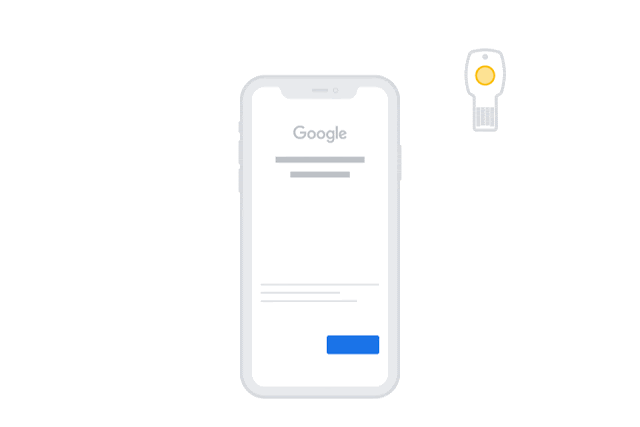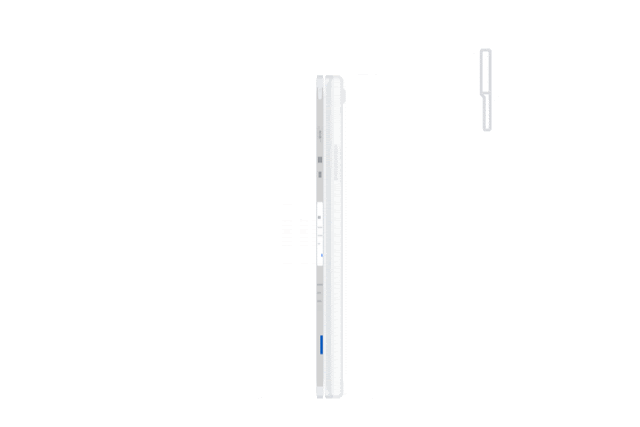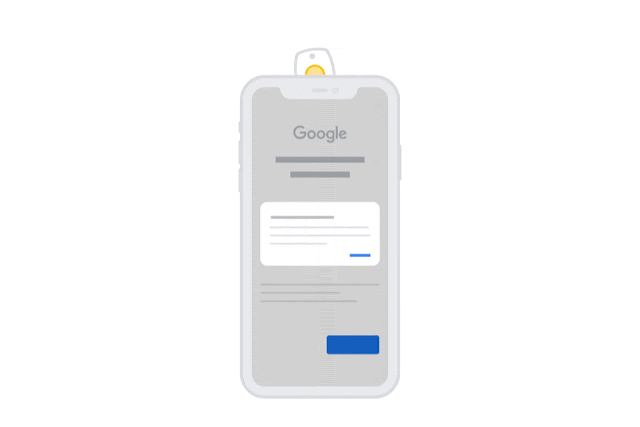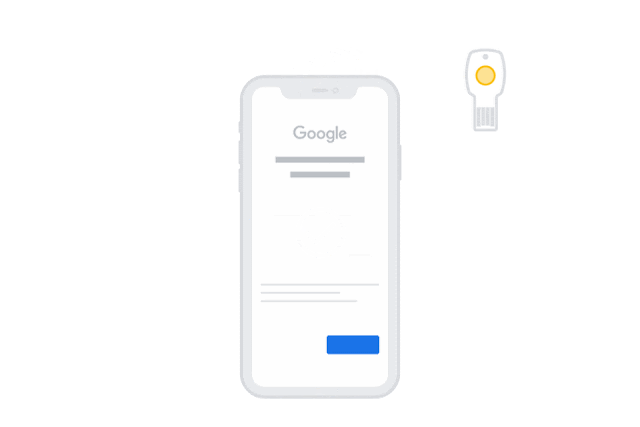
For example, earlier this year Google began allowing the iPhone to be used as a Bluetooth security key, replacing the need to insert a physical USB device into a Mac or PC port when logging into your Gmail or YouTube account, and now it’s taken the next step of embracing the new openness of iOS 13 to enable USB and NFC security keys to be used directly with iPhones and iPads.
To be clear, this capability comes as a result of changes in iOS 13.3 late last year, so it’s not Google that’s been dragging its heels, but rather Apple that didn’t previously permit the necessary access to the NFC hardware or USB ports by third-party apps. In fact, it’s been possible to use physical security keys on many Android devices for years, so this was more a matter of Google waiting for Apple than the other way around. That said, the Android method was somewhat proprietary, and it was only about a year ago that a universal web authentication standard was adopted by the W3C consortium, providing a common framework for everybody to work with.
Now in an announcement on its security blog, Google notes that it has begun rolling out support for new “WebAuthn” standard for Google accounts on Apple devices running iOS 13.3 and later, which should vastly simplify the experience of using a security key on an iPhone or iPad, and hopefully will encourage more users to take advantage of the better security offered by the Advanced Protection Program.
Benefits of Physical Security Keys
As our regular readers will know, we’re strong proponents of two-factor authentication, since it makes it significantly more difficult for hackers to get into your account by requiring another piece of information in addition to your passcode.
Most classic two-factor systems require you to generate a six-digit code using an app, or simply send a code out to your phone number via a text message, although this latter method is falling out of favour and we generally recommend against using it as much as possible, as many hackers have resorted to “SIM-jacking” attacks that allow them to intercept your SMS messages.
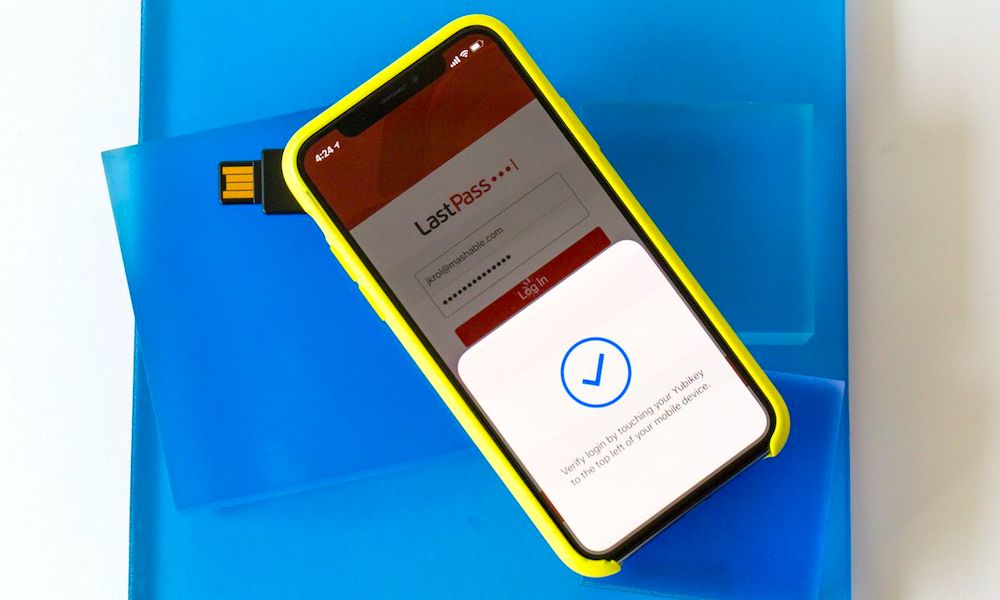
Physical security keys, on the other hand, are an even more secure method to make sure that nobody but you can get into your account, since unlike a code, it literally requires you to have the key on your person in order to access your account. This can take the form of a physical USB key that gets plugged into a port, an NFC key that has to be tapped against the device, or a Bluetooth key that needs to be at least with a few feet. An account that uses only physical security keys as as a second factor is virtually immune to hacking and phishing attempts.
You see, as secure as app-generated codes may seem at first blush — after all, you have to generate the code on your device and key it in — it’s still relatively easy for a phishing attack to get that code out of you. All a hacker needs to do is set up a fake website that looks like a site you could legitimately be logging into, and use it as a “man-in-the-middle,” capturing all of your login details and relaying them to the real server, including the six-digit code you generate in your authentication app.
By comparison, due to the way that physical security keys work, they can’t be intercepted by this kind of attack, since it’s impossible for an intermediary site to make a legitimate request for your security key in the first place, much less capture that information and pass it on to the legitimate site. In short, you can only use your security key with the legitimate site you’re logging into, and it has to be physically connected to your computer or in close proximity.
That said, there’s no reason you can’t use both physical security keys and one-time passcodes in tandem, and Google has let you do this for years. However, if you want the best security, Google’s APP is designed to lock down your account so only physical security keys can be used as a second factor, in addition enforcing a few other tighter security restrictions, such as limiting the third-party apps that can access your account.
Note that while Apple doesn’t support traditional physical security keys, likely out of a desire to keep things simple, Apple does offer some of the best code-based two-factor authentication, since it almost treats your physical iOS and macOS devices as security keys, although it’s important to note that unlike Google’s phone-based solution, it doesn’t require the device receiving the code to be anywhere near the device that you’re signing into, and can therefore still be more prone to phishing attacks. Apple does offer a slight advantage, however, in that it will notify you where the sign-in attempt is coming from, at least in terms of a general geographic area, so if you’re logging into iCloud from a browser in Toronto and the authentication request says somebody in Kalamazoo is trying to access your account, that should be a good tip-off that something isn’t quite right.
How It Works
Up until now if you wanted to log in using a physical security key on an iPhone or iPad you needed to use Google’s Smart Lock app and have a Bluetooth key paired with your device. This created a slightly inelegant sign-in process which required Google to prompt you to download or open Smart Lock and authenticate your account there by pressing a button on your Bluetooth security fob, after which you’d be returned to whatever Google app you were actually trying to sign into.
Needless to say, this was enough of an encumbrance that it discouraged many users from using strong two-factor authentication at all, and made folks especially reluctant to enroll in Google’s Advanced Protection Program, which requires the exclusive use of physical security keys.
With this change, however, the Smart Lock will no longer be required as long as you have a USB or NFC security key, such as the Titan keys sold by Google itself. Users with a standard USB-only key will be able to plug it into their iPhone or iPad using a Lightning to USB connector, or into the USB-C port on an iPad Pro using an appropriate USB-A to USB-C adapter, while obviously if you have a Lightning security key or a USB-C security key, no adapters will be required.
What’s even cooler, however, is that if you have a newer NFC-capable key, you’ll be able to authenticate simply by tapping your key to the back of your iPhone when logging in, and this will be done natively, without the need to redirect you to the secondary Smart Lock app.
That said, there are still advantages to keeping the Smart Lock app around, since you’ll need it for Bluetooth keys, and it’s also still necessary if you want to use your iPhone as a Bluetooth security key to log into other devices.
Note that Google will be rolling these changes out gradually, so you may not see them right away, but within the next 15 days they should be available to all G Suite, Cloud Identity, and personal Google account users.