You Can Now Use Your iPhone as a Physical Security Key for Google’s Two-Factor Authentication
 Credit: OpturaDesign / Shutterstock
Credit: OpturaDesign / Shutterstock
Toggle Dark Mode
We’ve long touted the benefits of two-factor authentication, which is one of the best ways to secure your important online accounts against hackers, and while iPhone users already benefit from built-in two-factor authentication for their Apple ID, it can often be more complicated to set up for other online accounts, which usually require things like one-time password generating apps or SMS messages — an older method that’s falling out of favour due to the higher risk of “SIM-jacking” attacks that allow SMS passwords to be intercepted by hackers.
Google has actually long led the way on two-factor authentication, however, being one of the first major companies to adopt the use of physical security keys several years ago in Chrome, and helping to drive it forward as an open standard for other browsers — an initiative that helped support for it finally arrive in Safari with this year’s release of macOS Catalina and iOS 13.
Physical security keys are USB, Bluetooth, or NFC devices that you carry around with you, usually on your keychain, that provide an additional level of security that makes it extremely difficult for hackers to access your account, and also has the even more important advantage of preventing phishing attacks. Using a physical key requires connecting it to your device after you enter your password to prove that it’s really you logging in, and the request for the physical key can only come from the actual site that you originally registered it with.
For desktop and laptop computers this is most commonly done by plugging the key into a USB port, however until recently iPhone and iPad users have had to rely on Bluetooth keys with apps specially designed to interface with them, such as Google’s own Smart Lock iOS app. With the release of iOS 13.3 last month, however, Apple finally opened up support for directly connecting security keys to the Lightning port, and even support for the NFC-based security keys that were previously the exclusive domain of Android devices.
In addition to its longstanding support for physical security keys, Google announced last year that it would allow Android 7+ devices to be used as two-factor keys when signing into its own services such as Gmail and Google Drive. At the time, however, iPhone owners were left out of this plan, leaving them to either rely on physical keys for the best possible security, or settle for a less secure alternative such as one-time passwords generated by an app like Google Authenticator, or using Google Prompt, a method similar to Apple’s own two-factor authentication that would simply display an alert in the Gmail or Google apps on your iPhone to confirm your login.
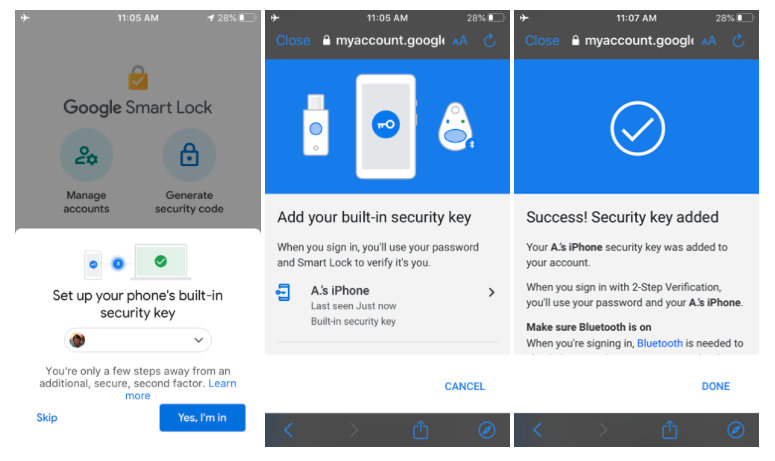
This week, however, Google has now invited iPhone users to the party with an update to the Google Smart Lock iOS app that allows it to be used as an actual physical U2F security key.
Google Prompt vs Google Smart Lock
While on the surface this may seem very similar to the Google Prompt feature that’s found in Gmail and the Google Search app, it’s actually very different and considerably more secure.
The Google Prompt method isn’t tied in any way to your location or what device you’re signing in with. Instead, it simply provides a notification on your iPhone whenever anybody signs in from anywhere, sent to your iPhone over the internet.
By contrast, with the new Google Smart Lock app, the iPhone actually behaves in the same way as a Bluetooth security key, and in fact according to a cryptographer at Google it actually uses the iPhone’s Secure Enclave — the same chip that stores Face ID and Apple Pay data — as the security key.
Since it works just like a FIDO U2F security key, this means that your iPhone actually has to be in Bluetooth range of the computer where you’re signing in, meaning that somebody can’t be signing in somewhere else on your behalf. Further, the nature of the U2F exchange means that only the site to which the key is registered — Google in this case — can actually request the key, and that request comes directly from your actual computer, over Bluetooth.
Google’s Advanced Protection Program
If you’re a Gmail user who wants to maximize your security, you can actually enrol in Google’s Advanced Protection Program, which will enforce the use of physical security keys with your Google account, as well as locking out access by less secure third-party apps.
The Advanced Protection Program (APP) isn’t for everybody, as the higher security settings impact a number of areas. For one thing, turning on APP will block a lot of third-party apps from accessing your data, although Apple’s own Mail, Calendar, and Contacts apps are considered “trusted” so you’ll be okay with those.
What’s great, however, is that if you’re concerned about maximizing security on your Google account, APP offers a one-step process for locking things down, disabling the use of all two-factor authentication methods except for the use of physical keys. Unfortunately, in the past this was a bit more cumbersome for Apple users, since you had to purchase at least two physical keys and use Chrome or Firefox as your primary browser for accessing Gmail and other Google apps.
However, now that Safari and iOS 13.3 all support physical keys, and you can use your iPhone as a physical key when logging in to just about any computer, there’s far less of a barrier for those who are heavily invested in the Apple ecosystem, and even if you don’t want to go for the full Advanced Protection Program treatment, we’d still strongly recommend setting up and using physical security keys, especially now that you can use your iPhone as one.
How Does This Prevent Phishing?
If you’re unfamiliar with the term, “phishing” refers to the process of trying to steal a user’s password by setting up a fake website and then trying to get users to log into it.
For example, a hacker could setup a website that looks identical to the Gmail.com sign-in page, and then send you an email with a disguised link that makes you click on it and sign in without realizing that you’re in the wrong place. While modern browsers have taken steps to mitigate these risks, clever hackers are constantly finding ways around them.
Even with two-factor authentication, it’s not difficult for a determined hacker to get access to your account, since there’s still no direct connection between your one-time password and the actual login process. All a hacker would need to do is capture your credentials and submit them to the real Google server at the same time. In this case, you’d be supplying your two-factor authentication credentials to the hacker and they in turn would use them to access your account. Even the Google Prompt method can be phished in this case, since users who thought they were signing into the real Gmail.com page would of course tap “Yes” on their iPhone, allowing the hacker behind the scenes to gain access to their actual Google account.
Physical U2F security keys significantly mitigate this risk because they rely on a two-way handshake between the website that you’re actually signing into, the device you’re signing in with, and the physical key. When you sign into Gmail with a physical key, Google asks your browser to ask you to plug in the specific key that’s registered to your account. This request can’t be forged or intercepted by a hacker, and even if you insert the physical security key, it won’t respond with usable credentials to anything except a valid request.
How to Set It up
If you’re already using two-factor authentication with your Google account — which you definitely should be — then setting this up is simply a matter of installing the latest update to Google Smart Lock and opening it up. If you’ve never used Google Smart Lock before, you’ll be prompted to sign in, but once signed in you should see a prompt to “Set up your phone’s built-in security key” that’ll walk you through the process.
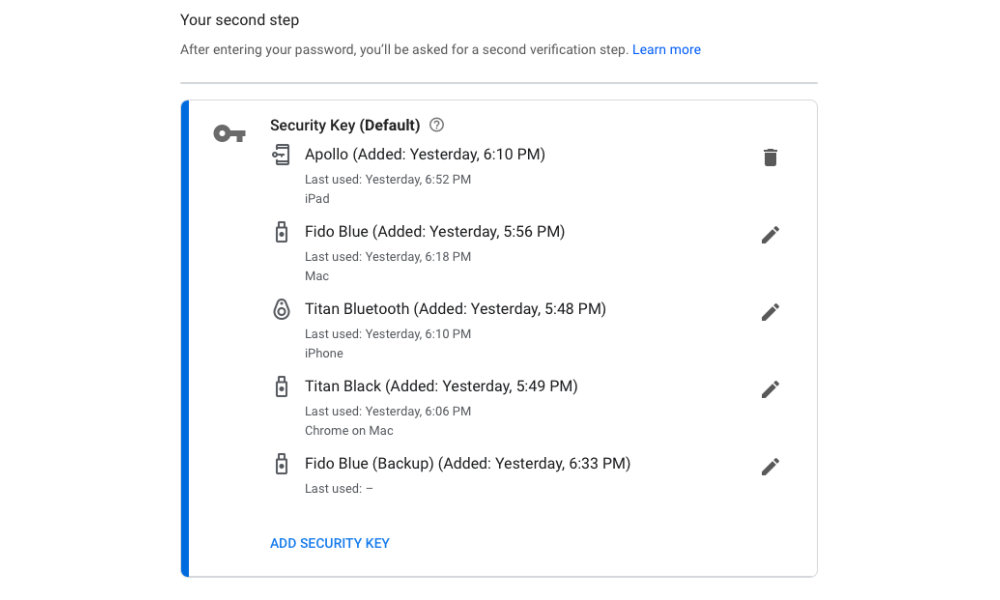
Once you’ve enabled this feature on your iPhone, it will automatically be added to the list of security keys found under “2-Step Verification” in your Google Account, which you can find by going to accounts.google.com and logging in and clicking on Security, 2-Step Verification.
If you haven’t set up any other physical security keys yet, you can add more from this screen as well, although you’ll have to order the physical keys from a third-party company like Yubico, which provides a variety of keys such as the YubiKey 5Ci that offers both Lightning and USB-C connectivity, or Google’s own Titan security keys, which offer a Bluetooth option as well.
Note that unless you’ve enrolled in Google’s Advanced Protectio Program, you can still use any of Google’s other two-factor authentication methods as alternatives to your physical keys, but once you’re confident that you can rely on the use of physical keys alone, you can also easily remove the other, less secure methods from the 2-Step Verification settings in your Google account.