Google Gets on Board with Apple’s SMS Security Proposal
 Credit: Jesse Hollington
Credit: Jesse Hollington
Toggle Dark Mode
Earlier this year, Apple’s engineers shared a clever new proposal that could help to make SMS two-factor authentication systems considerably more secure, and now it looks like the idea is gaining traction with other internet heavyweights, including receiving backing from Google and the Web Platform Incubator Community Group.
The idea was originally put forward back in January by Apple’s WebKit engineers — the group that develops the core technology used by Apple’s Safari web browser — and outlined a method whereby one-time codes delivered by SMS messages could be reliably associated with the services they actually came from.
If you’re unfamiliar with the term, two-factor authentication generally refers to the use of something in addition to your password to log in to an online service — usually, a numeric code sent to your phone or generated by an app. The feature is also sometimes referred to as “two-step verification,” but unless you’re a security expert, the two essentially mean the same thing in practical terms.
Chances are pretty good that you’ve used SMS two-factor authentication, even if you don’t know it by that name since it’s basically just a fancy term for the text messages that many online services send to your phone when they want you to confirm that it really is you trying to log in to something like your online banking system, or your Amazon or email account.
While some providers, including Apple, often use more sophisticated forms of two-factor authentication, in some cases even going so far as to use physical security keys instead of simple codes, all but the most secure systems often still allow for a fallback to receiving an SMS message if the other methods don’t work, in order to reduce the risk of users getting locked out of their accounts.
The Problem
The problem with using SMS messages is that they’re actually prone to a number of security vulnerabilities. First there’s the issue of SIM-jacking, which involves hackers going so far as to get your phone number transferred to a device that they own so that they can intercept any SMS messages that would normally go to you. Once a hacker can receive your SMS messages, they can basically get into any of your accounts that use your phone number as a second or backup authentication method, often simply by resetting your passwords.
Of course, this is a targeted attack that requires some effort on the part of the hacker to be going after you specifically, and there’s not much Apple or any other big tech company can really do about this except to prohibit the use of SMS entirely, as Google does with its Advanced Protection Program.
However, there are other more common and somewhat more insidious attacks that Apple’s proposal does address, including “phishing” attacks that attempt to get users to give up their passwords and other information by sending text messages that include bogus links, as well as “man-in-the-middle” (MitM) attacks where a hacker will try and get you to enter a legitimate two-factor code on a fake website.
Apple’s Solution
Apple’s WebKit engineers are proposing a new standard that would allow online services, mobile messaging apps, and web browsers to all communicate more effectively in order to determine if the SMS code should be trusted:
- Did the SMS message come from a legitimate site?
- Does the site where the code is being entered actually match the site that sent the message?
In Apple’s case, the new proposal would be a more secure extension of a feature that was introduced back in iOS 12 and macOS Mojave to allow SMS codes to be autofilled into Safari. While this is a huge time saver by saving users the trouble of finding the code and then copying it and pasting it in manually, there’s no way to tie that code to a specific site. In fact, in a worst-case scenario, a user could blithely autofill a security code into a malicious site, allowing it to be captured by a hacker.
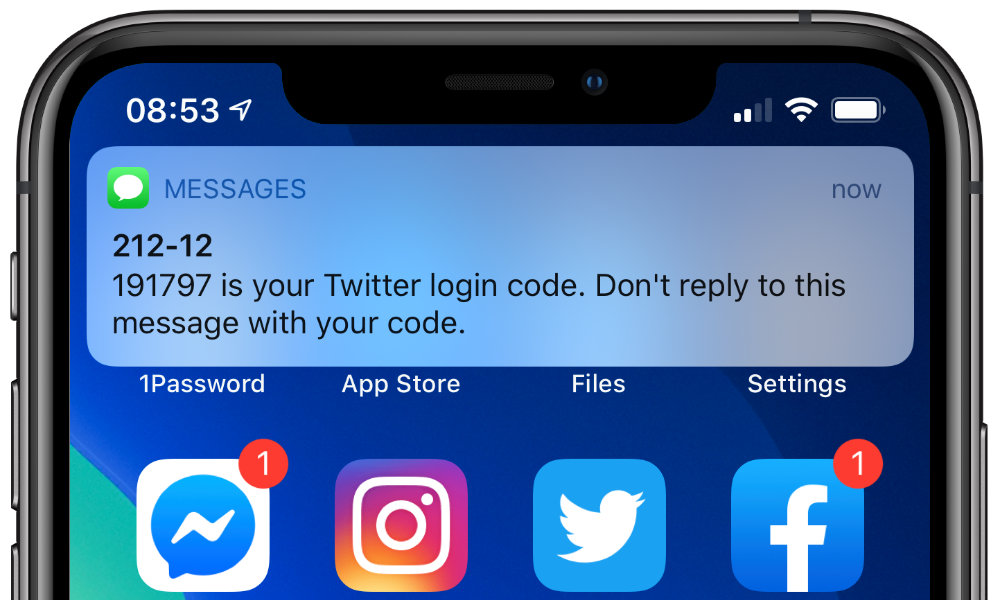
So needless to say, Apple has a bigger stake in making this process more secure, and to that end it has simply suggested that all SMS authentication messages use a standardized format that clearly identifies the website both in human-readable and machine-readable form.
747723 is your FooBar authentication code.
@foobar.com #747723
The machine-readable line would be read by the browser when polling the on-device messaging app (e.g. Safari and Messages on iOS or macOS devices), and the code would only be offered up for autofill if everything matched properly.
In addition, although the new solution still wouldn’t prevent a user from manually entering an OTP code onto a malicious site, Safari would be able to alert users if the site they’re on doesn’t actually match the one listed in the SMS message, strongly advising that they don’t proceed.
Moving Forward
Apple originally posted this proposal on GitHub, and now an update to the original post showed that the proposal has now reached the status of being an official Web Platform Incubator Community Group (WICG) specification draft, which is an important step in moving the proposal forward.
At this point, Google’s Chromium engineers have also signed on to throw their weight behind the proposal, although Firefox developer Mozilla still remains non-committal at this point. Getting widespread platform support will obviously be key to making this happen, and while online services would still need to format their SMS messages according to the proposed standard, they’re likely to adopt it rather quickly if all of the major browsers get on board, since it’s a relatively minor change for most services to make.
Apple and Google both acknowledge that the proposal doesn’t solve all of the risks associated with SMS delivery of one-time codes, and wherever possible, we continue to strongly recommend that you employ a more secure method for any high-security accounts, such as your online banking and your email account.






