Apple Officially Releases iOS 10.3.3 with 24 Major Security Fixes
Toggle Dark Mode
Apple on Wednesday officially released iOS 10.3.3 to the general public, concluding a testing period that lasted about nine weeks and consisted of six betas. The last update to iOS 10.3 was released on May 15, and that update similarly squashed as many as 23 bugs and other issues.
Among the more important changes is a fix for a major vulnerability that would have allowed attackers to execute code via an iOS device’s Wi-Fi chip. Other than that, iOS 10.3.3 doesn’t appear to contain any new features or outward-facing changes. Instead, it’s an incremental update focused on under-the-hood improvements, security enhancements and bug fixes.
The new update comes amidst a winding down of work on iOS 10 as Apple shifts its focus to the next-generation iOS 11, which is due for a rollout this fall. In fact, iOS 10.3.3 is likely to be one of the last updates to iOS 10, if not the last. Notably, iOS 10 is the last update that 32-bit iPhones and iPads will be able to download as iOS 11 will do away with support for
Notably, iOS 10 is the last update that 32-bit iPhones and iPads will be able to download as iOS 11 will do away with support for 32-bit architecture. With devices such as the iPhone 5 and iPhone 5c about to be left behind, it stands to reason that Apple tried to polish iOS 10’s last update as much as it possibly could.
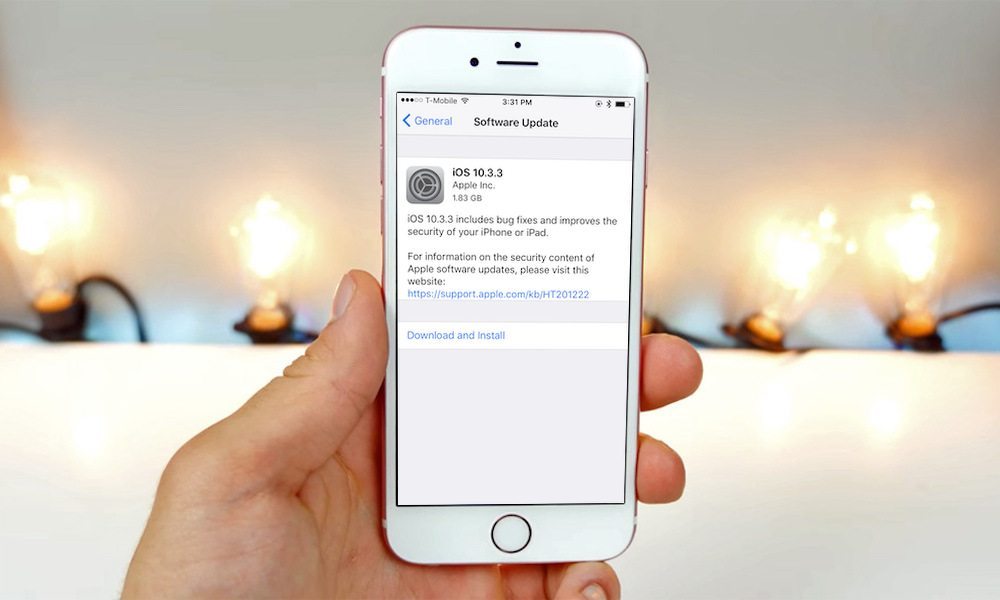
iOS 10.3.3 is currently available for the iPhone 5 and later, iPad 4th generation and later, and iPod touch 6th generation as an over-the-air update found under Settings > General > Software Update.
Alternatively, it’s available to download and install on an iOS device via iTunes on a Mac or PC.
List of iOS 10.3.3 Fixes
Contacts
- Impact: A remote attacker may be able to cause unexpected application termination or arbitrary code execution
- Description: A buffer overflow issue was addressed through improved memory handling.
CoreAudio
- Impact: Processing a maliciously crafted movie file may lead to arbitrary code execution
- Description: A memory corruption issue was addressed with improved bounds checking.
EventKitUI
- Impact: A remote attacker may cause an unexpected application termination
- Description: A resource exhaustion issue was addressed through improved input validation.
IOUSBFamily
- Impact: An application may be able to execute arbitrary code with kernel privileges
- Description: A memory corruption issue was addressed with improved memory handling.
Kernel
- Impact: An application may be able to execute arbitrary code with system privileges
- Description: A memory corruption issue was addressed with improved memory handling.
Kernel
- Impact: An application may be able to execute arbitrary code with kernel privileges
- Description: A memory corruption issue was addressed with improved memory handling.
Kernel
- Impact: An application may be able to read restricted memory
- Description: A validation issue was addressed with improved input sanitization.
libarchive
- Impact: Unpacking a maliciously crafted archive may lead to arbitrary code execution
- Description: A buffer overflow was addressed through improved bounds checking.
libxml2
- Impact: Parsing a maliciously crafted XML document may lead to disclosure of user information
- Description: An out-of-bounds read was addressed through improved bounds checking.
libxpc
- Impact: An application may be able to execute arbitrary code with system privileges
- Description: A memory corruption issue was addressed with improved memory handling.
Messages
- Impact: A remote attacker may cause an unexpected application termination
- Description: A memory consumption issue was addressed through improved memory handling.
Notifications
- Impact: Notifications may appear on the lock screen when disabled
- Description: A lock screen issue was addressed with improved state management.
Safari
- Impact: Visiting a malicious website may lead to address bar spoofing
- Description: An inconsistent user interface issue was addressed with improved state management.
Safari Printing
- Impact: Processing maliciously crafted web content may lead to an infinite number of print dialogs
- Description: An issue existed where a malicious or compromised website could show infinite print dialogs and make users believe their browser was locked. The issue was addressed through throttling of print dialogs.
Telephony
- Impact: An attacker in a privileged network position may be able to execute arbitrary code
- Description: A memory corruption issue was addressed with improved memory handling.
WebKit
- Impact: A malicious website may exfiltrate data cross-origin
- Description: Processing maliciously crafted web content may allow cross-origin data to be exfiltrated by using SVG filters to conduct a timing side-channel attack. This issue was addressed by not painting the cross-origin buffer into the frame that gets filtered.
WebKit
- Impact: Visiting a malicious website may lead to address bar spoofing
- Description: A state management issue was addressed with improved frame handling.
WebKit
- Impact: Processing maliciously crafted web content may lead to arbitrary code execution
- Description: Multiple memory corruption issues were addressed with improved memory handling.
WebKit
- Impact: Processing maliciously crafted web content with DOMParser may lead to cross site scripting
- Description: A logic issue existed in the handling of DOMParser. This issue was addressed with improved state management.
WebKit
- Impact: Processing maliciously crafted web content may lead to arbitrary code execution
- Description: Multiple memory corruption issues were addressed through improved memory handling.
WebKit
- Impact: An application may be able to read restricted memory
- Description: A memory initialization issue was addressed through improved memory handling.
WebKit Page Loading
- Impact: Processing maliciously crafted web content may lead to arbitrary code execution
- Description: Multiple memory corruption issues were addressed with improved memory handling.
WebKit Web Inspector
- Impact: Processing maliciously crafted web content may lead to arbitrary code execution
- Description: Multiple memory corruption issues were addressed with improved memory handling.
Wi-Fi
- Impact: An attacker within range may be able to execute arbitrary code on the Wi-Fi chip
- Description: A memory corruption issue was addressed with improved memory handling.






