iOS 10.3.2 Officially Released with 23 Bug Fixes
Toggle Dark Mode
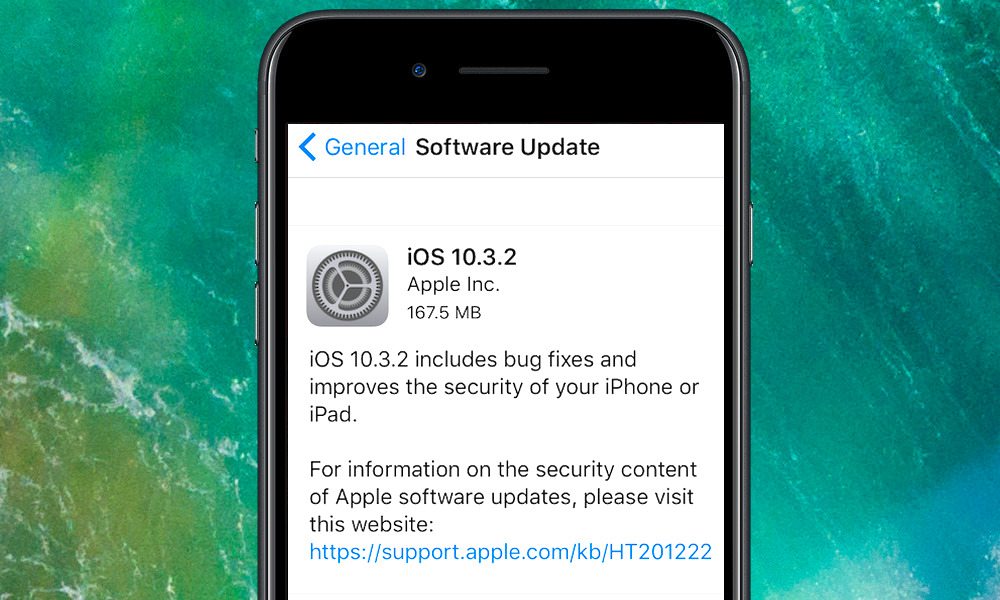
Apple has released the final version of iOS 10.3.2 to the public, after just about a month and a half of beta testing. Notably, the update fixes and patches a whopping 23 known issues and bugs.
Like the iOS 10.3.1 update before it, Apple’s newest OS firmware is an incremental update packed with under-the-hood bug fixes, security improvements and performance enhancing patches. No forward-facing changes or new features have been discovered so far, so it’s likely that the patch is just a security and bug fix update (but that makes it no less important). A full list of the included fixes is available below.
The new iOS update manages to squash a wide range of various bugs, including two bugs in iBooks — one of which would allow a malicious book to open websites without user permission. A similar bug in Safari would allow malicious websites to apply an application denial of service. The patch also fixes a Kernel bug, a Notifications issue, several SQLite bugs and a total of eight WebKit bugs, among several others.
It’s important to note that, with the security fix announcement, these bugs and exploits are now public knowledge. In turn, it’s definitely a good idea to update your device to iOS 10.3.2 as soon as possible to prevent attackers from using these now-patched vulnerabilities on iOS devices running older versions. iOS 10.3.2 can be installed on any iOS device that can run iOS 10 — which includes the following:
- iPhone 5 and newer
- Fourth-gen iPad and newer
- iPad mini 2 and newer
- All iPad Pro models
- Sixth-gen iPod Touch and newer
iOS 10.3.2 is currently available as an over-the-air update for the devices above. Alternatively, you can download and install the update via iTunes.
iOS 10.3.2 Security Fixes (list of 23)
- AVEVideoEncoder
Impact: An application may be able to gain kernel privileges. A memory corruption issue was addressed with improved memory handling.
- CoreAudio
Impact: An application may be able to read restricted memory. A validation issue was addressed with improved input sanitization.
- iBooks
Impact: A maliciously crafted book may open arbitrary websites without user permission. A URL handling issue was addressed through improved state management.
Impact: An application may be able to execute arbitrary code with root privileges. An issue existed within the path validation logic for symlinks. This issue was addressed through improved path sanitization.
- IOSurface
Impact: An application may be able to gain kernel privileges. A memory corruption issue was addressed with improved memory handling.
- Kernel
Impact: An application may be able to execute arbitrary code with kernel privileges. A race condition was addressed through improved locking.
Impact: An application may be able to read restricted memory. A validation issue was addressed with improved input sanitization.
- Notifications
Impact: An application may be able to cause a denial of service. A denial of service issue was addressed through improved memory handling.
- Safari
Impact: Visiting a maliciously crafted webpage may lead to an application denial of service. An issue in Safari’s history menu was addressed through improved memory handling.
- Security
Impact: Update to the certificate trust policy. A certificate validation issue existed in the handling of untrusted certificates. This issue was addressed through improved user handling of trust acceptance.
- SQLite
Impact: A maliciously crafted SQL query may lead to arbitrary code execution. A use after free issue was addressed through improved memory management.
Impact: A maliciously crafted SQL query may lead to arbitrary code execution. A buffer overflow issue was addressed through improved memory handling.
Impact: A maliciously crafted SQL query may lead to arbitrary code execution. A memory corruption issue was addressed with improved memory handling.
Impact: Processing maliciously crafted web content may lead to arbitrary code execution. Multiple memory corruption issues were addressed with improved input validation.
- TextInput
Impact: Parsing maliciously crafted data may lead to arbitrary code execution. A memory corruption issue was addressed with improved memory handling.
- WebKit
Impact: Processing maliciously crafted web content may lead to arbitrary code execution. Multiple memory corruption issues were addressed with improved memory handling.
Impact: Processing maliciously crafted web content may lead to universal cross site scripting. A logic issue existed in the handling of WebKit Editor commands. This issue was addressed with improved state management.
Impact: Processing maliciously crafted web content may lead to universal cross site scripting. A logic issue existed in the handling of WebKit container nodes. This issue was addressed with improved state management.
Impact: Processing maliciously crafted web content may lead to universal cross site scripting. A logic issue existed in the handling of pageshow events. This issue was addressed with improved state management.
Impact: Processing maliciously crafted web content may lead to universal cross site scripting. A logic issue existed in the handling of WebKit cached frames. This issue was addressed with improved state management.
Impact: Processing maliciously crafted web content may lead to arbitrary code execution. Multiple memory corruption issues with addressed through improved memory handling.
Impact: Processing maliciously crafted web content may lead to universal cross site scripting. A logic issue existed in frame loading. This issue was addressed with improved state management.
-
WebKit Web Inspector
Impact: An application may be able to execute unsigned code. A memory corruption issue was addressed with improved memory handling.






