Apple Embraces Passkey Portability in iOS 26
Toggle Dark Mode
The Passwords app doesn’t appear to be getting too many visible changes in this year’s iOS 26 and macOS Tahoe releases (other than the Liquid Glass treatment, of course). However, it is gaining one essential new capability under the hood: the ability to seamlessly move passkeys to and from other platforms.
Over the past few years, Passkeys have become a simple and secure alternative to traditional passwords. Many websites, including Apple’s iCloud and mainstream services like Gmail, have already adopted passkeys, eliminating the need to fuss with passwords or even usernames in some cases.
Sadly, the most significant advantage of passkeys is also their greatest weakness. These credentials are stored securely in password managers, often accessible only using biometric authentication like Face ID or Touch ID; however, the standard also prevents passkeys from being exported in the traditional manner, since a text-based file containing your passkeys would risk compromising their security.
That creates no small amount of lock-in among password managers, and some even believe this is by design. Whether you choose to use Apple’s new Passwords app or a third-party password manager like 1Password, your passkeys end up stuck in whatever app you used to create them.
Although this lack of portability for your passkeys isn’t serious since most services let you generate multiple passkeys for different devices and password managers, it’s still far from ideal. A user who has all their passkeys stored in 1Password and wants to switch to Apple Passwords would need to visit each site manually and manually generate a new passkey using Apple’s app. That’s not only time-consuming, but it also risks leaving a few behind if you’re not careful.
The issue is more complex than the cynical take that software companies are trying to lock their users into their password managers. Passkeys are a standard developed by the FIDO Alliance, which didn’t provide a way for exchanging passkeys between platforms until last year. In October, the FIDO Alliance finally published a draft spec for this, opening up a secure way to move passkeys between platforms using a fully encrypted format that doesn’t risk exposing your passkeys in the process.
While companies like 1Password and Dashlane committed to adopting the spec, Apple may be getting there first. During a WWDC25 developer presentation on What’s new in passkeys, Apple engineer Andrew Abosh revealed how the Passwords app will allow users to import and export passkeys securely.
People own their credentials and should have the flexibility to manage them where they choose. That’s why I’m happy to let you know, passkeys can now be transferred securely between participating credential manager apps on iOS, iPadOS, macOS, and visionOS 26. This gives people more control over their data and the choice of which credential manager they use.
Andrew Abosh, Authentication Experience Engineer
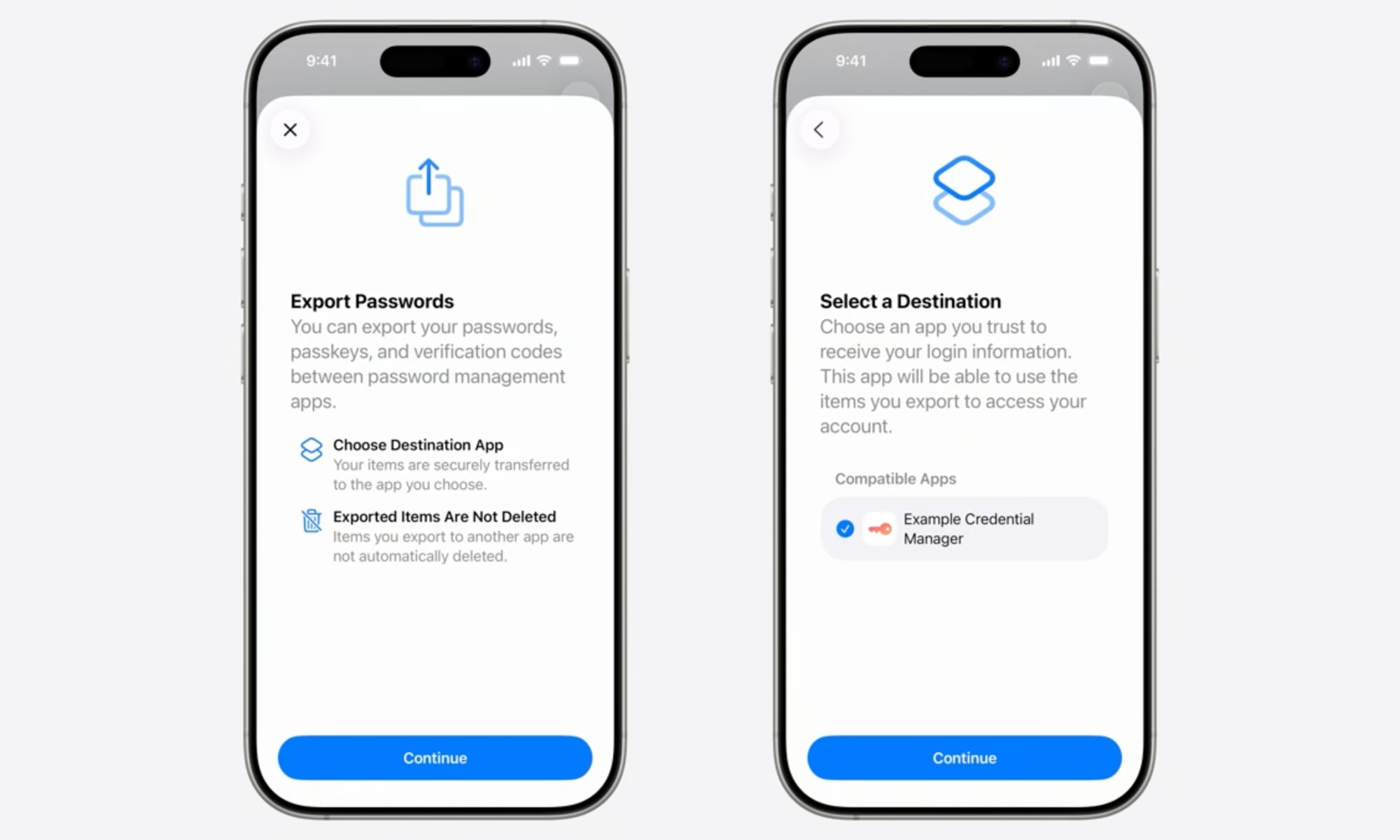
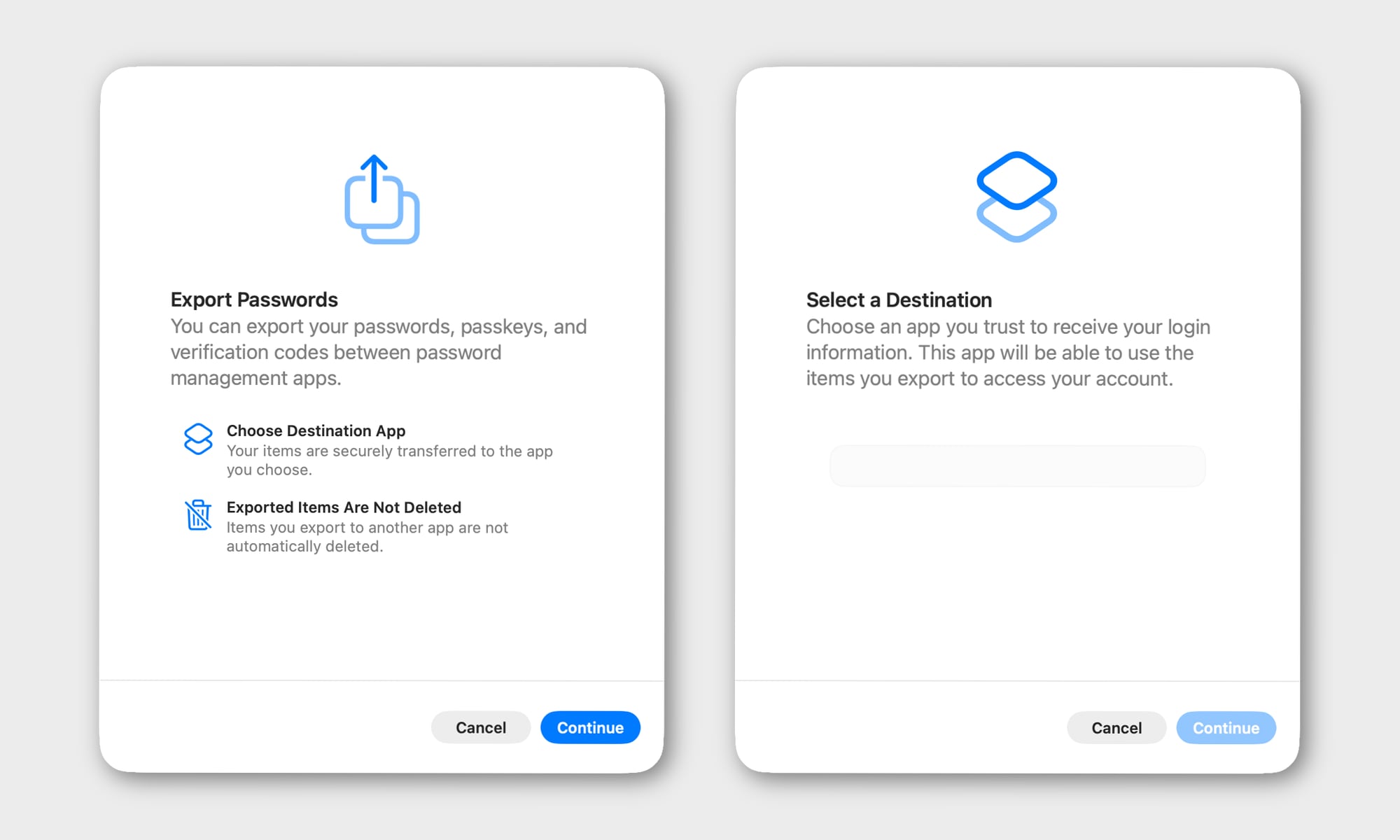
Abosh explained how the process is “fundamentally different” from traditional credential export methods. It’s not just a matter of dumping passkeys to an unencrypted CSV or JSON file that can be manually imported into another app. Instead, the transfer process occurs directly between participating credential manager apps and can only be done after the user explicitly authorizes it using Face ID.
“No insecure files are created on disk, eliminating the risk of credential leaks from exported files,” Abosh said, adding, “It’s a modern, secure way to move credentials.” Apps and websites that use passkeys also don’t need to participate in the process, as the full passkeys are transferred to the new password manager, just like a password would be, only much more securely.
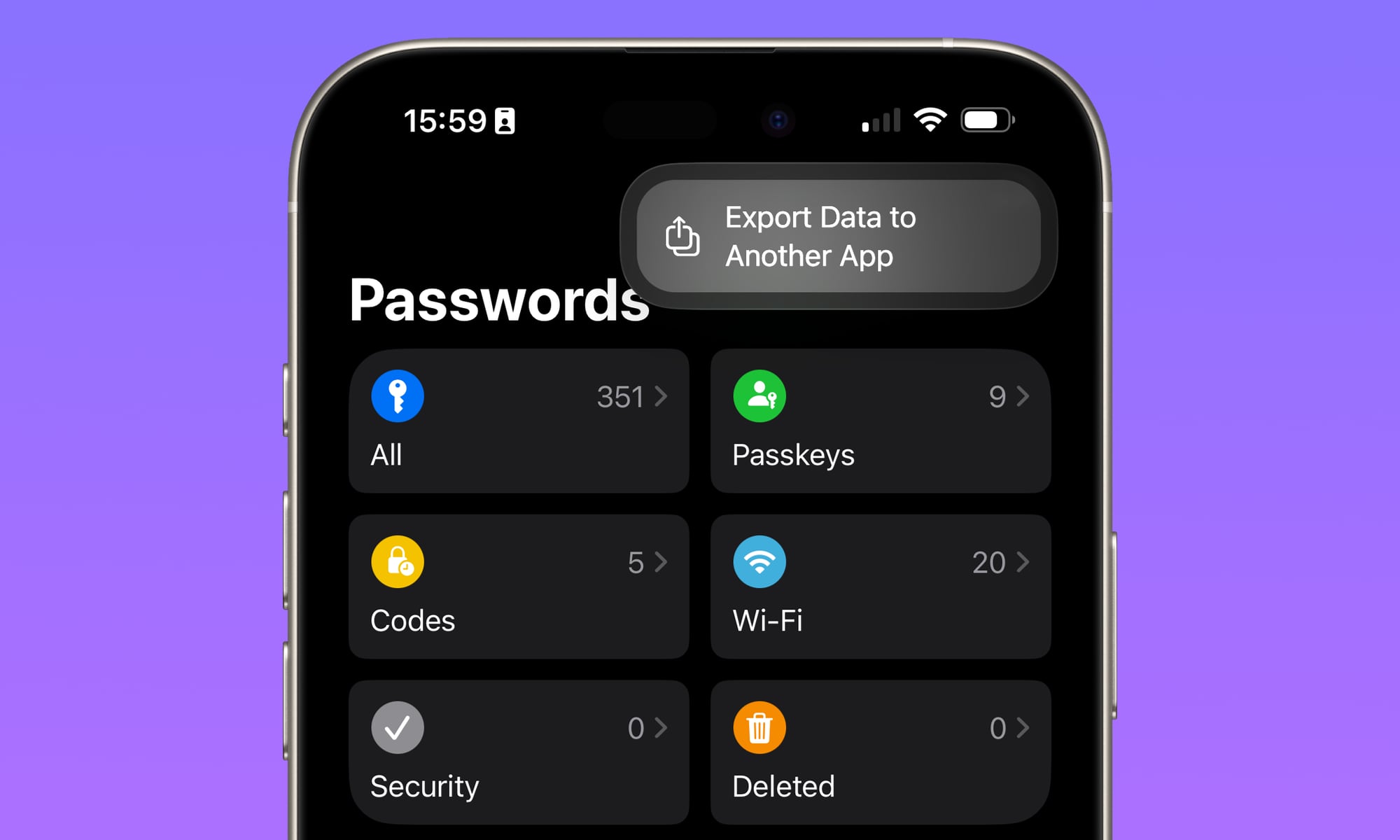
The new passkey export features are already up and running in the initial iOS 26, iPadOS 26, and macOS Tahoe developer betas. However, your passkeys have nowhere to go yet since this is an app-to-app transfer process. Initiating the export on an iPhone or iPad prompts you to “Install another app to receive your data,” while macOS Tahoe lets you start the process and then prompts you to “Select a Destination” from a blank list.
Still, it’s great to see Apple getting ahead of this with a sort of “if-you-build-it-they-will-come” approach. As Abosh notes, this uses the FIDO Alliance standard, and others like 1Password that have already committed to supporting this now have an on-ramp into Apple Passwords. Hopefully, we’ll have some apps ready to go onto this list once Apple publicly releases its operating system updates this fall.