Can Law Enforcement Hack Your iPhone?
 Credit: ink drop / Adobe Stock
Credit: ink drop / Adobe Stock
Toggle Dark Mode
Ever wonder if law enforcement can access your iPhone without a passcode, Face ID, or Touch ID? The short answer is yes, but it’s not that simple.
A special device is required and it comes with quite the price tag. The device is called GrayKey and is manufactured by Grayshift/Magnet Forensics. GrayKey’s existence was never a secret. However, details on how it works and how much it costs weren’t readily apparent. Now they are.
What is GrayKey and What Does it Do?
Fairfield Township in Butler County, Ohio, recently spilled the beans on GrayKey in a resolution approving the purchase of one of the boxes for its police department. In a memo proposing the purchase, day shift sergeant Brandon McCroskey explains the device thusly:
Most modern cellphone downloading technology available to law enforcement today…Specifically, Gray Shift allows investigators to bypass passcode obstructions to gain access to devices otherwise would be impossible to do so on other platforms. Their technology also allows unencrypting some of the data within cellphones, thus allowing investigators to see all the phone’s contents. Gray Shift also allows geo-location services to pull from multiple sources in the phone’s data. Simply said, it allows the investigator to find where a person was at a given time, and their platform places all the information into a final report for evidentiary and prosecutorial purposes.” Brandon McCroskey, Day Shift Sergeant, Fairfield Township Police Department
The proposal also includes a product brochure and quote from Grayshift (which has since become part of Magnet Forensics) that claims GrayKey is capable of providing same-day access for both iOS and Android devices, often in less than one hour, regardless of the device’s state.
There also doesn’t appear to be a limit to the data GrayKey can extract. This includes pictures, videos, chat histories, internet usage data, and deleted data. GrayKey is a physical device paired with a web interface that requires “no special training” to use.
The Fairfield proposal is from May 2023, so it doesn’t mention Apple’s latest devices and software. However, Magnetic Forensics confirmed in December that GrayKey supports “consent-based” extractions for both iOS 17 and the iPhone 15, allowing it to pull a complete set of data from any iPhone where the passcode is known. However, it only gained full support for bypassing the passcode on iOS 17 devices last month.
How Much Does GrayKey Cost?
Fairfield Township Police Department paid $14,169 for the first year of GrayKey, which included $550 for one GrayKey device and $10,995 for the “Essential” license which includes unlimited data extractions where a passcode is known (“consent” extractions), and 30 extractions where bypassing the passcode is necessary.
Additional extractions start in bundles of 5 for $3,845 ($769 per extraction) through 75 for $17,925 ($239 per extraction). This seems like quite a bargain for the speed and efficiency it provides investigators (if they have a search warrant, of course).
There’s also a $300 annual fee per user to train, certify, and re-certify them as GrayKey Operators, plus a $1,349 licensing fee for Magnet’s ArtifactIQ Pro forensic analysis platform.
Fortunately, Grayshift goes to great lengths to ensure its technology doesn’t fall into the hands of bad actors. In a 2022 letter to the FCC (Federal Communications Commission), Grayshift’s CFO wrote: “GrayKey is a specialized product that is only available for use by verified law enforcement or government agencies; and it is not made available for use by the general public. For every account request from a potential customer, Grayshift undertakes a rigorous, risk-averse validation process to confirm that each originated from a valid law enforcement agency located in a supported country.“
While it’s obvious GrayKey plays a crucial role in legal investigations, its use underscores the ongoing battle between tech companies focused on user privacy and encryption (like Apple) and law enforcement agencies seeking access to encrypted data for legal and security reasons.
The use of GrayKey has rightfully sparked debates around privacy, security, and legal ethics. To what extent should authorities be able to access private digital data? What safeguards should be in place to protect civil liberties?
Moreover, GrayKey’s existence begs the question of how to regulate device manufacturers like Apple, which continuously develops and updates security measures to protect users, and entities like Magnet Forensics, whose entire business model is based on developing ways to bypass these security features.
How Well Does GrayKey Work?
While Magnet Forensics makes it seem like it’s relatively easy and inexpensive for law enforcement to gain full access to your iPhone, the situation is a bit more nuanced than its marketing department would like you to believe.
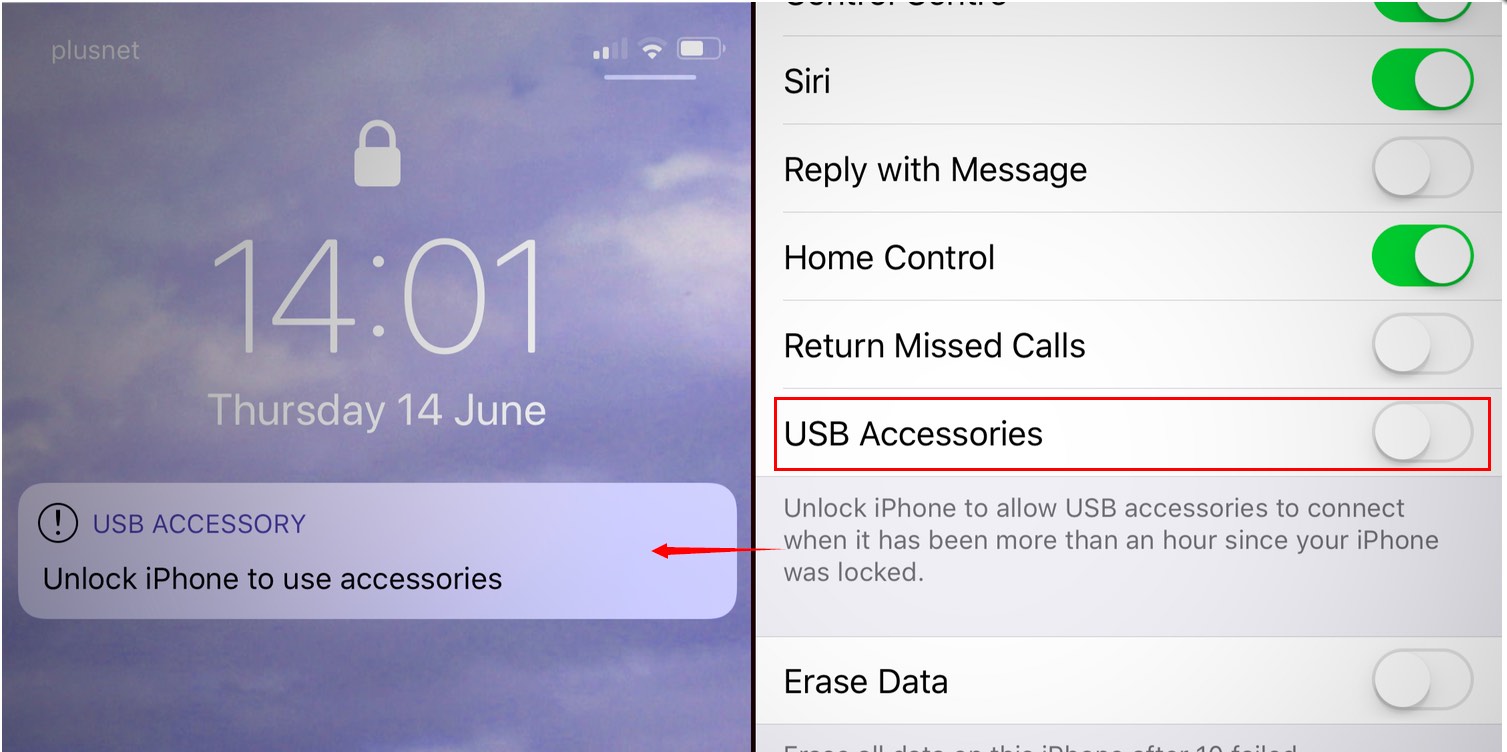
Firstly, since GrayKey requires a physical connection to an iPhone via its Lightning or USB-C port, it can only be used on iPhones that have been seized by law enforcement and taken to a forensics lab. Apple introduced a USB Restricted mode in iOS 11.4 to help combat these types of hacks, shutting down data access to the physical port when an iPhone has been locked for more than an hour. Once that time has passed, the iPhone will refuse to communicate with anything over its USB or Lightning port.
No one has yet figured out a way to bypass this lockdown, but several workarounds have been found to prevent it from engaging in the first place. Not the least of these is simply connecting the iPhone to GrayKey before that time elapses. Magnet Forensics also recommends connecting a “delay dongle” as soon as an iPhone is seized by law enforcement to prevent the timer from kicking in until the iPhone can be hooked up to a GrayKey box.
Secondly, GrayKey can’t magically break the iPhone’s encryption; instead, it relies on two key techniques: an AFU (After First Unlock) method to access data that’s left unencrypted in memory during normal use and a brute force attack that bypasses the standard passcode lockout features to try every possible password combination and unlock the iPhone normally.
The AFU method can reveal a surprising amount of data, including the content of text messages, browsing history, stored files, and much more. However, as the name suggests, it only works if the iPhone has been unlocked at least once since it was powered on; powering down or restarting your iPhone will negate this as long as you don’t unlock it after it reboots, leaving brute force as the only method available to GrayKey.
It will only take investigators an average of seven minutes to get into an iPhone with a four-digit passcode using the brute force method, but that increases exponentially the more digits are involved; a six-digit numeric passcode will take an average of 11 hours, while eight digits could take up to three months.
Choose an alphanumeric password and the time required for someone to brute-force their way into your iPhone increases by a much greater order of magnitude. A random six-character password will take an average of 72 years to guess. Increase that to eight characters, and the number goes up to 288,000 years. This all assumes you’re using entirely random passwords, as it takes far less time to go through a few hundred thousand words in a dictionary than it does to try over two billion combinations of six letters and numbers.
Lastly, keeping your iPhone updated to the latest iOS version will often be enough to prevent these attacks. All bets are off if you’re running an older version of iOS, but the constant cat-and-mouse game between Apple and digital forensics researchers means that keeping your iPhone on the latest iOS release makes it far less likely to be vulnerable to tools like GrayKey since Apple is constantly patching the security flaws that these devices exploit to do their thing. Consider that iOS 17 was released to the public on September 18, 2023 but GrayKey didn’t gain full support for breaking into an iPhone running iOS 17 until March 22, 2024 — and it’s still not clear if its method will work when iOS 17.5 is released next month.
However, considering the costs and complexities involved, no law enforcement agency is using GrayKey casually. If your iPhone has become of sufficient interest for law enforcement officials to detain it for further forensic analysis, they’ll have no problem leaving it plugged into a charger somewhere for however long it takes for Magnet Forensics to release an update that will add compatibility with whatever iOS version it’s running today.