Vulnerability in Mac Gatekeeper Has Been Exploited – Here’s How to Protect Yourself
 Credit: iMore
Credit: iMore
Toggle Dark Mode
Gatekeeper is one of many macOS features that may have lulled Mac users into a false sense of security. Case in point: a vulnerability within Gatekeeper has now been exploited in the wild.
In other words, there’s a publicly known method to bypass the Gatekeeper feature to get malicious software onto your Mac — and that method has been actively used by someone. Here’s what you should know.
About the Gatekeeper Vulnerability
We first reported on the vulnerability last month when security researcher Filippo Cavallarin discovered and publicized the flaw within Gatekeeper.
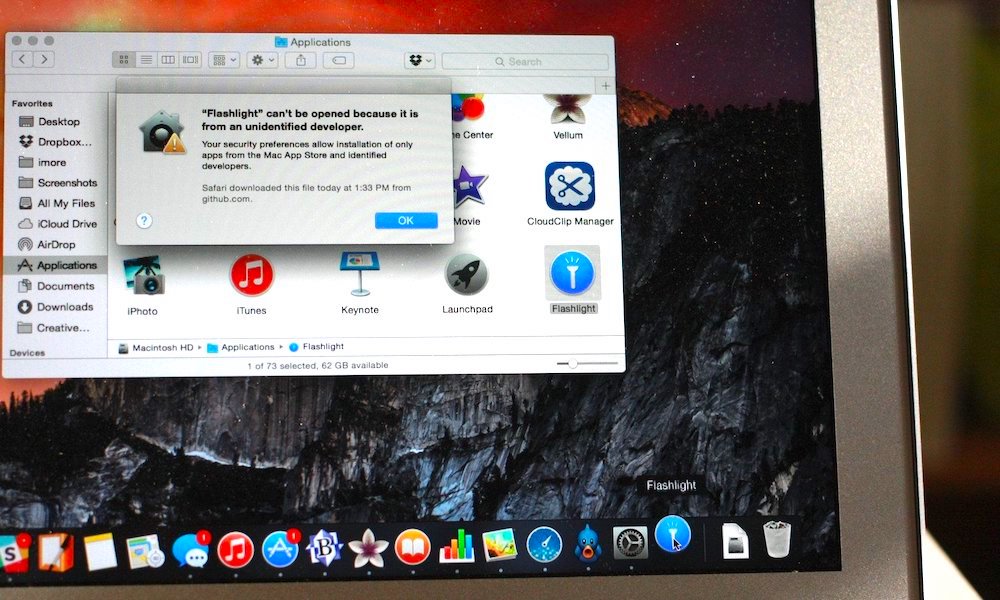
Gatekeeper, of course, is a macOS security feature that flags apps from untrusted developers. To run these untrusted and unsigned apps, users must explicitly give the go-ahead.
Essentially, the vulnerability is a flaw in how Gatekeeper is designed. By default, the security feature marks external drives and shared network folders as “safe.” Once a user approves them via Gatekeeper, any app within those safe locations can run without having to go through Gatekeeper again.
This basically means that a single legitimate app that a user has approved can be used as an attack vector to install malware on your machine. An attacker could trick a user into mounting a network share drive and then launch the attack.
Gatekeeper Exploitation in the Wild
While the Gatekeeper flaw may be dangerous, there’s now new evidence to suggest that the vulnerability has been exploited in the wild.
The vulnerability appears to have been leveraged in a “test” by an adware company in preparation for malware distribution, Cybersecurity firm Intego reported on its blog this week.
More specifically, the exploitation appears to have been a test to determine whether the exploit would work with disk image files — those .dmg files that you use to install Mac software.
Intego notes that there’s
The cybersecurity firm said it reported the Developer ID used in the test to Apple so the company can revoke it. It isn’t clear when or if Apple will actually do so, however.
Similarly, Apple has not addressed the underlying flaw. Cavallarin gave the company 90 days before he disclosed the vulnerability. But on his blog, he said that the company failed to patch it and stopped replying to his emails.
How to Protect Yourself
Currently, there does not appear to be an easy way for most consumers to stop an attacker from leveraging this exploit. Intego notes a few options on its blog, but none of them are really that suitable for the average Mac user.
- If you suspect an app you’ve allowed through Gatekeeper of any malicious activities, the best case scenario is to contact Apple and have them revoke the app maker’s developer ID certificate.
- Prevention being better than cure, the best way to protect yourself is to avoid downloading apps from random places on the internet. Stick to the Mac App Store or developers that you’re absolutely sure you can trust.






