New Security Flaw Reveals Your Mac’s Gatekeeper May Not Be Fully Protecting You
 Credit: Lewis Ngugi
Credit: Lewis Ngugi
Toggle Dark Mode
A new security flaw has been found in macOS that could allow malicious apps to bypass Apple’s built-in “Gatekeeper” security feature. Most significantly, this bug affects even most recent 10.14.5 update that was released earlier this month to address the ZombieLoad Intel hardware vulnerability.
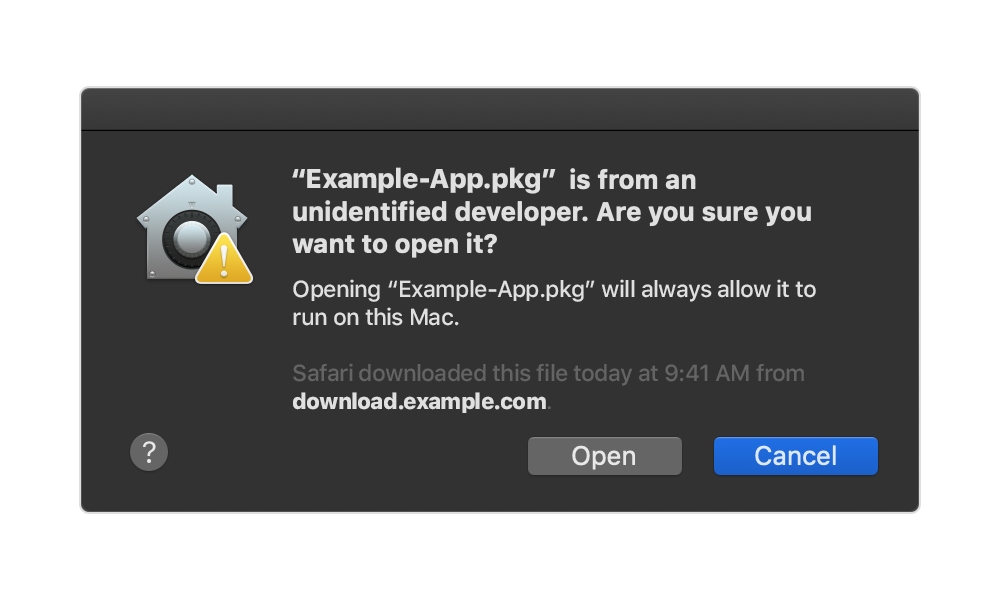
Gatekeeper is a security feature that was introduced back in 2012 in OS X Mountain Lion designed to flag apps from untrusted developers, preventing them from running without explicit user permission. Registered and trusted Apple developers are allowed to digitally sign their apps, and Gatekeeper kicks in when the user tries to run an unsigned app that they’ve downloaded from outside of the Mac App Store.
However, it seems that a loophole has been discovered in the Gatekeeper process. Security researcher Filippo Cavallarin discovered the flaw, publicizing it on his blog, as reported by 9to5Mac.
The problem is in the way that Apple has designed the feature, which considers external drives and network shares to be “safe locations” to run unsigned apps from. While the reasons for this decision on Apple’s part are unclear, it’s likely designed to allow users in business and school environments to easily open shared apps without having to jump through extra and possibly confusing, hoops.
Unfortunately, it’s relatively simple for a malicious app to trick a user into mounting a network share drive — even from over the internet — subsequently allowing anything in that folder to be run without consulting the Gatekeeper process.
Cavallarin offers some additional technical details and examples for ways in which this exploit could be taken advantage of by bad actors, highlighting not only the Gatekeeper limitations concerning network shares, but also the default behaviour of macOS to automatically mount network shares via a special path.
As Cavallarin explains, a ZIP archive could contain a special file that links to a network location (known as a “symbolic link” or “symlink”). This special file could be crafted in such a way as to make the user think that they need to click on it for some legitimate reason, which would then take them to a network share that’s completely trusted by Gatekeeper, but controlled by the attacker. Cavallarin even provides specific steps on his blog that can be used to reproduce the exploit with minimal effort.
Both the automatic mounting of network shares and the ability to include “symlinks” in ZIP files are legitimate features of macOS, Cavallarin notes, but because of the way Gatekeeper automatically trusts ANY network share, they open up very real possibilities for malicious software to get installed onto a user’s computer without them realizing it.
Cavallarin also provides a video of the exploit in action, showing how it could even be used to provide an attacker with full remote access to the target computer by tricking the user into clicking on an app that’s disguised as a folder of important PDF documents.
According to Cavallarin’s post, he contacted Apple on February 22 to make them aware of the bug, which Apple said was supposed to be addressed on May 15th — presumably as part of macOS 10.14.5 and the related ZombieLoad security updates for Sierra and High Sierra. However, Cavallarin notes that “Apple started dropping [his] emails” and since he had given Apple a 90-day disclosure deadline, he decided to make the information public after he found that it still hadn’t been addressed in macOS 10.14.5.
Until Apple addresses this issue, we’d recommend extreme caution when downloading apps outside of the Mac App Store, especially apps contained in ZIP files and/or those that look like they may require you to click on unusual files, folders, or other links. Cavallarin also suggests disabling the macOS automount feature as a “possible workaround” to increase security, although this requires editing a secure file through the macOS Terminal app, so it’s only recommended for advanced users who understand how to edit files as the root user.