Pegasus Spyware Remains a Threat as Researchers Discover New ‘Zero-Click’ Attacks
 Credit: usfaridas / Shutterstock
Credit: usfaridas / Shutterstock
Toggle Dark Mode
The notorious Pegasus spyware is back in the news this week as a team of security researchers highlights a new “triple threat” of exploits used by the malware to conduct targeted cyberattacks throughout 2022.
Pegasus is an “industrial” spyware tool that was developed by Israeli technology firm NSO Group, ostensibly purely for use in counterterrorism efforts by governments. While Pegasus has been around since 2014, it made headlines two years ago when a forensic analysis conducted by Amnesty International and the University of Toronto’s Citizen Lab revealed the spyware was responsible for “widespread, persistent and ongoing unlawful surveillance and human rights abuses,” having been used to target and spy on dozens of “human rights defenders (HRDs) and journalists around the world.”
In a rare move, Apple subsequently launched a massive lawsuit against NSO Group, describing the company and those who work for it as “amoral 21st century mercenaries who have created highly sophisticated cyber-surveillance machinery that invites routine and flagrant abuse.” It also set up a fund for organizations like Citizen Lab and Amnesty Tech to assist with their cyber surveillance research and advocacy, seeding it with an initial $10 million and promising to add to the pot from any damages that arise from the lawsuit against NSO Group.
While Apple hopes to sue NSO Group out of existence, sadly, courts move slowly, and in the meantime, Pegasus continues to be used for nefarious purposes. Things got quieter following a mid-2021 report that the Pegasus spyware had targeted U.S. State Department officials. However, a new report by ?Citizen Lab? reveals that Pegasus has still been active but has been flying under the radar for the past year or so.
A Zero-Click Triple Threat
Specifically, researchers at Citizen Lab have discovered three new “zero-click exploit chains” used by Pegasus throughout 2022 to ramp up cyber attacks against human rights defenders, journalists, and other “civil society targets” worldwide.
Far from being used for its stated purpose of counterterrorism and fighting human trafficking and other organized crime, Pegasus appears to have instead become a tool of oppressive regimes. The latest Pegasus targets identified by Citizen Labs involve two human rights defenders from Centro PRODH, an organization in Mexico that represents victims of military abuses such as extrajudicial killings and forced disappearances.
Pegasus infections among members of Centro PRODH go back to at least 2015, as Citizen Lab explains in its report:
“One widely publicized case of disappearances relevant to this case of spyware infection occurred in September 2015 when a group of 43 students at a teacher training college were forcibly disappeared after traveling to Iguala to protest teacher hiring practices. Their subsequent disappearance is referred to as the “Iguala mass kidnapping,” or simply the “Ayotzinapa case.” In 2017, we reported that three members of the Mexican legal aid and human rights organization, Centro PRODH, were targeted with Pegasus spyware, along with investigators involved in the Ayotzinapa case. At the time of targeting, which was in 2016, Centro PRODH was representing families of the disappeared students.”
However, as the cat-and-mouse game between Apple and Pegasus continues, NSO Group has had to get more creative in finding new exploits, including so-called “zero-click” vulnerabilities where Pegasus can install itself and begin spying on an iPhone without requiring any interaction from the user.
Citizen Lab found three of these dangerous exploits on two iPhones running iOS 15 and iOS 16, used by Centro PRODH staffers. One belonged to Jorge Santiago Aguirre Espinosa, the Director of Centro PRODH, who had also been identified as a Pegasus target in 2017. The other belonged to María Luisa Aguilar Rodríguez, International Coordinator at Centro PRODH. Pegasus was reportedly active on Mr. Aguirre’s device on June 22, 2022, the same date that Mexico’s truth commission held a ceremony launching its investigation into human rights abuses by the Mexican army. Ms. Rodríguez’s phone was infected the next day and then subsequently infected on two other occasions in September 2022.
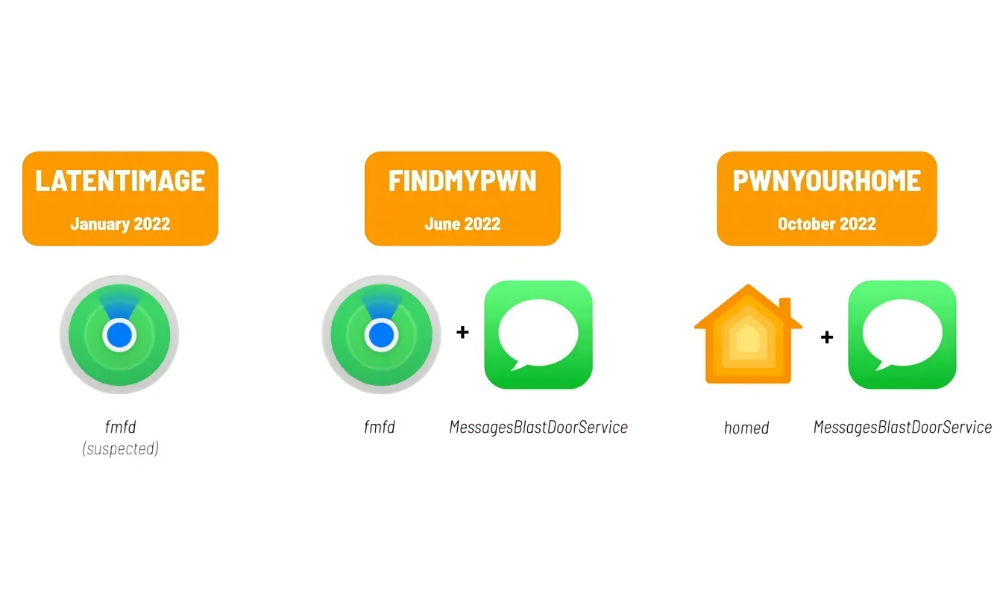
The three exploits, dubbed LATENTIMAGE, FINDMYPWN, and PWNYOURHOME, all take advantage of security vulnerabilities in iOS 15 and iOS 16, specifically flaws in the code underlying Apple’s Find My, Messages, and Home features. Most of the attacks were found on devices running iOS 15 since that was current at the time, although PWNYOURHOME was deployable against iOS 16.0.3.
Thankfully, Citizen Lab has not seen any cases of these on devices running iOS 16.1 or newer. This suggests that Apple has patched these flaws and in the case of PWNYOURHOME, researchers shared “forensic artifacts” that helped Apple shore things up with HomeKit in iOS 16.3.1.
Unfortunately, it’s probably only a matter of time before NSO Group finds new ones that can be exploited. That’s why it’s always a good idea to keep your iPhone updated to the very latest iOS version — especially when Apple’s release notes indicate patches for vulnerabilities that have been “actively exploited.”
Using iOS 16’s Lockdown Mode
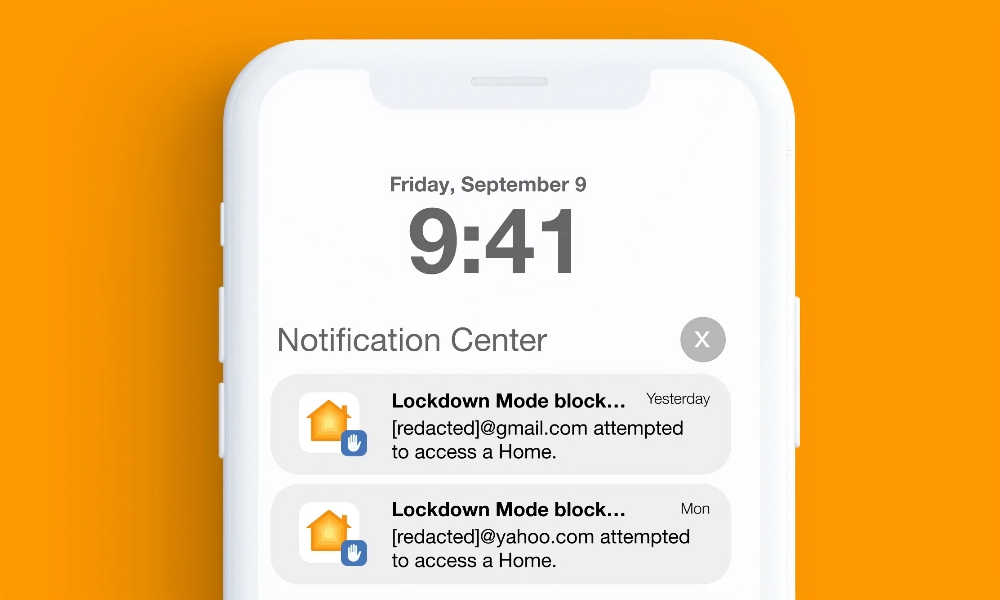
Citizen Lab researchers also noted that PWNYOURHOME triggered warnings on devices where Apple’s new high-security Lockdown Mode had been enabled. Initially, the exploit triggered notifications of an unknown user attempting to access a Home, demonstrating that Lockdown Mode works as designed.
Although later versions of the exploit seem to have found a way to block the notifications, researchers found no evidence it could actually bypass Lockdown Mode — merely silence the notifications that alerted a user to the unauthorized access attempts.
Despite the insidious nature of Pegasus, the good news for most of us is that it remains a targeted attack. Further, the tools developed by NSO Group are only sold to governments, which is why it’s referred to as “state-sponsored spyware.” Of course, not all government agencies are ethical when it comes to surveillance. However, it’s still safe to say that you’re unlikely to encounter Pegasus unless you’re involved in the sort of work that might garner the attention of a corrupt regime.
For those who are “high-risk” users, that’s where Apple’s Lockdown Mode comes in. While it involves too many usability compromises for most ordinary folks, Citizen Lab highly encourages it for anybody who thinks they may be at risk of being targeted by Pegasus or other state-sponsored spyware.