5 Things You Should Know about ‘ZombieLoad’, the Latest Major Mac Security Vulnerability
 Credit: Marcos Silva / Shutterstock
Credit: Marcos Silva / Shutterstock
A serious new vulnerability has been discovered in Intel chips dating back to 2011 — the same chips used by all of Apple's Macs over the past 7–8 years. While the significance of this latest flaw will undoubtedly give rise to a lot of media coverage, which might get confusing, there are really only a few simple things you need to know in order to protect yourself. Read on to learn the most important points about ZombieLoad and what you can do to ensure that your computers and data are fully protected.
What Is ZombieLoad?
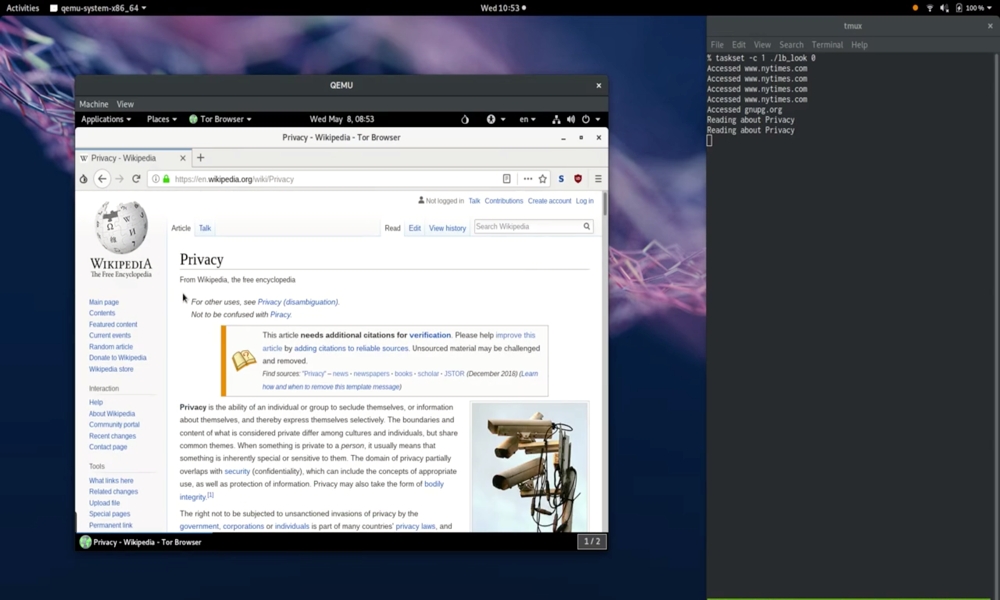
ZombieLoad is the latest flaw found in Intel's processor architecture. It's very similar in nature to the Meltdown and Spectre vulnerabilities that were discovered in early 2018, which could allow hackers to access extremely sensitive data like passwords and encryption keys from any affected computer.
ZombieLoad is not a software flaw, but rather something that can be exploited in the architecture of pretty much all modern computers. The flaw was named ZombieLoad in reference to the way it is exploited — by loading a large set of "zombie" data into the processor — more than it can normally handle — the processor calls upon additional resources to handle the load, which can then result in data leaking in from other apps. Security researchers who discovered the flaw have also prepared a very detailed technical paper on the flaw for those who are interested in the scientific and engineering aspects.
For the rest of us, however, the main takeaway is that this is a very serious vulnerability that shouldn't be ignored.
Who's Affected?
This flaw affects every Mac — MacBooks, iMacs, Mac minis, and even the Mac Pro — made since around the time in 2011 when Apple would have switched to the first generation of flawed CPUs.
The problem isn't exclusive to Macs, either — it impacts almost anything built with any Intel CPU inside that was made in 2011 or later, whether it's running Windows, Linux, macOS, or even an embedded specialized operating system. Note that cloud servers aren't immune either.
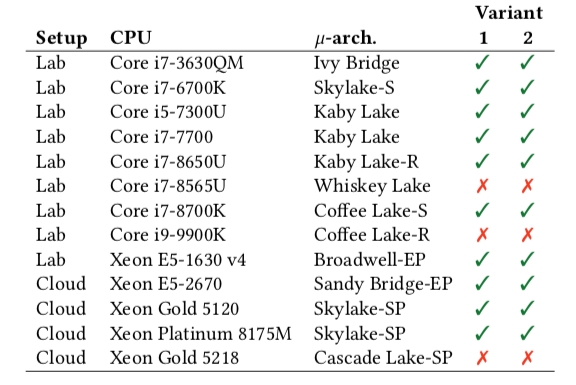
Security researchers specifically tested a wide variety of CPUs and found almost all of them were vulnerable, with only three relatively uncommon exceptions: the Whiskey Lake, Coffee Lake-R, and Cascade Lake-SP microarchitectures appeared to be immune to the variants of ZombieLoad tested by researchers, but it's much safer to assume that your Mac will be vulnerable to ZombieLoad. Apple never used Whiskey Lake and Cascade Lake architectures at all, and only two of the very most recent iMacs released a few weeks ago — the Core i9 and the Core i5 3.7GHz models — incorporate the Coffee Lake-R architecture; the others use Coffee Lake-S, which has been proven to be vulnerable to both variants of ZombieLoad.
Since this flaw only affects Intel CPUs, however, you don't need to worry about your other Apple devices. Apple's iPhone, iPad, iPod, Apple TV, and Apple Watch all use Appel's own ARM-based chips, and the flaw exists only in the CPU; ancillary Intel chips like the modem chips found in some iPhone models are not affected.
Why Is It Dangerous?
Put simply, ZombieLoad allows a hacker to access any data that could be in the memory of your computer, from any running app. Think of it as a way to break down the walls that normally exist between apps using the system's main processor, so a malicious app running on your Mac could read anything that any other app is doing or storing in memory, including extremely sensitive data like passwords and cryptographic keys.
Researchers showed a proof-of-concept video that demonstrates how the flaw can be exploited to provide real-time tracking of which websites the user is visiting, which isn't a far stretch from pulling in passwords and security tokens that could be used to access online email and banking accounts.
To be clear, this exploit still requires an app to be running on your actual computer — it's not exactly a "drive-by" vulnerability that would allow somebody to remotely take control of your machine, but it does provide a lot more for malware to work with, potentially allowing a malicious app to bypass all of the normal security features on your Mac. It's also very important to understand that this can be exploited by JavaScript, so it could be triggered as a result of visiting a website in your browser that might happen to have malicious code — it doesn't have to come from an app that you specifically choose to install on your Mac.
What Is Apple's Response?
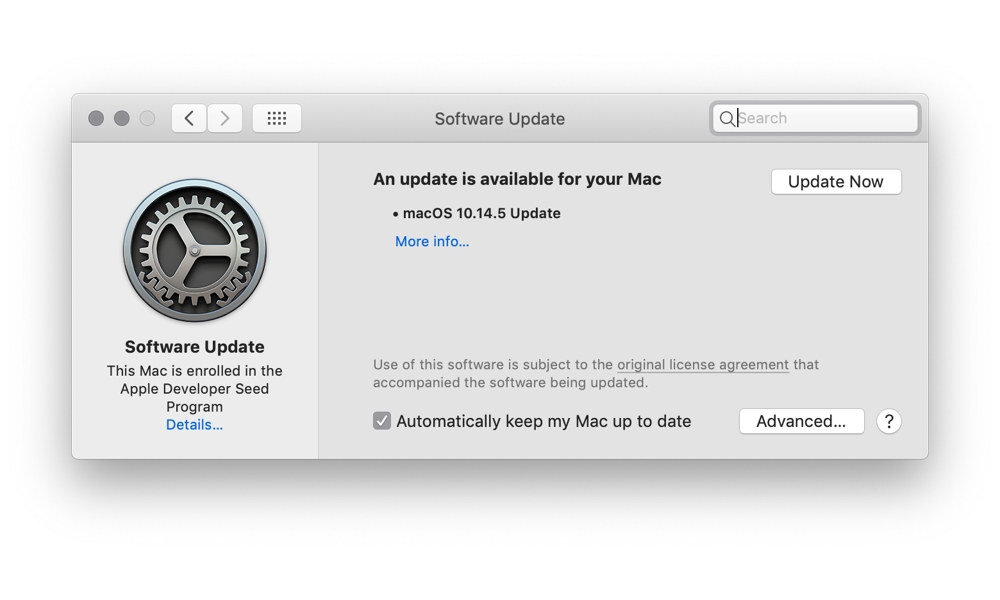
The good news is that Apple is already on top of it, with a series of fixes released earlier this week in the form of macOS 10.14.5 for those computers that support Mojave, and specific security updates for High Sierra and Sierra for those Macs that are stuck on older macOS versions.
Apple has also published a support document outlining the details of the vulnerability, along with some general safe computing recommendations to reduce the possibility of being impacted by these types of exploits in general, such as only installing apps from the App Store.
Unfortunately, Apple does provide a list of older Mac models that are unsupported, "due to a lack of microcode updates from Intel." All of the listed models, however, are from 2010 and earlier, which in theory shouldn't be impacted by the flaw in the first place. We suspect Apple is just being thorough here.
What Should You Do?
Users on macOS Mojave should immediately update to macOS 10.14.5, available through the normal software update mechanisms. If you're on an old Mac that can't run Mojave, you can instead apply Security Update 2019-003 to either High Sierra, or Sierra.
There are no security updates for versions of macOS prior to Sierra, so if you're running El Capitan, Yosemite, or an even older version, you'll need to bite the bullet and update to at least Sierra to get access to the fix. All affected Macs should support at least macOS Sierra.
What the Patch Does
Note that installing the security update by itself only patches the vulnerability in Safari, preventing exploitation via JavaScript or other malicious code from websites that you may visit. Since the only other way to be impacted by the vulnerability is by specifically installing a malicious app, this should be enough for most users — as long as you're using Safari as your only browser. Apple notes that it has been able to do this with no performance impact.
If you're using another browser like Chrome or Firefox, however, you'll need to install updates from your browser's developer (i.e. Google or Mozilla). Mozilla has said that it has a long-term fix on the way for Firefox, although in the meantime the company has applied the mitigations recommended by Apple, which will be included in Firefox release 67 and Extended Support Release update 60.7, both expected to arrive early next week.
Full Mitigation
As of this writing, however, Google's response to Chrome users has been to rely on operating system updates, which means you'll need to enable Apple's additional "full mitigation" procedure if you want to ensure you're protected. Apple doesn't enable these in the macOS patch by default, since they require you to disable hyper-threading entirely on your CPU, which will result in a serious performance hit — up to a 40% reduction, according to Apple.
The full mitigation steps will prevent any app from being able to exploit the vulnerability, but due to the performance cost it's only recommended for users in high-risk environments, those who regularly run untrusted apps on their Macs, or those who are simply extremely security conscious and willing to sacrifice that kind of performance in order to eliminate the risk completely. Sadly, however, since Google doesn't appear to be taking any steps to mitigate the issue in Chrome itself, users who rely on that browser will need to consider themselves to be in a "high-risk environment" and should apply the full mitigation steps. As far as we're concerned, this may be as good an excuse as any to switch to Safari.