Microsoft Condemns Spy Agencies After Massive WannaCry Attack
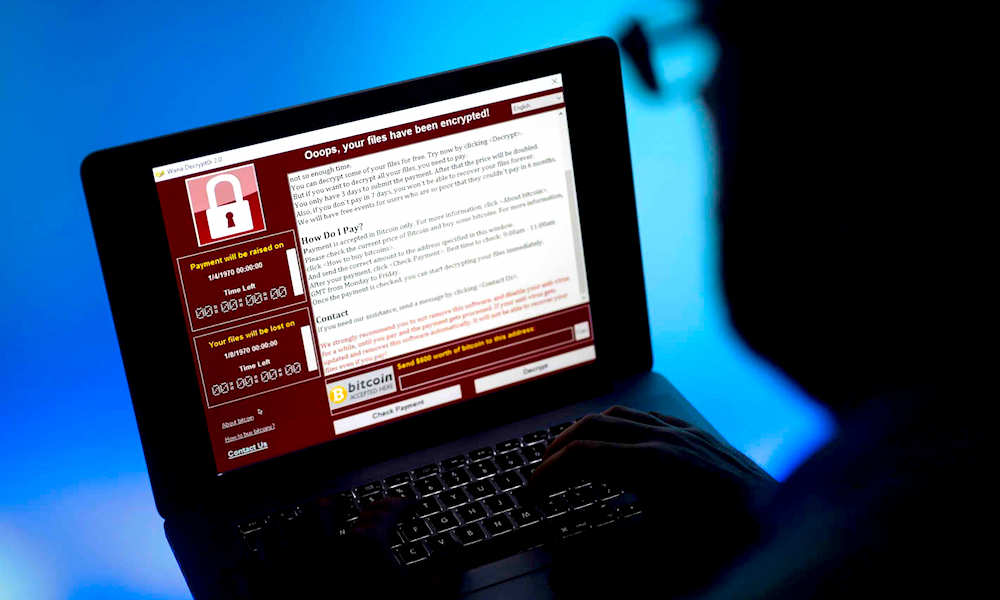
Image via NY Mag
Toggle Dark Mode
Microsoft castigated intelligence agencies for their role in the WannaCry cyberattack that crippled hundreds of thousands of computers across the world, analogizing the theft of the NSA hacking tools that enabled it, to “the U.S. military having some of its Tomahawk missiles stolen”. In doing so, the software giant called into question the government practice of hoarding zero-day exploits, which are a form of malware that can have devastating consequences if they end up in the wrong hands.
A Wake-up Call
“This attack provides yet another example of why the stockpiling of vulnerabilities by governments is such a problem”, Microsoft president Brad Smith wrote in a strongly worded company blog post. “We have seen vulnerabilities stored by the CIA show up on WikiLeaks, and now this vulnerability stolen from the NSA has affected customers around the world. Repeatedly, exploits in the hands of governments have leaked into the public domain and caused widespread damage.”
He went on to write that the latest ransomware attack should serve as a “wake-up call” to governments worldwide that they need to “adhere in cyberspace to the same rules applied to weapons in the physical world”. Smith, who is also Microsoft’s chief legal officer, used the occasion to issue another call for a Digital Geneva Convention on cyberwarfare, an idea he pitched earlier in February at the RSA security conference. At the time, he declared that “the time has come to call on the world’s governments to come together, affirm international cybersecurity norms that have emerged in recent years, adopt new and binding rules and get to work implementing them.”
Microsoft’s proposed Digital Geneva Convention would require governments to report vulnerabilities to vendors, rather than stockpile, sell, or exploit (or lose) them, in order to protect civilian internet use, much as the Fourth Geneva Convention furnished a set of rules governing the treatment of civilians in wartime in the aftermath of World War Two.
The WannaCry Attack
The WannaCry ransomware attack (also known as WannaCrypt, Wana Decryptor or WCry) began last Friday in the United Kingdom and Spain, and spread at an alarming rate to dozens of other countries in a matter of hours. WannaCry leverages an NSA-created exploit codenamed “EternalBlue”, which was leaked along with other NSA hacking tools last April by a group called the Shadow Brokers. It exploits a vulnerability in Windows software to lock down victims’ files, confronting them with ransom note for $300 or $600 in Bitcoin in exchange for restored access.
It bears noting that Microsoft issued a security patch for this very vulnerability in March. However, thousands of users neglected to update their systems in a timely fashion. A lax attitude towards security among users and organizations, paired with WannaCry’s ability to seek out vulnerable devices and propagate itself within a computer network like a worm, paved the way for Friday’s cyberattack to metastasize and spread at an unprecedented scale.
At last count, WannaCry had struck at least 300,000 computers, crippling hospitals, transport systems, and government agencies in more than 150 countries. High profile victims include FedEx, Russia’s interior ministry, major Spanish telecommunications provider Telefonica, and the UK National Health Service. While its advance slowed significantly over the weekend thanks to a happy accident (detailed below), WannaCry lingers on in Europe and continues to hit new targets in Japan and China, where the popularity of pirated Windows software has left computers especially vulnerable, NPR reports.
Despite its alarming spread, WannaCry has also proven to be remarkably inept at extracting ransom payments and crudely designed. Wired reports that the hackers have collected an estimated $55,000 so far– a paltry sum in view of the global scale of their internet-rattling attack– possibly due to inefficiencies in WannaCry’s ransom functions. Another inexplicable misstep on the part of the hackers was building an Achilles heel into their code, which was accidentally triggered by a researcher who operates under the pseudonym MalwareTech. While reverse-engineering WannaCry, MalwareTech found that the ransomware was designed to ping a certain gibberish URL and check whether it was active. He registered that domain name for around $10, a move that had the immediate effect of deactivating that strain of WannaCry, and sparing tens of thousands of computers.These aforementioned inefficiencies have left some security researchers wondering whether the hackers behind WannaCry were motivated by political purposes (like embarrassing the NSA) rather than monetary gain. But WannaCry’s success at self-propagating also suggests that attacks like these will become more popular in the future, perhaps fueled by more sophisticated cyberthieves eyeing an even bigger payday. WannaCry has already inspired copycats, as security experts had predicted. Cybersecurity firm Check Point announced the discovery of a new WannaCry variant on Monday that was spreading at a rate of about one computer per second. Thankfully, that variant also had a similar built-in “kill switch” that Check Point was able to initiate in order to halt it.






