Hackers Launch Global Ransomware Attack ‘WannaCry’ Using Stolen NSA Exploit
Toggle Dark Mode
Hackers have taken a stolen NSA spy tool and exploited it in a worldwide ransomware attack that has infected tens of thousands of computers in at least 74 countries, including Turkey, Vietnam, Japan, and Russia. The ransomware has been dubbed “WannaCry” and exploits vulnerabilities in Windows operating systems that haven’t updated a patch that Microsoft rolled out earlier this year.
It’s advised that users and companies that haven’t updated their Windows systems with the security patch do so immediately. And, as always, you should be careful when opening strange emails with attachments from unknown senders. Unfortunately, the patch won’t be much help for systems that have already been infected with the ransomware.
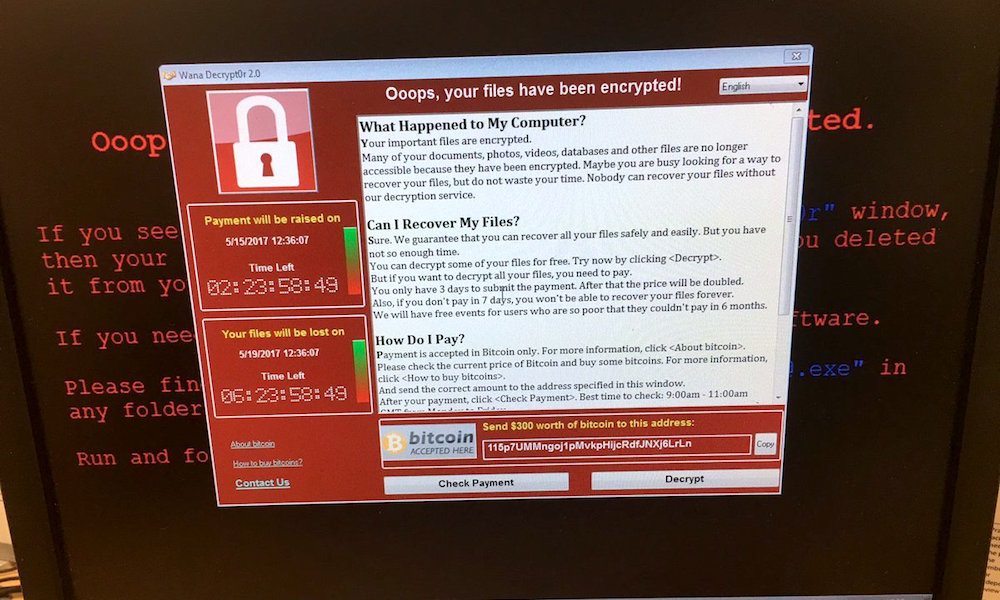
The WannaCry attack works by locking down files in the affected computer and demanding payment of $300 in Bitcoin in exchange for their release: “Your important files are encrypted.
Many of your documents, photos, videos, databases and other files are no longer accessible because they have been encrypted.” The ransom message comes with translations in 28 different languages including Russian, Chinese, and Portuguese, suggesting that the hackers intended to hit systems in multiple countries. It also comes with a countdown clock and warns that the ransom amount will be doubled after a set amount of time, and that after 7 days without payment, users will lose their files forever. Unfortunately, paying the hackers does not guarantee that they will release your files, nor does it ensure that they won’t attack your computer again in the future.
A Bitcoin wallet reportedly associated with the attackers shows a number of incoming transactions, so it appears that at least some victims have opted to pay the ransom, which has gone up to as much as $600 in some reported cases. Bitcoin is a favored form of cryptocurrency among cyberthieves because it is hard to trace.
The ransomware attack has been linked to a trove of hacking tools that were stolen from the NSA and dumped last month by a group known as the Shadow Brokers. One of the leaked exploits, codenamed “EternalBlue”, appears to be the primary vulnerability that the ransomware is spreading through. Following the April leak, Microsoft announced that it had preemptively addressed the flaws published by the Shadow Brokers and released the patch on March 14.
“We’ve investigated and confirmed that the exploits disclosed by the Shadow Brokers have already been addressed by previous updates to our supported products,” a Microsoft spokesperson told CNNTech in April. “Customers with up-to-date software are already protected.”
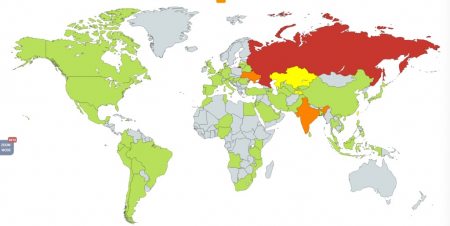
However, it’s apparent that many organizations and users did not update their systems in a timely fashion. As of Friday afternoon, Russian cybersecurity firm Kaspersky Lab said it had recorded at least 45,000 attacks in 74 countries, while noting that its visibility was limited and that “the range of targets and victims is likely much, much higher.” Another cybersecurity firm, Avast, reported a much higher incidence rate– 75,000 attacks in 99 countries. Both firms agree that the overwhelming majority of the attacks appear to have occurred in Russia.
Unlike typical ransomware, WannaCry has a “hunter” module that gives it the ability to spread itself to vulnerable computers within a system, which appears to have greatly magnified the scope of the attack. This ability has allowed WannaCry to spread like wildfire within an organization’s computer system once it has infiltrated it, likely through a malicious email attachment sent to an unsuspecting employee. One Milan-based user tweeted the following image that appears to show a university computer lab with multiple affected devices.
The rapid spread of the attack has deeply concerned cybersecurity experts, who warn that it has yet to run its course.
“It is going to spread far and wide within the internal systems of organizations — this is turning into the biggest cybersecurity incident I’ve ever seen,” UK-based security architect Kevin Beaumont said. Beaumont added that US firms would likely be affected by the ransomware, which has already hit organizations across Europe, including Portugal Telecom, the Russian Interior Ministry, and Russia’s Megafon. Spain’s Telefonica, which is one of the largest telecommunications companies in the world, had as much as 85% of computers in its internal network had been affected, according to the Interior Ministry.
FedEx also confirmed that it had been impacted by the attack. “Like many other companies, FedEx is experiencing interference with some of our Windows-based systems caused by malware,” the delivery company said in a statement. “We are implementing remediation steps as quickly as possible.”
Perhaps most devastating of all, the malware has crippled 39 National Health Service organizations and hospital in the UK, where hackers seized computers and blocked access to patients’ files, forcing some emergency rooms to reroute patients and ambulances, The New York Times reports. Doctors and patients in the UK also reported cancelled surgeries, though so far no injuries or deaths have been connected to the cyberattack. In response, the NHS published a statement on its website on Friday acknowledging the attack and stated that there was no “evidence that patient data has been accessed” at this time.
British Prime Minister Theresa May also issued a statement that the government was working closely with the NHS to resolve the matter and agreed that no patient data appears to have been compromised at this stage. “We are aware that a number of NHS organisations have reported that they have suffered from a ransomware attack,” she said. “The National Cyber Security Centre is working closely with NHS digital to ensure that they support the organisations concerned and that they protect patient safety.”
As of now, it’s unclear who is behind the massive attack, which is an object lesson on the importance of keeping your software up to date with the latest security patches. Without them, organizations and consumers could be vulnerable to a host of other forms of malware beyond ransomware. And unfortunately, there isn’t a clear solution for victims of the latest ransomware attack beyond paying the hackers (not recommended) and unplugging the infected computers to prevent it from spreading further.






