HomeKit Flaw Used to Install Pegasus Software on Serbian Journalists’ iPhones
 Credit: usfaridas / Shutterstock
Credit: usfaridas / Shutterstock
Toggle Dark Mode
Serbian authorities are suspected of exploiting zero-day vulnerabilities in Apple’s HomeKit to install Pegasus spyware, requiring no user interaction.
As reported by Amnesty International, Serbian police and intelligence authorities are using two tools — the well-known Pegasus spyware (created by Israel’s NSO Group) and a locally developed system called NoviSpy — to target journalists, activists, and other high-profile individuals as part of a covert surveillance campaign. Governments and organizations around the globe have previously used both pieces of software to target opposition leaders.
Pegasus exploits zero-day vulnerabilities (flaws unknown to software makers) to infect devices. Once installed, the spyware can not only scrape messages, emails, photos, and other files from a phone, but it can also be used as a surveillance device.
No interaction on the user’s part, like clicking a link, is required to launch a Pegasus attack.
NoviSpy operates similarly but appears designed to solely target individuals in Serbia. Officials are reportedly using Cellebrite to install NoviSpy in cases where devices are being physically seized by police, such as at traffic stops or “interviews.”
While Cellebrite is designed for use by law enforcement for forensic purposes, like extracting data from locked phones, it can also be used to unlock devices, bypassing security locks and allowing authorities to install spyware.

At least one journalist, Slavisa Milanov, said his phone began acting strangely after leaving it at a police station for a few minutes. Later analysis discovered that not only had Cellebrite been used to unlock his device but that NoviSpy had also been installed while the phone was out of his hands.
Authoritarian regimes can use spyware tools like NoviSpy and Pegasus to monitor encrypted chats, map out personal associates, and gather intelligence on upcoming protests or other activist activities.
As you might imagine, this has had a chilling effect on the activities of journalists, activists, and other high-profile people. As reported by AppleInsider, one activist says he avoids using his phone altogether and now only meets his sources in public places.
It is believed that authorities took advantage of security vulnerabilities in Apple’s HomeKit smart home platform to install the spyware. While HomeKit uses secure protocols to communicate with devices, attackers can exploit security flaws via network manipulation or malicious invitations, as researchers at the University of Toronto’s Citizen Lab discovered in 2022. Apple quickly patched those vulnerabilities, but that doesn’t mean others don’t exist.
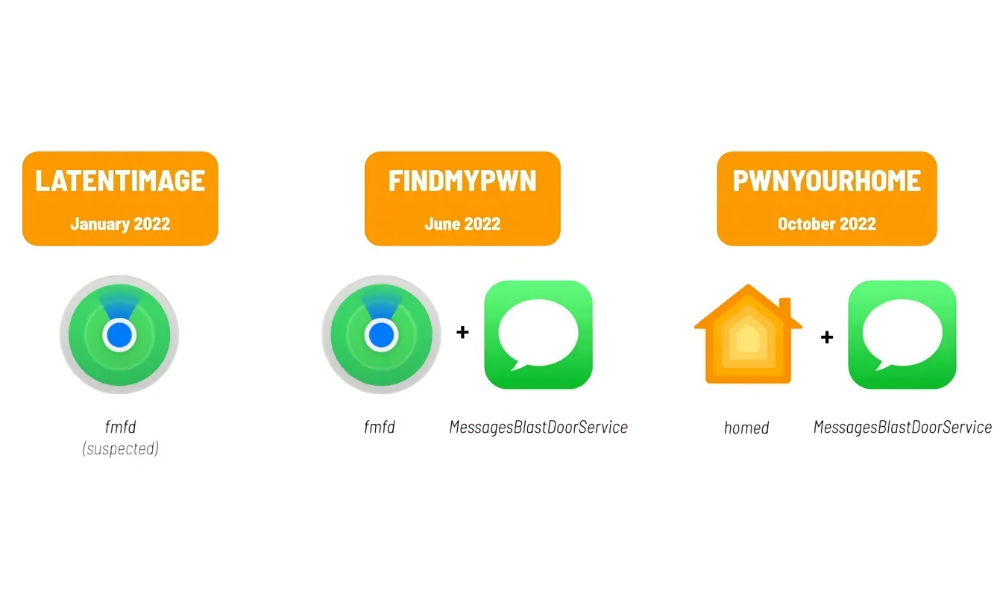
Pegasus often uses flaws in Apple’s iMessage to install spyware remotely. However, Apple has been working hard to close those doors. HomeKit exploits, while less common, could also provide an entry point for attackers, and any such vulnerabilities exist in a corner of iOS that’s likely scrutinized less closely than more common attack vectors like Messages, Safari, and Mail.
Over the years, Pegasus and other tools have been used worldwide to target opposition, journalists, human rights activists, and other high-profile individuals.
While Apple responds quickly to plug security holes used by such exploits, it is a constant game of back and forth between Apple and the bad actors of the world. Apple hires engineers to identify vulnerabilities before they are exploited, but spyware developers continue to search for new security flaws that can be used in their attacks, and companies like NSO Group have vast resources as they count deep-pocketed government agencies among their biggest clients.

Apple is using a combined effort that combines technical and legal efforts to combat Pegasus and other spyware. In 2021, Apple sued NSO Group, seeking to block its access to Apple services and devices. It recently asked to have that case dropped, but only because of fears that it would do more harm than good by forcing the company to disclose confidential information that would help mercenary spyware firms develop even better tools.
In iOS 16, Apple debuted “Lockdown Mode” to shrink the attack surfaces used by such tools — what it calls “extreme protection that’s designed for the very few individuals who, because of who they are or what they do, might be personally targeted by some of the most sophisticated digital threats.”
Unfortunately, Pegasus continues to evolve, as three new zero-click exploits targeting iPhones were developed in 2023.
How Can Users Protect Themselves?
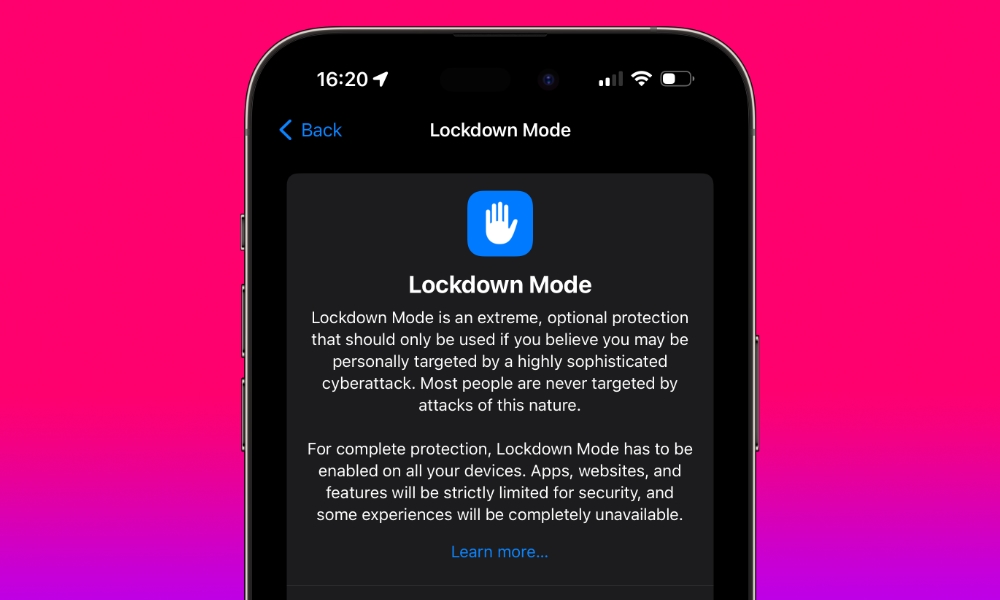
In addition to using strong, unique passwords and enabling two-factor authentication, journalists, activists, and other possible target individuals can enable Lockdown Mode in iOS.
Lockdown Mode is designed for high-risk users to protect themselves from targeted spyware attacks. Lockdown Mode hardens device defenses and strictly limits certain functionalities. This greatly reduces the attack surface that could be exploited by mercenary spyware.
Lockdown Mode on your iPhone or iPad can be enabled by going into the Settings app, tapping “Privacy & Security,” and scrolling down to Lockdown Mode. Tap “Turn On Lockdown Mode,” review the explanation of how the feature works, and confirm by selecting “Turn On Lockdown Mode.”
Your device will reboot with Lockdown Mode active, restricting certain features to enhance security. The feature can then be disabled anytime by following the same steps.







