Google Authenticator Now Syncs Two-Factor Codes | Here’s Why You Shouldn’t Use It
 Credit: PixieMe / Shutterstock
Credit: PixieMe / Shutterstock
Toggle Dark Mode
Google’s free Authenticator app has long been one of the best ways to store the timed codes needed for the two-factor authentication (2FA) systems used by many online services. However, it’s always suffered from one annoying limitation: these codes were stored only on whatever device you used.
While it’s hard to argue against the security of such an approach, it made it a hassle for folks who wanted to access their two-factor codes from multiple devices, such as an iPhone and iPad. It was also a nuisance when upgrading to a newer iPhone since the codes typically won’t be restored from a backup onto a new phone due to how they’re stored in the app.
Needless to say, it was a breath of fresh air when Google product manager Christiaan Brand shared the news this week that Google Authenticator can back up and sync one-time codes using your Google Account. That gets a well-deserved “finally” when you consider the app was released in 2010 as one of the first 2FA apps on the market.
However, that excitement was short-lived after security researchers took a closer look at what Google was doing and discovered it lacks important protections for storing data as sensitive as people’s 2FA codes.
In a lengthy tweet (yes, Twitter now lets paying members write essays), the developers and security analysts at Mysk called out the lack of end-to-end encryption (E2E) in the new system and advised Google Authenticator users not to enable it.
We analyzed the network traffic when the app syncs the secrets, and it turns out the traffic is not end-to-end encrypted. As shown in the screenshots, this means that Google can see the secrets, likely even while they’re stored on their servers. There is no option to add a passphrase to protect the secrets, to make them accessible only by the user.Mysk
While you may think there’s no harm in exposing 2FA codes that change every 30 seconds, the Google Authenticator information stored unencrypted in your Google Account also contains the secret keys, or “seeds,” used to generate these codes. This means that anybody with access to this information could generate the same 2FA codes on another device, thereby leading to a potential compromise of your security.
Of course, they’d still have to know your password as well, but the whole point of 2FA is to secure your accounts in the event that your password gets intercepted or leaks out through a data breach.
On the upside, the 2FA secrets are not included in data exported from your Google Account, so they’re secure in that regard, but there’s still a risk that they could be exposed in some other way if a hacker were to gain access to your Google Account.
Further, as the team at Mysk notes, there’s also a privacy aspect to this: “Since Google can see all this data, it knows which online services you use, and could potentially use this information for personalized ads.” Google’s data-mining practices are well known, so one can’t assume it wouldn’t use this data to profile its users.
Fortunately, the new syncing feature is entirely opt-in; you can still use the app like you always have, storing your secrets only on your device. Following the report of security concerns, Google’s Christiaan Brand explained why the company chose to omit end-to-end encryption, noting that it comes “at the cost of enabling users to get locked out of their own data without recovery.” He adds that E2E is coming for Google Authenticator “down the line,” at which point you will presumably be able to use it securely. It’s best to avoid it until that happens or consider an alternative app for handling your 2FA codes.
Ditch Google Authenticator and Use iCloud Keychain
Since Google naturally pushes its own Google Authenticator app, many Gmail users have come to believe this is the app they’re required to use to access their Google Account and other services that use 2FA.
However, nothing could be further from the truth. Sure, Google Authenticator handles that well, and it’s been around for so long it’s become a de facto standard for 2FA credentials. However, it’s not the only game in town by a long shot.
In fact, if you’re using iOS 15 and/or macOS Monterey or later, you can ditch Google Authenticator entirely and switch to iCloud Keychain, which has included robust end-to-end encryption since its inception in iOS 7 and OS X Mavericks in 2013.
While iCloud Keychain has been able to store passwords securely for years, the ability to handle two-factor authentication codes only came along in iOS 15 and its other accompanying iPadOS and macOS releases. However, that now makes it a complete replacement for Google Authenticator, especially since it already syncs all this information across every iPhone, iPad, and Mac signed into your iCloud account and can autofill these codes for you in Safari. Apple offers a Windows app for it, too.
Third-party password managers like 1Password have also supported storing 2FA codes for a long time, with the same autofill features, so if iCloud Keychain isn’t cutting it for you, you can always turn to one of those.
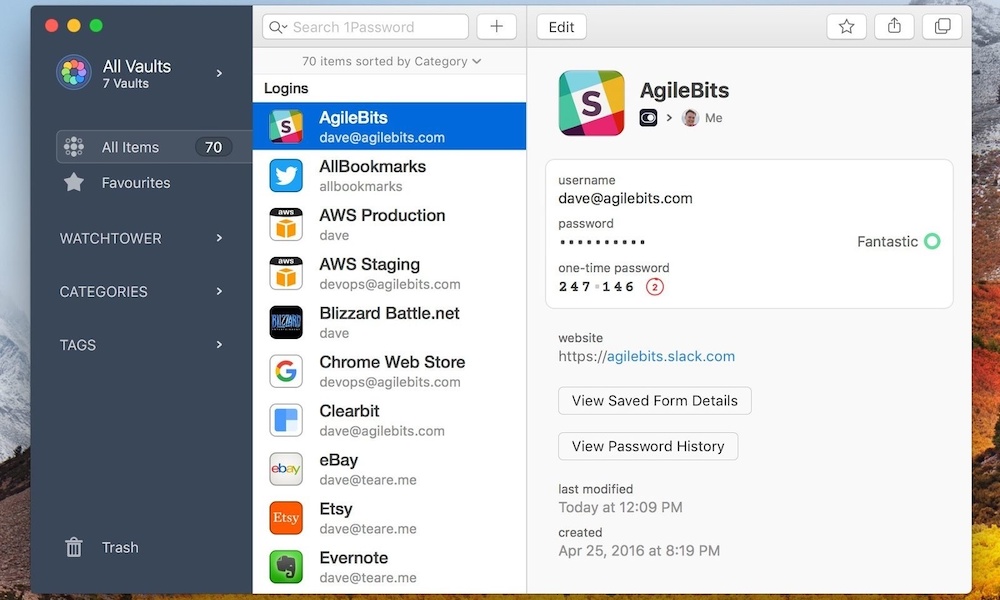
However, there’s a valid argument that storing your passwords and 2FA codes in the same app keeps all your eggs in a single basket. A security breach of that app would give hackers all the pieces they need to compromise your accounts. If that concerns you, then there are a variety of standalone 2FA apps like Authy, OTP Auth, and TOTP that get the job done. Some even offer Apple Watch apps to quickly get your 2FA codes from your wrist. That’s something that Google Authenticator won’t do for you.
Just keep in mind that you’re not really improving security by using a separate 2FA app if it’s installed on the same iPhone as your password manager unless you protect it with a different password and it supports local encryption of your OTP data. Otherwise, anybody who gets their hands on your iPhone and can unlock it can fish your 2FA codes out of a separate app even more easily than they can get into a more secure password manager like 1Password.









