Crooks Are Trying to Bribe Carrier Reps to Hack Your Phone
 Credit: Brett Jordan
Credit: Brett Jordan
Toggle Dark Mode
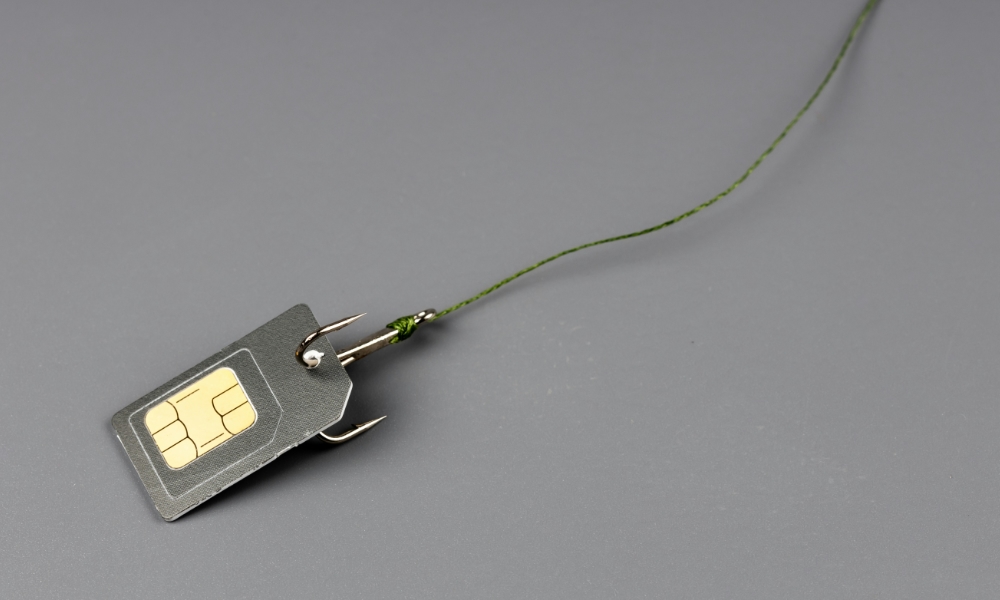
While two-factor authentication is a great way to protect your account against unauthorized access, it also exposes one of the most significant weak points in most people’s online security: the humble SIM card that links you up with your carrier’s network.
It’s a vulnerability that should be apparent as soon as you take a moment to think about it. Your cell phone number is the method most commonly offered for two-factor authentication and is often also used to send password reset requests. This means anyone who gets their hands on your phone number can intercept these messages and wreak havoc in your personal life.
While stealing your phone is an obvious method of getting at your SIM card, most crooks use a more insidious tactic known as a SIM swap attack. Sometimes also referred to as “SIM-jacking,” this is where a fraudster typically uses social engineering tactics to impersonate you and convince a customer service rep at a cellular carrier or store to transfer your number to a new SIM card that they’ve just purchased.
Unlike many cyberattacks, this is far more than a hypothetical scenario. The FBI warns that SIM swap attacks have been on the rise in recent years, and even as carriers find ways to defend against them, clever criminals are finding new ways around these protections.
Last month, we shared the story of a Canadian couple who lost over $160,000 when a criminal accessed and cleaned out their accounts after transferring the husband’s phone number to a new SIM card. This was reportedly done at a carrier store, although it’s unclear whether the employee was an unknowing dupe or was somehow complicit in the crime.
At the carrier level, protections against unauthorized SIM swaps shouldn’t be too difficult. Requiring proper identification and other verification steps to confirm they’re talking to the real account holder is a big step in the right direction, but employees can still be the weakest link in that chain, particularly if they are not required to actually enter that information into a system before the swap can proceed.
These attacks most often succeed as a result of employees who aren’t on the ball. A 2020 Princeton Study found a shocking number of attempts to conduct SIM transfers succeeded without the caller answering any of the required security questions. In most cases, simple “playing dumb” social engineering tactics convinced well-meaning customer service reps to proceed with the swap. Other problems included carriers asking the caller to confirm two or three recent calls for verification. In some scenarios, they only needed to provide a list of incoming calls to the victim’s phone — something trivially easy for an attacker to generate simply by calling their target a few times.
However, as carriers have closed some of these loopholes, it looks like crooks are trying to exploit that human weakness in an entirely different way: by offering bribes to recruit accomplices within the carriers.
As shared by 9to5Mac, an organized campaign is now targeting employees at T-Mobile and Verizon, offering bribes of $300 for each SIM they successfully swap for the perpetrators of these attacks.
According to The Mobile Report, T-Mobile employees across the country have been receiving unsolicited text messages offering them cash in exchange for swapping SIM cards on request. While the initial contact comes via SMS, they ask the workers to contact them on Telegram if they’re interested. The contact information for the employee appears to have come from a recent data breach, but Bleeping Computer notes that Verizon employees have been receiving similar messages.
Protect Yourself from SIM Swap Attacks
While the Federal Communications Commission (FCC) has introduced more substantial carrier requirements to protect consumers against these attacks, the jury is out on how well these will work in practical terms, especially against “inside jobs” where carrier employees are helping the attackers.
Nevertheless, at least one of these protections could make a big difference as long as you’re paying attention; carriers are supposed to proactively notify you whenever a SIM swap is requested by texting your existing number before conducting the transfer.
It’s a technique that some carriers already use to protect against port-out scams — when a crook tries to transfer your phone number to an entirely different account — but SIM swap attacks are trickier. One of the challenges is dealing with a situation where a customer’s existing SIM card is legitimately lost or damaged and, therefore, unable to receive texts.
In many cases, carriers are adopting an assumptive notification for this by sending you a message to advise that a SIM transfer has been requested and is about to go through. The transfer automatically proceeds if you don’t respond within a set timeframe. That’s a step in the right direction, but it only works if you catch it quickly.
The best way to protect your personal data against SIM swap attacks is to remove your SIM card from the equation. Avoid using your phone number as a second factor or a password reset fallback as much as possible. Most services will let you use two-factor authentication apps that generate a login code on your iPhone or even your Apple Watch, and password resets are better done by email than SMS (provided your email account is secure, of course).
If you want to be sure that password resets won’t go to your phone, try removing your phone number from your profile entirely on critical services like banking and email. If they don’t have your number, they can’t use it to send you a text message even if they want to. As a bonus, you can also be confident that any texts you receive that claim to be from these companies are much more likely to be scams.
It’s also a good idea to contact your carrier and ask about additional protection they can add to your account. Verizon has a Number Lock option that you can turn on right in the MyVerizon app, while T-Mobile’s similar SIM Protection will require a visit to your account settings.
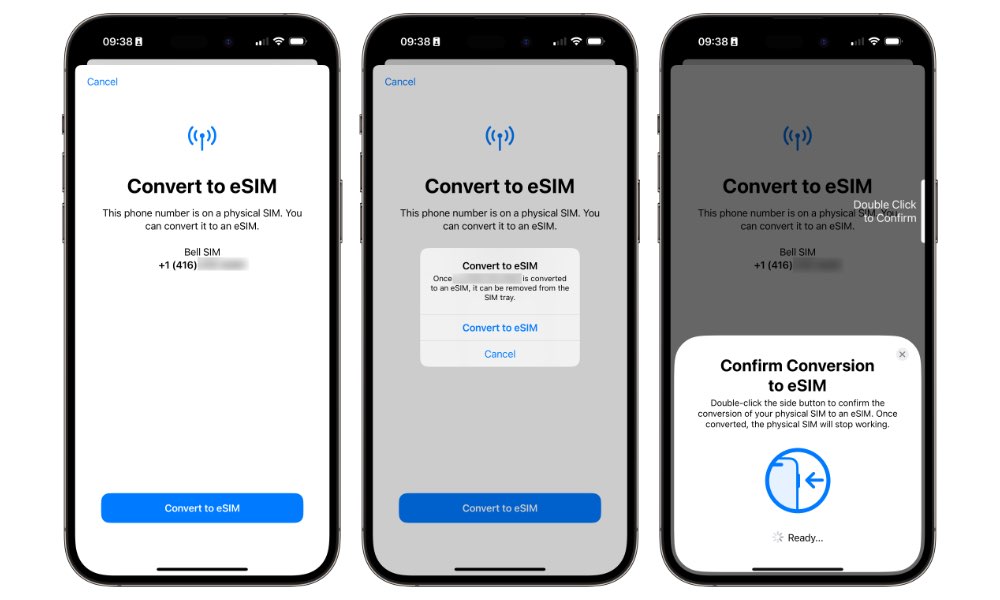
Although T-Mobile says that “SIM protection does not prevent eSIM transfer on Apple devices,” it adds that this is “due to the extensive security steps already included in that process.” An iPhone eSIM transfer can’t be conducted remotely; it requires both iPhones to be in close proximity and needs to be authenticated with Face ID, Touch ID, or a password.
This makes for another good reason to use an eSIM instead of a physical SIM in your iPhone. All models from the iPhone XS/XR onward support eSIM, and all major US carriers make it easy to transfer to an eSIM right on your device. If you lose your iPhone, anyone who picks it up can pop out a physical SIM card and insert it into any other phone to place calls and send and receive SMS messages using your phone number. Setting up a PIN code on your SIM card can protect against that, but it’s much better to simply switch to an eSIM.
An eSIM can’t realistically be removed and it’s protected by your iPhone’s security. Plus, if you remote wipe your iPhone, the eSIM gets wiped along with it.