Researchers Discover Malicious Spyware App Targeting iPhone Users
 Credit: Hadrian / Shutterstock
Credit: Hadrian / Shutterstock
Toggle Dark Mode
A powerful spyware app originally designed to target Android devices now has iPhone users in its crosshairs, security researchers have discovered.
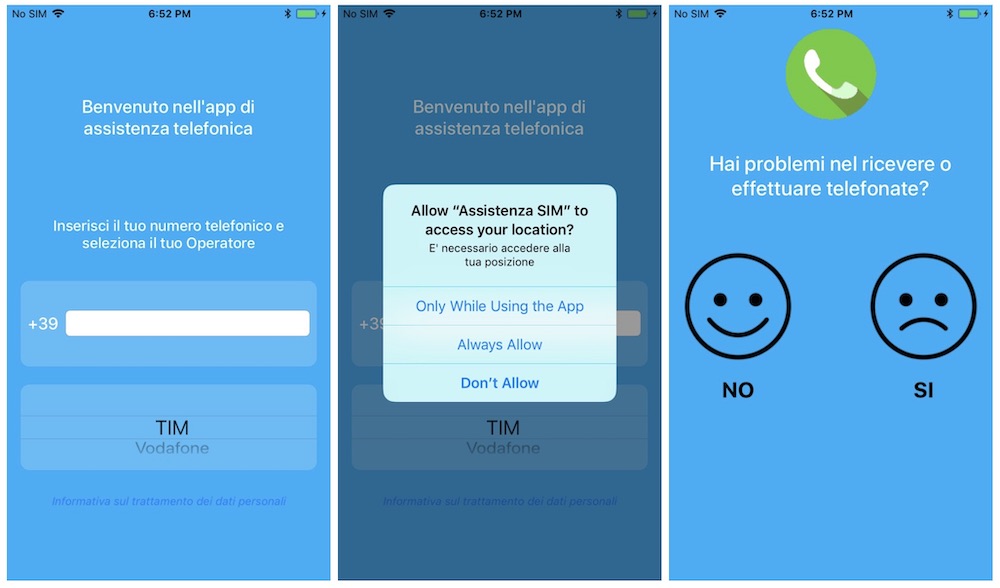
The surreptitious surveillance app was first discovered by researchers at Lookout, a mobile-focused security firm (via TechCrunch). According to those researchers, the spyware masqueraded as a carrier assistance app and abused Apple enterprise certificates to bypass the App Store.
Once the app was installed on a user’s device, it could secretly steal the user’s contacts, photos, videos, voice memo recordings and other device data — such as a user’s real-time location.
It isn’t clear who the app may have been targeting, and the researchers said there isn’t data to suggest how many iOS users had been impacted.
Lookout pointed out that the spyware was side-loaded onto devices from fake cellular carrier websites in Italy and Turkmenistan.
On the other hand, security researchers were able to link the iOS spyware to the creators of a previous Android app. That app, dubbed Exodus, was also a surveillance program developed by Connexxa and known to be in use by Italian government entities.
According to Security Without Borders, Exodus was installed on hundreds of devices — sometimes willingly, sometimes without a user’s knowledge. Unlike the newly discovered iOS spyware, Exodus had a wider set of surveillance abilities because it was able to gain root access to a device.
Worringly, Lookout notes that the iOS spyware and Exodus are both built on the same backend infrastructure. The iOS surveillance app used several advanced techniques to make it difficult to analyze its network traffic, Lookout’s Adam Bauer told TechCrunch.
The use of those techniques is “one of the indicators” that the app was developed by professionals. Presumably, that means a government entity or a high-profile hacking group.
While Exodus was available on the Google Play store, Apple’s App Store restrictions are much more stringent. Because of that, Connexxa had to sign the app with an enterprise developer certificate to bypass the App Store review process and side-load the software onto a device.
That is, of course, a clear violation of Apple’s enterprise certificate guidelines. Those certificates are meant solely for internal app installation and management at larger companies or other enterprise users. They’re not meant to push apps onto consumer devices.
It isn’t the first time that a developer has abused Apple’s enterprise certificate guidelines. Earlier this year, both Facebook and Google were found to be violating those guidelines by using an enterprise certificate to deploy surveillance apps onto consumer devices.
Apple, in response, revoked Facebook and Google’s certificates — causing serious problems at both companies until the Cupertino tech giant issued new certificates. The enterprise certificate side-loading technique has also been used by other apps not allowed on the App Store, such as pornographic and gambling apps.
Ultimately, users should never side-load apps onto their devices as they threaten security and privacy – users should only download apps directly from Apple’s App Store.