PSA: Secure Your iCloud Account After Big Password Leak
 Motortion Films / Shutterstock
Motortion Films / Shutterstock
Toggle Dark Mode
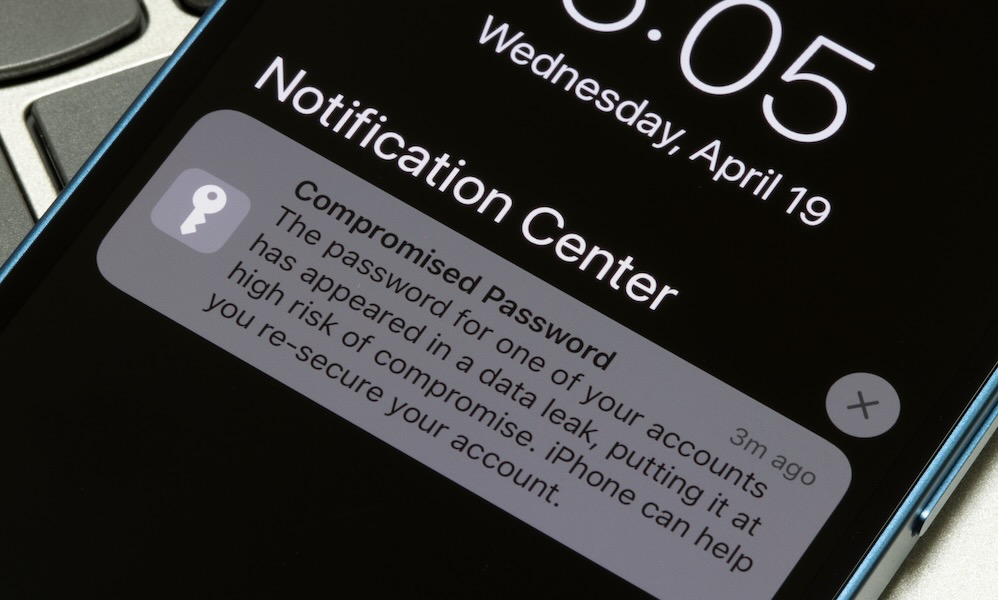
There’s been another massive password leak, which means you may want to check the Apple Account you use for iCloud and any other critical accounts for email and banking to ensure that they haven’t been compromised.
Earlier today, cybersecurity researcher Jeremiah Fowler reported a malware data breach that exposed over 184 million logins and passwords, many of which may be used for Apple Accounts.
The data came via what Fowler believes was infostealer malware — “a type of malicious software designed specifically to harvest sensitive information from an infected system.” While the source of the database is unclear, it was not password-protected or encrypted and contained 184,162,718 unique logins and passwords, totaling 47.42 GB of raw credential data.
“I saw thousands of files that included emails, usernames, passwords, and the URL links to the login or authorization for the accounts,” Fowler said. “The database contained login and password credentials for a wide range of services, applications, and accounts, including email providers, Microsoft products, Facebook, Instagram, Snapchat, Roblox, and many more,” plus bank and financial accounts, health platforms, and government portals from numerous countries.
While Fowler didn’t specifically mention Apple Accounts, a deeper analysis of the data by Wired found that plenty of those were also included.
In a sample of 10,000 records analyzed by Fowler, there were 479 Facebook accounts, 475 Google accounts, 240 Instagram accounts, 227 Roblox accounts, 209 Discord accounts, and more than 100 each of Microsoft, Netflix, and PayPal accounts. That sample—just a tiny fraction of the total exposure—also included Amazon, Apple, Nintendo, Snapchat, Spotify, Twitter, WordPress, and Yahoo logins, among many others. A keyword search of the sample by Fowler returned 187 instances of the word “bank” and 57 of “wallet.”
Matt Burgess and Lily Hay Newman, Wired
While neither Fowler nor the team at Wired conclusively determined the source or purpose of the database, Fowler says he suspects it was a dataset compiled by a cybercriminal through other infostealer malware tools. “It’s the only thing that makes sense,” he told Wired, “because I can’t think of any other way you would get that many logins and passwords from so many services all around the world.”
That theory is bolstered by the fact that the database was located on an unmanaged server run by a hosting provider, which is fully controlled by a customer. “It appears a fraudulent user signed up and uploaded illegal content to their server,” said Seb de Lemos, the CEO of World Host Group, in a statement to Wired. “The system has since been shut down. Our legal team is reviewing any information we have that might be relevant for law enforcement.”
What This Means For You
Unlike many of the data breaches we’ve seen, this isn’t a database that only includes data from a single company’s customers. While there have been some serious data breaches where account data has been stolen from services like Facebook, Adobe, Dropbox, LinkedIn, and others, these breaches have only revealed user accounts from those specific services.
That was still a problem for users of those services, but not for anyone else unless they used the same passwords across multiple sites. Sadly, many people do that, but these data breaches are perfect examples of why that’s extremely dangerous.
However, this particular data breach could be much more serious, as it contains a collection of passwords for multiple services. It’s highly unlikely that these credentials were stolen directly from company databases; if Fowler’s theory is correct, they likely originated from malware and phishing attacks conducted by cybercriminals.
“This is probably one of the weirdest ones I’ve found in many years,” Fowler told Wired. “As far as the risk factor here, this is way bigger than most of the stuff I find, because this is direct access into individual accounts. This is a cybercriminal’s dream working list.”
In other words, even though Apple’s servers have not been compromised, Apple Account passwords could still have been collected from malware running on Macs and PCs where people log in to iCloud or other Apple services. Ditto for other online services.
Those who use the same password for their Apple Account as other services could find themselves similarly compromised even if their actual Apple Account information isn’t in this data dump. That’s an even bigger problem if you use an “icloud.com” email address to sign up elsewhere, as it makes it evident to hackers that you’re also an Apple user. Apple Accounts tend to be high-value targets due to the extensive data most people store there, such as photo libraries and iCloud backups.
The good news is that if you’re using two-factor authentication for your Apple Account (and you really should be), then you likely don’t have too much to worry about. There is no evidence that the compromised data includes 2FA credential information, and it’s unlikely that this data could have been obtained unless it came from malware that directly harvested data from password management apps rather than just keyloggers and phishing attacks.
Nevertheless, it’s still a very good idea to change your passwords for all critical services immediately. That includes your Apple Account, banking, and financial accounts, as well as any other services you use for things like email since your email account is where password reset requests often end up.
If you haven’t yet enabled two-factor authentication for your Apple Account, there’s no time like the present. You can read more about how to do that in Apple’s guide to enabling two-factor authentication. If you want to take things a step further, you can even add a hardware security key to your Apple Account, preventing anyone from accessing it without an additional physical security device.
If you’ve read this far, you should also know that reusing passwords is a terrible idea. At the very least, ensure that you have unique passwords for all critical accounts; ideally, consider using a password manager to generate random and unique passwords for all your services. Apple’s built-in Passwords app makes this easy. Still, if you’re willing to pay for a more powerful solution, we suggest checking out 1Password, which not only provides more robust cross-platform support but also includes tools that will notify you if your passwords have been compromised in a data breach.
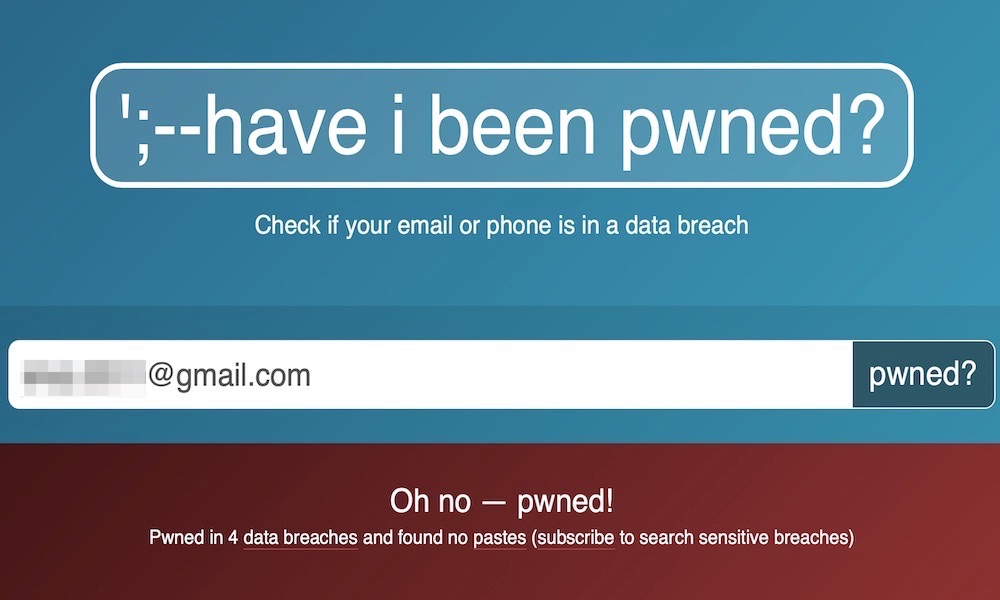
You can also visit Have I Been Pwned to see if your information appears in any data breaches. This latest database has yet to be added, but it’s still worth checking if any of your other accounts are vulnerable from past breaches. If you’re like most folks online, there’s a good chance your email address will show up in a few of these, but the good news is that as long as you’re using unique passwords everywhere, many of these won’t matter. For example, my info was caught up in the Hot Topic data breach from last fall (don’t judge — I have a teenage daughter), but it goes without saying that I didn’t sign up for an account there with a password that even vaguely resembles one I use for anything actually important.
Lastly, be extra diligent about potential phishing attacks. Cybercrooks who get access to this data may not be able to get at your important accounts, but if your email address is in there, it gives them a new attack vector to try to spam you with fake emails directing you to fake websites where they hope to convince you to give them your passwords.