Leaked Document Reveals How the Police Hack into Locked iPhones
 Credit: iDrop News / Elijah Fox
Credit: iDrop News / Elijah Fox
Toggle Dark Mode
Apple’s iOS platform has several security measures to prevent others from accessing your data without consent. Though most of these safety features are designed to thwart hackers and thieves, they also serve to lock down your iPhone from law enforcement. Police departments circumvent these controls using GrayShift’s GrayKey tool, a highly controversial device that can pull data from iPhones and iPads.
Up until now, we knew very little about GrayShift’s GrayKey iPhone unlocking device. The device has been rumored to be in use at police departments in the United States, but details on how it is being used have been sparse.
A recent report at Motherboard lifted this veil of secrecy. The news outlet obtained a document with detailed written instructions for the device.
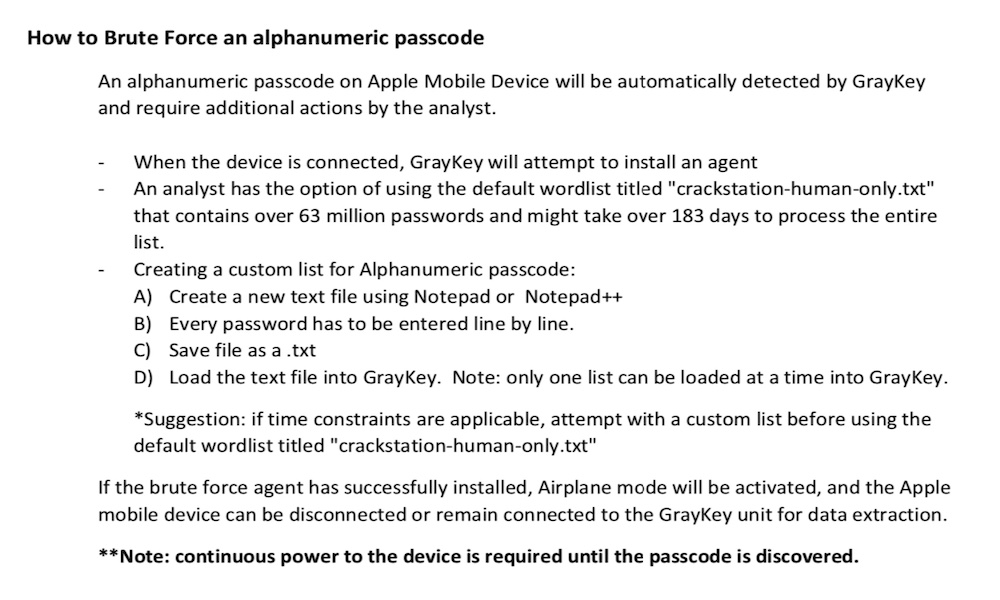
Not meant for public consumption, the document details how the device can unlock an iPhone “Before First Unlock (BFU)”, “After First Unlock” (AFU) when the phone is already on and when it has a damaged screen or low battery.
The device allegedly uses a brute force method to obtain access to an iPhone or iPad. The device installs an agent on the iOS device, which runs until the passcode to unlock the device is discovered. Once retrieved, the GrayKey device can pull off data immediately. It also can grab the metadata from files that remain inaccessible.
The leaked documentation published by Motherboard also mentions another app called HideUi, which can be covertly installed on an iPhone or iPad. The iOS device is then handed back to the unsuspecting owner. This HideUi software then secretly records a user’s passcode when they are using the device.
The San Diego Police Department supposedly wrote these GrayKey instructions for internal use by law enforcement officers. The instruction manual warns officers that GrayKey should only be used after “proper search authority has been established for the requested Apple mobile device.”
Though not confirmed, it is believed that the FBI used a GrayKey device to access a locked iPhone 11 Pro in a 2019 high-profile investigation of Baris Ali Koch. Koch was suspected of lying to federal agents and helping his brother escape the US to avoid prison time. As part of its search warrant, the FBI listed a USB drive containing “GrayKey derived forensic analysis” of the suspect’s iPhone.