The iPhone’s Lockdown Mode Just Passed a Significant Real-World Test
Toggle Dark Mode
On January 26, 2026 Aurelio Perez-Lugones, a US Navy veteran and defense contractor was indicted by a Federal Grand Jury on five counts of unlawfully transmitting and one count of unlawfully retaining classified national defense information.
A DOJ press release alleges that, between October 2025 and January 2026, Perez-Lugones repeatedly accessed and removed classified reports from the sensitive compartmented information facility (SCIF) where he worked as a government contractor and shared them with a reporter.
The nature of the information Perez-Lugones is accused of mishandling isn’t publicly known as court documents relating to the information are sealed. However, in a move that’s sparked outcry from First Amendment advocates, a sealed search warrant was executed at the home of journalist Hannah Natanson of The Washington Post, who the DOJ believes was Perez-Lugones’ contact, referred to as “Reporter 1.”
Court orders, like search warrants and subpoenas, used to obtain information from journalists usually require a high level of scrutiny. During the search, Natanson’s personal computer, a Washington Post laptop, iPhone, and Garmin watch were all seized by the FBI. However, Natanson herself is not under investigation, and has not been charged with anything, according the Freedom of the Press Foundation:
This is an alarming escalation in the Trump administration’s multipronged war on press freedom. The Department of Justice (and the judge who approved this outrageous warrant) is either ignoring or distorting the Privacy Protection Act, which bars law enforcement from raiding newsrooms and reporters to search for evidence of alleged crimes by others, with very few inapplicable exceptions.
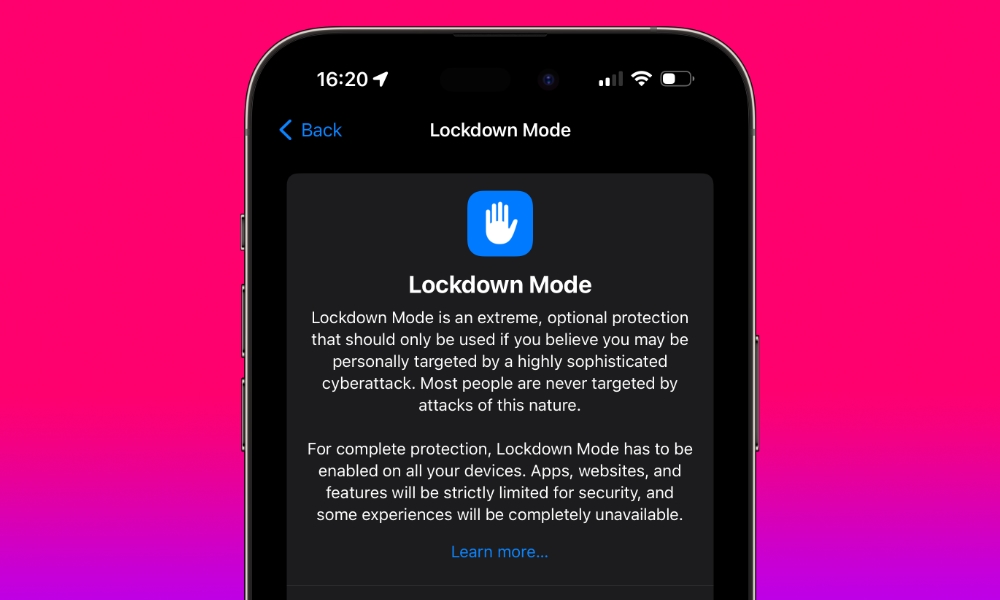
Controversy aside, it turns out the FBI can’t access Natanson’s iPhone because it was in Lockdown Mode.
According to a court filing opposing the return of her property and a Standstill Order preventing further efforts towards accessing these devices, the DOJ said, “The iPhone was found powered on and charging, and its display noted that the phone was in “Lockdown” mode.” Because of this, CART, the FBI’s Computer Analysis Response Team, hasn’t been able to access it.
Lockdown Mode is, according to Apple, designed to protect against the “extremely rare and highly sophisticated cyber attacks…Most people are never targeted by attacks of this nature.” It must be enabled on your iPhone, iPad, and Mac separately. When enabled on your iPhone, Lockdown Mode is automatically turned on for your paired Apple Watch. It’s also possible to exclude certain apps or websites in Safari from Lockdown Mode.
Can Lockdown Mode be cracked by industrial grade tools the FBI’s CART has either developed independently or has access to? So far, there don’t appear to be any cases of Lockdown Mode being successfully bypassed, and the fact that it blocks most message attachments and web technologies basically shuts the “backdoors” that sophisticated hacking tools like Cellebrite and GrayKey use to break into iPhones.
The FBI apparently forced Natanson to unlock her work MacBook with her fingerprint, which was allowed due to a 2024 D.C. Circuit appeals court ruling police may compel a suspect to unlock a device using biometric data, but not passwords. It’s unclear if her iPhone and MacBook were sharing an iCloud account, but if Natanson’s iPhone was syncing documents to the now-unlocked MacBook, the FBI may already have everything they’re looking for.
As of now, the matter is still pending a decision and Perez-Lugones remains detained pending trial. If reporters didn’t already have Lockdown Mode enabled across their devices, they’re certainly thinking about it now.







