US Cyber Defense Agency Issues Urgent Warning for iPhone Users
 gguy / Adobe Stock
gguy / Adobe Stock
Toggle Dark Mode
CISA, the federal agency tasked with defending the US against cyber threats, issued a fresh warning to iPhone users yesterday via an updated Mobile Communications Best Practice Guidance document, recommending specific actions for Apple smartphone users.
This guidance was developed in response to joint efforts by CISA and the FBI that revealed that actors affiliated with the People’s Republic of China (PRC) have engaged in a “broad and significant” cyber espionage campaign compromising multiple telecommunications companies. This coordinated attack resulted in the theft of customer call records data, private communications, and “the copying of certain information that was subject to U.S. law enforcement requests pursuant to court orders.” The PRC’s efforts targeted a specific number of individuals involved in government or political activity.
Most of us likely don’t fall into the category of “highly targeted individuals” who possess information of interest to the PRC or its affiliated actors. Nonetheless, CISA has now published specific guidance applicable to all iPhone (and Android) users, directly as a result of its investigation into this activity.
The crux of CISA’s warning is simple: All communications between mobile devices are subject to interception, and no single solution completely eliminates the risk. Accordingly, everyone should use only end-to-end encryption. CISA recommends free messaging applications that provide end-to-end encryption (E2EE) between iPhone and Android devices, such as Signal or WhatsApp.
The warning specifically flags the lack of encryption in RCS messages between iPhone and Android users. Last year’s adoption of RCS has enabled more streamlined messaging between iPhone and Android users, including higher-resolution images and videos, read receipts, and other iMessage-like features that work across platforms. However, RCS messages are not end-to-end encrypted between iPhone and Android users. This means carriers or other third parties can potentially access them.
Google uses a proprietary extension to support E2EE between Android devices, but Apple preferred to wait until E2EE became part of the open RCS standard, which happened in March with the release of Universal Profile 3.0. This means end-to-end encryption for RCS should be coming soon for iPhone users, but it’s not here yet.
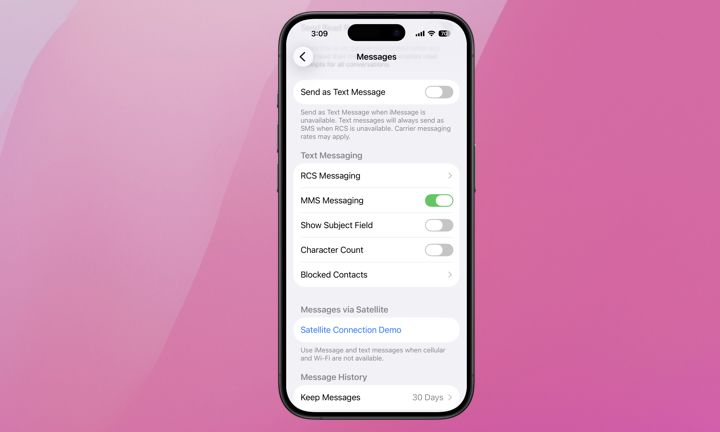
CISA urges iPhone users to disable the Send as Text Message setting. This prevents your phone from falling back to insecure SMS if iMessage is unavailable. Here’s how to find it:
- Open the Settings app on your iPhone.
- If you’re running iOS 18 or later, scroll to the bottom and select Apps.
- Locate and tap Messages.
- Scroll down and toggle off Send as Text Message.
Keep in mind that disabling this means that if an iMessage fails to send due to a poor data connection, your message will not be automatically sent until you regain connectivity, rather than switching to green-bubble SMS. However, you can override this for an individual message by holding your finger on it in the Messages app and choosing Send as Text Message from the menu that appears.
The current iOS 26.2 betas have expanded this setting. Apple has relabeled the toggle “Retry as Text Message” to clarify that SMS is a fallback. Crucially, this switch now also controls fallback for RCS messages — something that couldn’t be disabled in iOS 26.1. The feature description also now explicitly notes that only SMS messages are “not encrypted” — a hint that E2EE for RCS may be coming soon.
If iMessage or RCS are unavailable, iPhone can automatically send text messages using SMS. Text messages sent using SMS are not encrypted. Carrier messaging rates may apply.
CISA makes further recommendations to iPhone users, such as enabling iCloud Private Relay and Lockdown Mode, and reviewing app permissions to ensure only necessary apps have access to sensitive data, such as your location, camera, or microphone. The cyber threat landscape is evolving rapidly and is already incredibly sophisticated. While some of these tips might be overkill for most folks, it can’t hurt to follow the same guidance issued to “highly targeted individuals” if you want to take privacy and security seriously.







