Everything You Need to Know About Phishing and How to Avoid It
 Credit: Tero Vesalainen / Shutterstock
Credit: Tero Vesalainen / Shutterstock
Toggle Dark Mode
Scammers are always finding new ways to get people’s information, but one of the oldest ones in the books is known as phishing. Well, at least old for the internet world. Phishing’s been around since the 90s, and it’s only getting more sophisticated as time goes on.
Even if you believe you’ll never be fooled, phishing is dangerous and sometimes even hard to spot. Fortunately, there are ways you can prevent it and make you and your personal data as secure as possible.
What’s Phishing?
Phishing is a form of cyberattack where a target is contacted by someone pretending to be another person or company the target trusts. The end goal of phishing is to make the target provide sensitive information such as login credentials or private, personal data. It’s also possible that the purpose of phishing is to install malware on the target’s devices.
The term “phishing” is meant to sound similar to “fishing” because the cyber attack is similar to catching fish with hooks and bait. In this case, however, the bait is that it’s a company or a person you can trust, and the hook is something that’s often too good to be true.
How Does It Work?
As we mentioned, the cyber attacker will try to contact someone to get their private information or install malware on a device. The most common way to “phish” is to send emails. Most of the time, attackers send hundreds of emails hoping that someone will fall for their bait. And even though it’s very rare, they may target a single person.
Victims of phishing have also been contacted via text message or phone call.
The attackers usually choose popular companies to spoof and use as bait. According to an Ironscales study from last year, the top five spoofed companies were PayPal, Microsoft, Facebook, eBay, and Amazon.
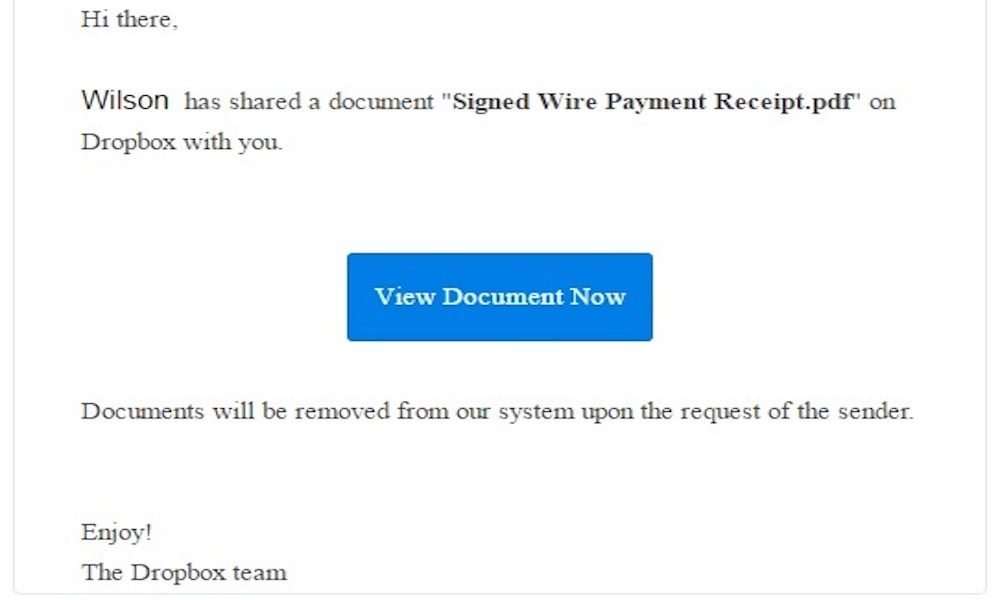
The emails will often offer you something or say something that’ll catch your attention, like a pending invoice or a package that wasn’t delivered. Then they’ll ask you to click on a link to fix the problem or get the reward.
Other popular phishing techniques involve social media. For example, you might receive an email saying that someone tagged you on a photo on Facebook or that someone wants to connect with you on LinkedIn.
Once you click the link, you’ll be redirected to a website that looks like the company’s website, and it’ll ask you to enter your credentials. Other emails will ask you to open the attached file with malicious software to attack your computer.
Phishing Is More Dangerous Than You Imagine
If you’re a tech-savvy person, you might think that phishing is pretty easy to spot, but that’s not always the case. Because of phishing, many attackers have managed to get really important and really private information.
Phishing has cost big tech companies like Google and Facebook over $100 million. And because of phishing, multiple private pictures of celebrities were leaked in 2014, although it was first believed that it was Apple’s fault because of an iCloud breach.
But perhaps the most dangerous thing about this type of cyber attack is how easy it is to create your own phishing scam. Back in 2004, a teenager was filed with their first phishing lawsuit because they managed to get sensitive information like credit card details by imitating the website America Online.
What’s more, is that anyone can start phishing thanks to the so-called “phishing kit.” As you can expect, this is a kit filled with tools and resources that anyone can use to set up their own fake website and even a list of emails so they can start sending spam mail.
How to Avoid Phishing
If big tech companies like Google, Sony, and Facebook fall victim to phishing, all of us are at risk too. Fortunately, there are ways to avoid being scammed.
- Check for spelling: Unlike the actual companies, many cyber attackers don’t worry that much about grammar. So make sure to read the email carefully. If you spot any spelling and grammar mistakes, it’s possible that the company didn’t send that email.
- Read the URLs: If you need to open a link, make sure to read it carefully. Since they can’t use the same domain name, people will change it to look like the original. For instance, instead of “America,” the link might actually read “Arnerica.” Nevertheless, it looks normal at first glance. That’s why you need to read it carefully.
- See who sent the email: Another clue of a phishing email is the email address of the person who sent it. Be careful if the person’s name or email address seems “fishy” (pun intended).
- If it’s too good to be true, it probably is: If an email talks about a surprise invoice or an unexpected package, you should avoid opening links or files until you’re sure it’s not a phishing email.
- Contact the company: If you received a random email from your bank or other company, but you feel it’s suspicious, try contacting the company with a new email or a phone call. They can help you figure out if it was actually them or not.
Common Phishing Email Subjects
Knowbe4.com published some of the most common email subjects that people click on. As you can see from the image below, the biggest subjects come from LinkedIn and Facebook.
Emails like “Join My Network,” “Add Me,” or “New Message” is really compelling, especially if you’re looking for new jobs or connections. Other subjects like “Your Friend Tagged a Photo of You” are pretty common since they raise people’s curiosity and make you feel special.
Outside of social media, the most common subjects relate to packages and deliveries. Subjects like “Your Order with Amazon.com” or “A Delivery Attempt Was Made” make most of us want to click immediately and figure out what’s happening.
If you receive any of these subjects, make sure the websites and email addresses are correct before clicking on a link or opening an attached file.
If you want to learn more real examples, you can see the list of phishing samples Lehigh University shared a few years ago. It’s got samples of phishing emails spoofing Dropbox, Google, and Lehigh University itself.