How New Malware Can Affect Non-Jailbroken iPhones and iPads

Toggle Dark Mode
In the past, standard iOS devices have, generally speaking, been almost immune to malware. Because of how tightly Apple controls apps that are loaded into the app store, it’s been very difficult for infected apps to make it onto users’ phones. The exception has been either with jailbroken devices – devices that have removed some of Apple’s software restrictions, usually with the purpose of installing pirated apps, or apps that are otherwise unavailable in the app store – or via the abuse of enterprise certificates, which allow companies to develop proprietary iOS apps for employee use. However, a new type of malware has just been discovered that can now infect several non-jailbroken iOS devices via a new method of transfer.
Security company Palo Alto Networks has recently discovered a new family of iOS malware that can infect standard iOS devices. The malware, which they have named ‘AceDeceiver’, doesn’t exploit jailbroken devices, nor does it abuse enterprise certificates to load itself onto iPhones or iPads. According to a blog post on Palo Alto Network’s website, AceDeceiver uses a method called “FairPlay Man-in-the-Middle”, which has been used to distribute pirated iOS apps in the past, to spread the infected apps.

The technique takes advantage of the fact that Apple allows users to purchase iOS apps onto their computer through the iTunes App Store, which are then installed onto their iOS device. According to Palo Alto Networks, apps downloaded from the iTunes App Store and then installed on iOS devices will go through an authorization process, where the malware can be inserted.
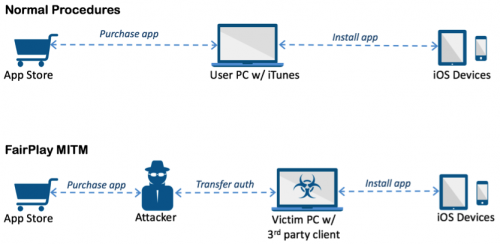
“iOS devices will request an authorization code for each app installed to prove the app was actually purchased. In the FairPlay MITM attack, attackers purchase an app from App Store then intercept and save the authorization code. They then developed PC software that simulates the iTunes client behaviors, and tricks iOS devices to believe the app was purchased by victim. Therefore, the user can install apps they never actually paid for, and the creator of the software can install potentially malicious apps without the user’s knowledge.
The malware has appeared in three different iOS apps, all disguised as wallpaper apps. Palo Atlo Networks has notified Apple of the rogue apps, and all three have been removed. The good news is, it’s highly unlikely that the malware has affected any of our readers. For one – the malware contains a geotag, only displaying malicious behavior when a user is located in China. Second, the malware has only been loaded via Windows software called “Aisi Helper”, which, according to Palo Alto Networks, “purports to be software that provides services for iOS devices such as system re-installation, jailbreaking, system backup, device management, and system cleaning.” It’s likely that the malware has only affected a small amount of users located in China.
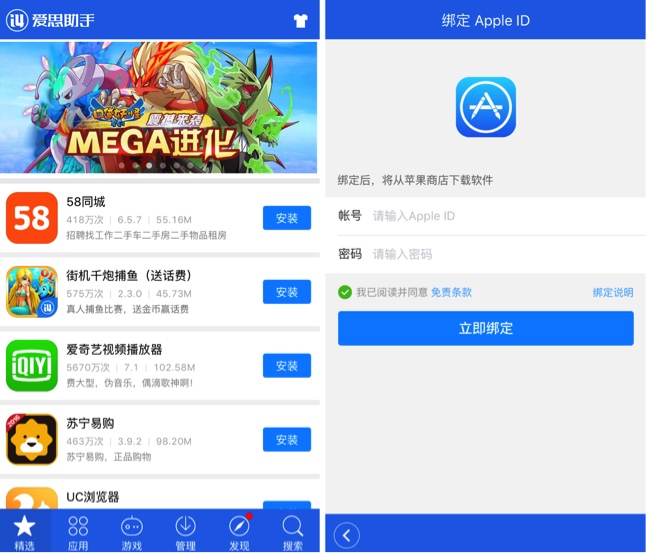
The bad news, however, is that this technique could be used in the future by other hackers who copy the method AceDeceiver uses to infect iOS devices. At the moment, it’s recommended that users who have ever come across the “Aisi Helper” software be sure to uninstall it immediately, and run a virus/malware scan on their computers. To avoid problems in the future, it’s best to stay away from any third-party software intended for iOS devices, and only install apps from the official App Store.
Learn More: Leaked Packaging Image Confirms iPhone SE Name, Apple Pay, and More






