This New Tool Can Harvest Your Most Personal Data from iCloud Without You Knowing
 Credit: Jaririyawat / Shutterstock
Credit: Jaririyawat / ShutterstockToggle Dark Mode
Although Apple is known for taking a very strong stance on protecting the privacy and security of its customers — it’s resistance to the FBI’s requests to create a back door in iOS has become the stuff of legends — the company still faces a cat-and-mouse game in trying to stay ahead of security firms that are determined to profit by creating tools designed explicitly to break into Apple’s iPhone and related services.
Even in the famous case of the San Bernardino shooter, the FBI eventually gave up on coercing Apple, finding another way into the iPhone under investigation by contracting the services of an unnamed third party contractor, which many believe to be the Israeli security company Cellebrite.
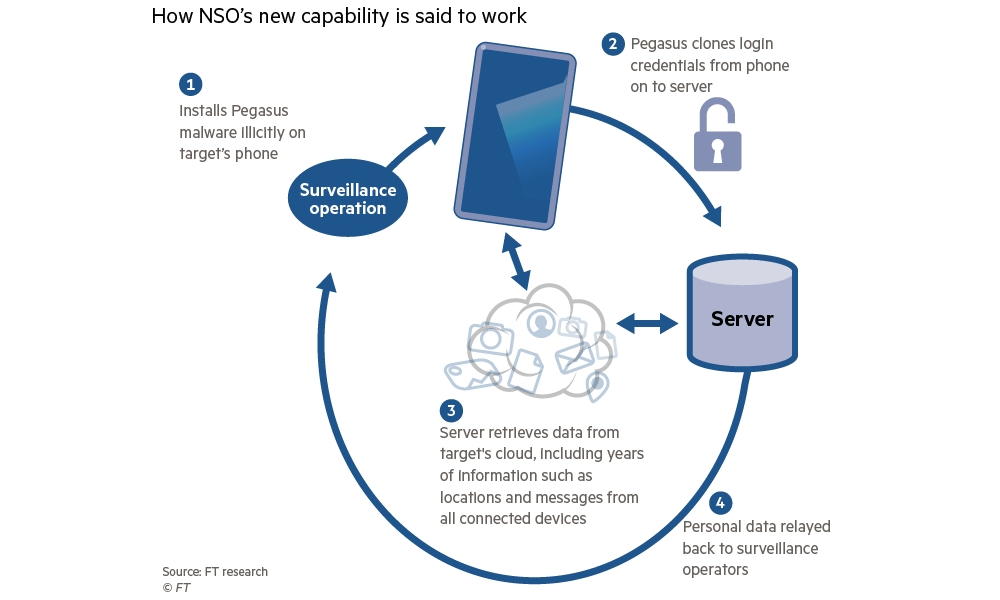
Now another Israeli security firm is boasting of its ability to surreptitiously hack into users’ iCloud accounts by impersonating their iPhone. According to The Financial Times, the firm, NSO Group, has told buyers that its Pegasus smartphone malware now has the ability to scrape all of an individual’s data from the servers of Apple, Google, Facebook, Amazon, and Microsoft, and do so without triggering any alerts that would let the user or the organization know that their data is being illegimately accessed.
How It Works
According to sources familiar with the company’s sales pitch who also described a recent product demonstration, the new technique works by extracting and copying the authentication keys used to access iCloud — and other services such as Google Drive and Facebook Messenger — directly from a user’s iPhone (or Android phone). These credentials are then used to impersonate the device — including even its original location — in order to get the same access to the cloud that the user themselves has.
Further, because Apple’s servers assume the connection is coming from the legitimate user’s actual phone, no red flags are raised, so there are no prompts for two-factor authentication, and no warning emails or notifications are sent. For all intents and purposes, the new access requests are business as usual as far as the service providers are concerned.
What Are the Risks?
The software, Pegasus, is a type of malware that infects target smartphones, and while iPhones and iOS are generally more hardened against this sort of thing, they’re by no means immune. Since the information in the report came entirely from NSO Group’s sales pitches, very few technical details are available on how it actually works, although Apple didn’t deny the possibility that such a tool could exist and could infect iPhones, but emphasized that due to the nature of iOS, it’s extremely unlikely to be used for anything more than very specific, targeted attacks.
While some expensive tools may exist to perform targeted attacks on a very small number of devices, we do not believe these are useful for widespread attacks against consumers.
Apple, in a statement to The FInancial TImes
Pegasus was originally developed as a tool for spy agencies and governments to harvest data from the smartphones of targeted individuals, however up until now it’s been limited to accessing the data stored on the smartphone itself. This new development would allow it to access a much larger trove of information, including full location data history, along with long-archived messages and photos.
However, it’s important to Keep in mind that Apple uses a special hardware chip known as the Secure Enclave to store extremely sensitive information like saved passwords, Health data, HomeKit data, Apple Pay, Touch ID, and Face ID data. This means that it’s extremely unlikely that Pegasus or other malware of this nature would be able to access this kind of data.
To be fair, NSO Group maintains strict policies on who it sells and provides these tools to, so it’s not like just anybody can get their hands on Pegasus in order to exploit it. The software tool is actually classified as a “weapon” by the Israeli government, placing additional restrictions on who it can be sold to, and NSO insists that it’s only sold to “responsible governments to help prevent terrorist attacks and crimes.”
Despite this, however, the Pegasus malware has been discovered by security researchers on phones used by human rights activists and journalists around the world, which suggests that it is being used by oppressive regimes for less altruistic purposes. Whether this is the result of NSO selling Pegasus directly to these governments, or whether they’re obtaining it in some other way is unclear.
However, this is ultimately the nature of the problem, and is exactly why Tim Cook said that creating a backdoor for the FBI would be the “software equivalent of cancer”; once a tool or capability exists to bypass security, Pandora’s box has already been opened, and even the best policies and restrictions can’t ensure that these tools will only be used by those with noble intentions. Apple’s very responsible take is that it’s far better to not create a weapon at all than to risk it being used for nefarious purposes.
Still, between the nature of the tool itself and the fact that Apple is almost guaranteed to find and close the security holes that Pegasus is exploiting, there’s little cause for most iPhone users to be concerned. Apple’s walled garden already makes it difficult for these kinds of apps to compromise security, and there’s a good chance that Apple will have improved its security even further by the time tools like Pegasus inevitably fall into the wrong hands.
In the meantime, if you’re an iPhone user and are concerned about Pegasus, changing passwords and revoking login permissions on a semi-regular basis is one way to protect yourself from this kind of eavesdropping, since this essentially renders the keys stolen by the Pegasus malware useless.