FBI Warns Against ‘Juice Jacking’ Threat From Public USB Chargers
 Credit: Andreas Haslinger
Credit: Andreas HaslingerToggle Dark Mode
Using a public charging station can be a convenient way to give your iPhone a quick boost while at a public transit station, airport lounge, or coffee shop, but they may be giving your device more than just charging power.
After all, the Lightning port on your iPhone can do more than just charge it. While syncing data to your iPhone over a wired connection from your Mac or PC seems rather quaint in an era where services like Apple Music, iCloud, and over-the-air iOS updates have taken over, the port on the bottom of your phone can still be used to transfer data, install software, or update your operating system — and it appears that cybercriminals are taking advantage of that.
The FBI issued a new warning this week against using these “free charging stations” often found in airports and shopping centers, suggesting that you “carry your own charger and USB cord” to plug into an ordinary electrical outlet.
While the FBI goes on to say that “bad actors” have figured out how to exploit public USB ports, it’s not clear if this latest warning comes as a result of any ongoing investigations. Still, it’s good advice either way; many folks are so used to using Lightning connections solely for charging that it’s easy to forget that they’re also a pathway for malicious software to enter your iPhone.
In fact, the danger goes beyond public USB charging stations. The chips involved in carrying out these attacks are small enough that even an innocuous-looking USB to Lightning cable can potentially compromise your security. This means that using any unknown charging cable can present a risk, even if you can see that it’s connected to a regular charger and power outlet.
This isn’t merely a Lightning problem; devices with USB-C ports can also be compromised, including Apple’s iPads and its upcoming iPhone 15 models, which are expected to switch to USB-C.
What’s the Risk for iPhone Users?
Firstly, the good news is that there are no risks from using Qi or MagSafe wireless chargers. Unlike physical ports, Qi only supports power transfer, and Apple’s MagSafe standard only allows for the exchange of very specific types of information directly related to the connected accessory, such as identifying the color of one of Apple’s MagSafe cases or how much power is left in your MagSafe battery pack. This means you don’t need to worry about dropping your iPhone on a wireless charger in a public venue like a coffee shop.
As long as you’re running iOS 12 or later — and you really should be — your iPhone is also protected by a feature known as USB Restricted Mode; technically, this first appeared in iOS 11.4, but Apple had some bugs to work out before it was ready for prime time.
Today, USB Restricted Mode is essentially a firewall that prevents your iPhone from exchanging data with any unknown devices connected to the Lightning port until you explicitly authorize them by responding to a “Trust this Computer” pop-up — which can only be done when your iPhone is unlocked.
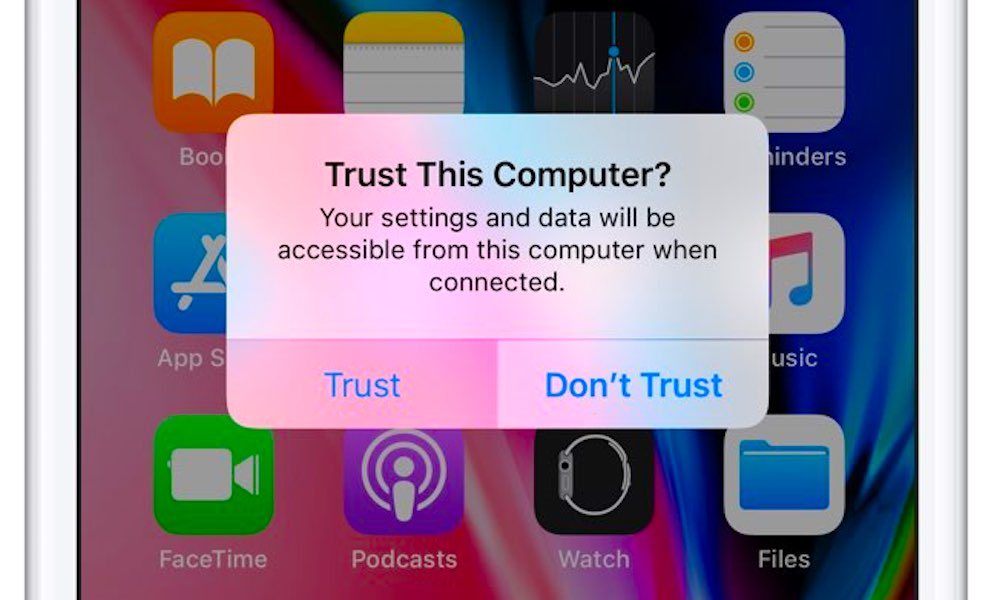
That prompt asking you to “trust” a connected device is your first line of defense against malicious USB/Lightning connections. You don’t need to trust a charger for your iPhone to receive power, so if a public USB “charging station” asks you to trust it, don’t. Disconnect your iPhone and walk away.
Nevertheless, while USB Restricted Mode offers good protection, it’s not a panacea. The best way to protect your iPhone from malicious USB cables and chargers is to avoid connecting to them in the first place. Follow the FBI’s advice and carry your own trusted cable and charger and use a standard electrical outlet. You can also consider investing in a portable battery pack for an even more convenient way of juicing up your iPhone on the go.







