7 Reasons Why Apple Creates the Most ‘Unhackable’ Devices
 Credit: Konstantin Savusia / Shutterstock
Credit: Konstantin Savusia / Shutterstock
Apple devices have a reputation for being secure and privacy-respecting. And while Apple has certainly played up that angle in recent years, there is undoubtedly truth to that reputation.
To be clear, Apple devices aren’t "unhackable" — there’s no such thing as an "unhackable" device. But Apple's security features, and the software decisions it's made with its software, has created some of the most secure consumer devices in the world. Continue reading to browse seven reasons why that's the case!
iOS’s Walled Garden
It’s easy to forget that when the iPhone first launched, there were no third-party apps. When Apple begrudgingly added apps eventually, it did so with a slew of restrictions. This is the so-called “walled garden” of Apple’s security.
In the beginning, and even now, most apps can only see a highly curated portion of the file system on an iOS device. The result is a smartphone App Store where there are few malicious apps with any real power to do things. Importantly, Apple can also easily delete or “recall” apps that abuse or bypass its guidelines.
Constant Software Updates
When Apple identifies a vulnerability or an issue with its software, it typically patches the bug in the next software update (or as soon as possible). That’s already a huge step above the fragmented Android ecosystem. But once a patch is out, it’s up to the user to actually download and install that update.
Luckily, Apple’s devices are extremely easy to update when compared to some of its competitors — due to the company’s tight integration and controlled device base. Apple can also be annoyingly persistent about its updates, which turns out to be a good thing for users.
macOS Security Features
Back in the day, it was widely believed that Macs would never get computer viruses. That isn’t necessarily true, but there are a lot fewer threats to Mac systems than there are for Windows.
But Macs do a lot to protect their users, including systems like System Integrity Protection, Gatekeeper and code-signing checks. Newer features, like the baked-in T2 chip, can go even further to encrypt and secure a Mac’s drive by barring unsigned operating systems or apps from booting after a teardown.
Encryption Everywhere
Pretty much all Apple devices and systems feature encryption in some way. If you use FileVault 2 on a Mac, your system is encrypted. iOS devices are also automatically encrypted and secured by your passcode, fingerprint or facial data.
When data is sent to Apple’s servers, it’s also end-to-end encrypted. That goes for your location data in Maps or the contents of the texts you send in Messages. You can rest assured that, in pretty much every way, Apple tries to keep your data away from prying eyes. (That includes itself, since even it doesn’t have the keys to unlock your data.)
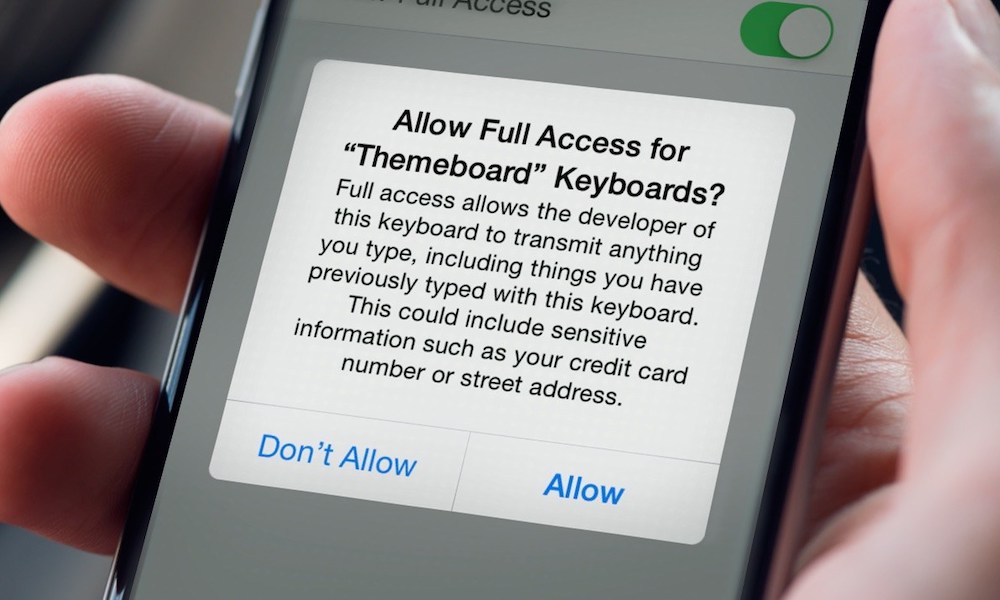
App Permissions
App permissions are an underrated feature of Apple’s ecosystem. You may even find them annoying if you’re bugged frequently by Bluetooth usage or app permission alerts. But they serve a purpose.
Without these permissions, third-party apps (or malware) have a much harder time using important parts of your system. This is true across pretty much any Apple product with app permissions built-in. It gives users a sense of agency and the ability to control what data and system features their apps can use.
Find My & Activation Lock
Physical security is every bit as important as digital security. After all, what’s the use of a good anti-spyware app when someone can just take off with your device and extract your data?
Apple has measures in place to prevent this, including the aforementioned encryption and the T2 chip that blocks certain repair processes. But it also includes Find My, which can help users track, ping or wipe stolen devices, and Activation Lock, which helps prevent Apple devices from being wiped and resold by thieves.
Security Is Built from the Ground Up
Apple uses the Mac subkernel as the basis for most of its operating systems — including macOS, iOS, iPadOS, tvOS and watchOS. Even if you don’t know what that is, it’s significant because security has to be built-in from the ground up.
That’s in stark contrast to other operating systems with no built-in security. As a result, those operating systems need to rely on additional utilities to provide it. That isn’t even to mention Apple’s strong security culture and its existing reputation, which pushes it to keep updating and refining its security processes.