9 Things You’re Doing That Make You an Easy Target for Hackers
 Credit: Travel man / Shutterstock
Credit: Travel man / Shutterstock
Companies and governments aren’t the only entities that get hacked. No matter who you are or where you’re located, you — yes, you — can also easily end up a target for a hacker. That fact is made worse because many people aren’t taking their online security seriously enough. But before you panic too much, there are some easy ways to shore up your online defenses. Continue reading to learn about nine important cybersecurity practices you probably aren’t doing.
Not Changing Your Default Passwords
There are plenty of everyday, internet-connected objects in your house that can be hacked. And if you don’t change the default passwords for those devices, you’re only making a hacker’s (illicit) job easier.
If there’s a device that has a password, such as a router, modem or another smart IoT product, it’s strongly recommended that you change the default password for it. If not, someone could easily find that password with just a quick Google search.
Not Practicing Good Password Management
Your password is the first line of defense against someone accessing your online accounts and hardware. And yet, despite all of the advice out there, many people still rely on weak or reused passwords.
First off, don’t use an easy-to-guess password. It’s also important not to reuse any password across multiple accounts. Because of those two best practices, it’s always a good idea to use a password manager.
Posting Private Details
If you’re like most of us, you probably post at least some content online. From geotagged pictures of the places you frequent to images of your desktop computer setup, there are plenty of ways for hackers to use the information you put online against you.
The exact tactics that hackers and social engineers use will differ. But for you, it all comes down to being mindful about the data you’re posting. Make sure that you aren’t revealing anything too sensitive. And if you do post something personal, keep in mind that a phishing attempt could use that information to seem more legitimate.
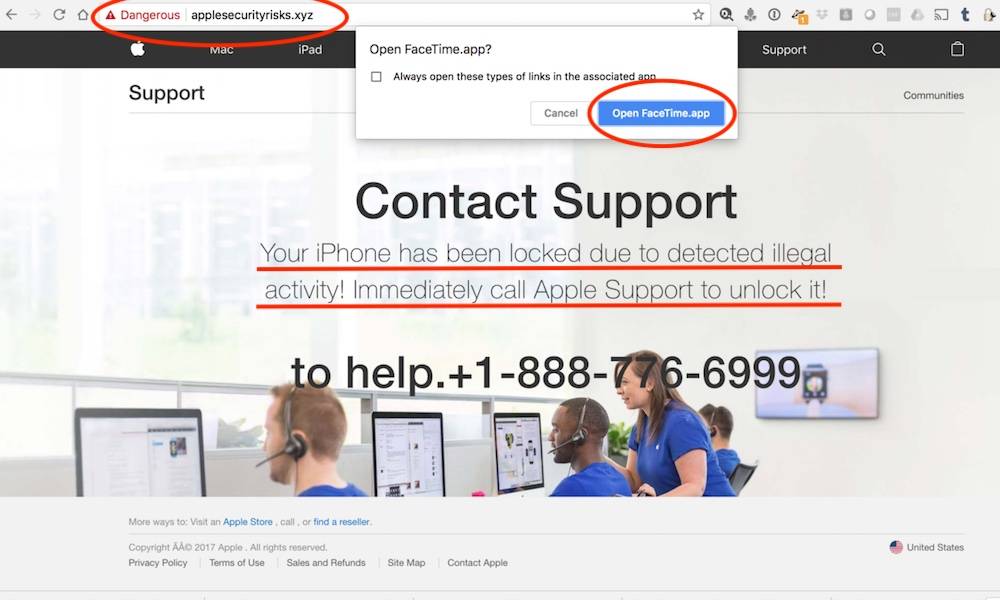
Not Vetting Phone Calls & Login Forums
Hacking doesn’t just involve lines of code and passwords anymore. In fact, there’s been an increase in social engineering attacks — “hacking” people, in other words. If you need an example, just think of phishing campaigns or scam phone calls.
To avoid these types of attacks, it’s always a best practice to keep a close eye on unsolicited emails and phone calls. If you get a communication you weren’t expecting, it never hurts to just hang up or delete the email and contact the supposed sender/caller through a verified medium.
Not Enabling Two-Factor Authentication
We talked about good password management earlier. And part of the reason why you want to use unique passwords is that there’s a good chance that one of the websites or services you use will be breached at some point.
But in addition to using different passwords across your accounts, you can add another layer of defense by enabling two-factor authentication (2FA) whenever possible. Most 2FA isn’t perfect, but a little additional effort can go a long way into securing your online presence.
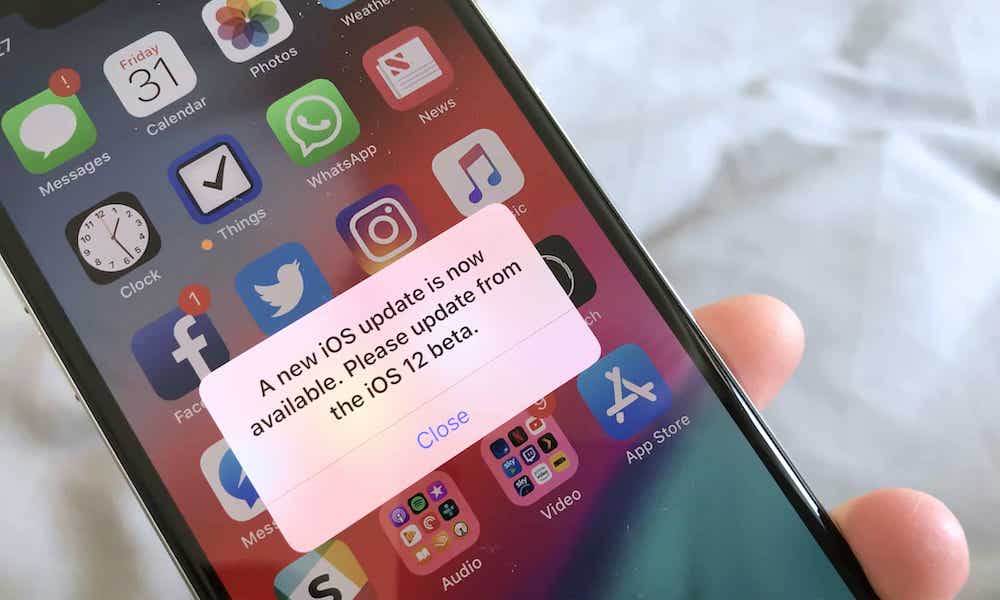
Not Being Careful About What You Click
One of the easiest ways for a hacker to get malware onto your computer is to simply trick you into installing it yourself. Because of that, you’ll want to be extremely careful about the sites you visit, the links you click and the apps that you download.
Ideally, only visit authentic and secure websites online and avoid clicking on anything suspicious in emails or social media posts. When it comes to apps, get them from an official App Store whenever possible. If not, make sure you do research on the developer and download the app from a trusted source.
Not Taking Physical Security Into Account
There are devices out there that, when plugged into a computer’s USB port, can extract information or download malware in just a few seconds. Your device’s physical security is often overlooked, but arguably just as important as digital security.
- Don’t leave your laptop or phones unattended when in public places.
- Make sure all of your devices have a password or passcode protecting them.
- And be aware that, with just a few seconds of physical access, an attacker could very well do some damage.
Not Updating Your Software
We always recommend updating to the latest version of whatever software you’re running. That isn’t just because of cool new features and bug fixes. It’s also because most updates contain at least some important security fixes.
Those security fixes almost always patch vulnerabilities that can easily be exploited by a bad actor. If you don’t update your device regularly, you’re just giving an attacker more opportunities to target and successfully exploit your device.
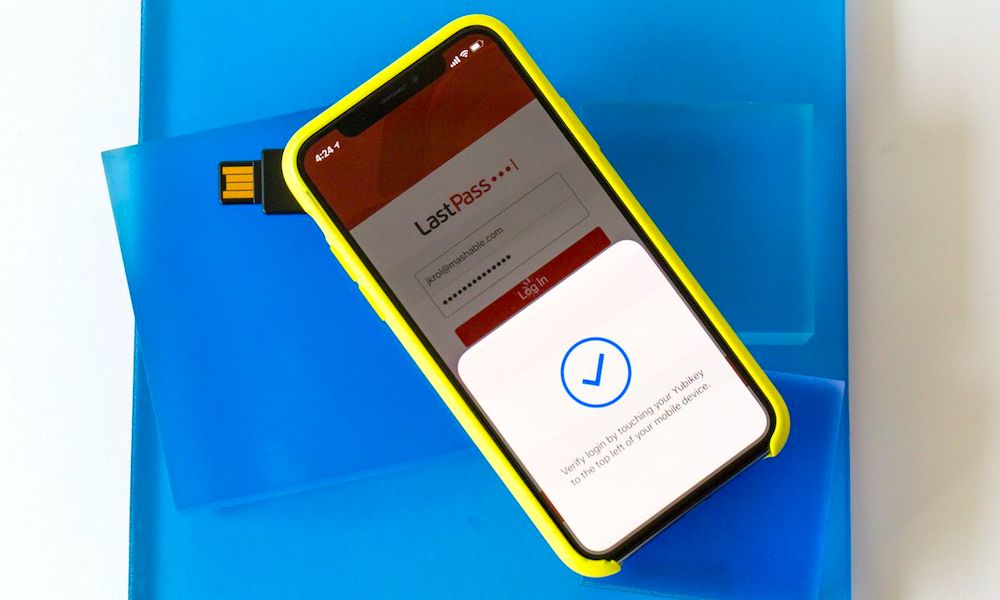
Consider Physical 2FA
Depending on your exact circumstances and security needs, it’s also probably a good idea to invest in a security key like a YubiKey. These tools, which look like small USB drives, are essentially a form of 2FA. Instead of an SMS text message, you plug one of these keys into your device to get access to your account.
This comes with its own set of tradeoffs and benefits, of course. But it’s much more secure than 2FA via SMS text messaging. That’s because, through a technique called SIM jacking, an attacker can theoretically intercept your 2FA code messages and gain access to your accounts remotely.