5 Ways to Spot an ‘Apple’ Phishing Email So You Don’t Get Scammed
 Credit: NBC Los Angeles
Credit: NBC Los Angeles
By most accounts, phishing attacks are not only becoming increasingly common — they’re also getting much more sophisticated. But while anyone can be targeted by a phishing account, not everyone has to be a victim of the scam. Keeping a few things in mind when you receive an unsolicited communication can go a long way in keeping you — and your sensitive information — safe from scammers.
Just take a look at a recently discovered phishing scam sent to iDrop News from a reader named Jenni, who provided screenshots of the email which are spread out over the following pages.
It seems like a newer phishing attack, but it relies on age-old social engineering tactics. But it also serves as a good opportunity to go over the steps of spotting a phishing attack. While phishing attacks and other malicious scams can be very sophisticated and appear to be legitimate, there are usually some telltale signs that give them away. Use the right arrow to learn 5 Ways to Spot an 'Apple' Phishing Email So You Don't Get Scammed.
5 Check the Email Address It Was Sent From
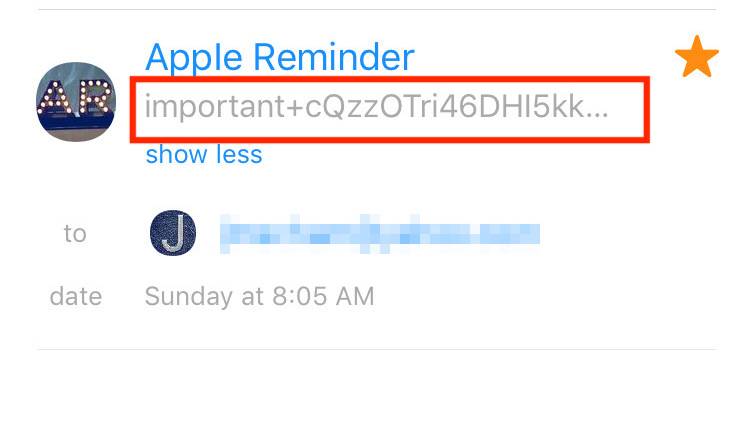
By and far, this is typically the easiest way to identify a fake email address. Communications from Apple will always use an address tied to a legitimate Apple domain name. There are no exceptions.
Emails that end in apple.com are the most commonly used. That includes “id.apple.com” or email.apple.com.”
As far as emails that are not authentic, they’re harder to list because they can be so diverse.
The best rule is this: if you have even the slightest doubt about an email, just delete it.
4 Take Note of Bad Grammar
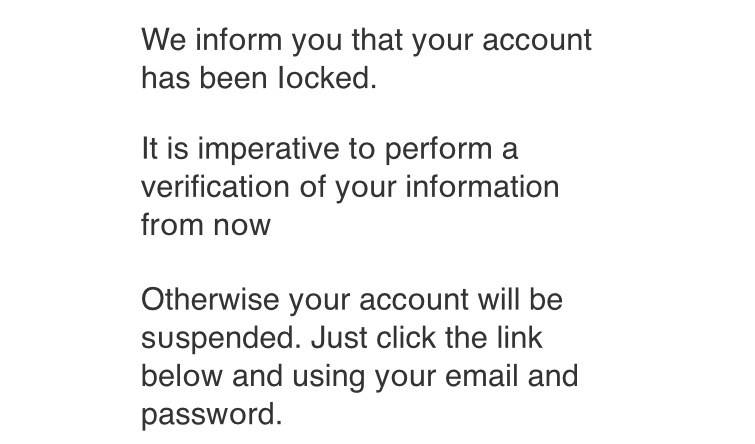
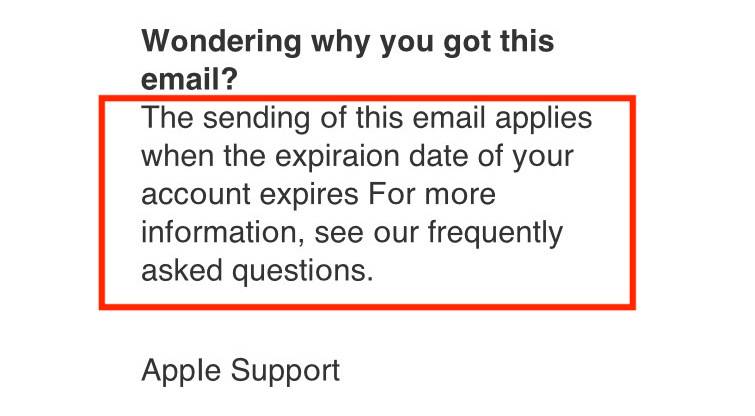
Though this isn’t always the case, most phishing attacks and scams will be written with poor grammar and spelling. Just take a look at the email.
“It is imperative to perform a certification of your information from now” isn’t a sentence that screams authenticity.
Similarly, “just click the link below and using your email and password” suffers from poor parallel structure.
You don’t have to be an English teacher or a grammar expert to spot these mild inconsistencies. Just read the sentences out loud and see if they make sense.
It’s not impossible for an authentic Apple email to contain a typo, but it’s incredibly unlikely.
3 Search for Sketchy Signs
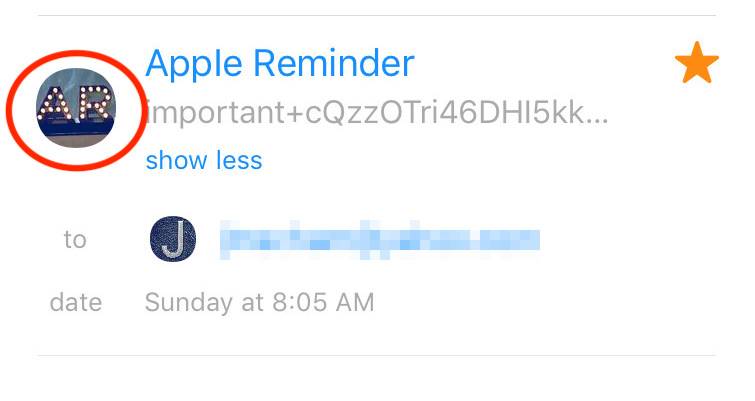
Apple, being one of the largest companies in the world, is not going to rely on shoddy graphics and icons.
In the phishing email provided to us by Jenni, for example, the sender has a user avatar that’s pre-generated by Google. Suffice to say, Apple would not use that icon.
On a similar note, the phishing email uses the contact name of “Apple Reminder.”
While this can cause confusion as to authenticity, just note that contact names aren’t a reliable indicator of legitimacy. In other words, you should always look at the email address — not the contact name.
2 Did They Address You By Your Name?

This is a small one, but it’s worth noting anyone because it’s another sure sign of positive identification.
Apple will never address you by your email address in communications. Apple will always use your name.
Basically, if an email starts with “Dear yourname@youremail.com” — it will always be a fake.
Oftentimes, scammers won’t have access to your full name. Which is why they use your email to address you.
Apple, on the other hand, does. In the vast majority of cases, Apple will use your full name on record when it’s addressing you.
1 Analyze the Content
While exceptions could exist, the general rule is that Apple does not send unsolicited communications to its customers.
If you take note of the emails actually from Apple in your inbox, you’ll see that they’re always the result of an action you took.
For example, it might be a receipt for a purchase you made. Or, it could be an email letting you know that you edited your Apple ID information.
Apple will not disable your account for delinquency — there are no “expiration dates” for Apple IDs.
Similarly, Apple emails are typically informational. They won’t ask you to sign-in or verify any personal information by clicking on a link.
Here is the phishing email in full. Check it out in further detail. Can you pinpoint all of the tell-tale signs?