Apple Blocks GrayKey iOS Hacking Device Shocking Security Experts
 Credit: Malwarebytes Labs
Credit: Malwarebytes Labs
Toggle Dark Mode
Apple’s freshest update to the iOS operating system came with a bevy of security upgrades that strengthen consumers’ confidence in the integrity of their iPhones. The security measures include end-to-end encryption of messages and FaceTime video chats, safeguards that make it harder for data companies to gather information for targeted advertising, and a web portal that allows you to check up on how much information Apple has collected about you.
Such moves have put Apple at odds with law enforcement agencies who seek to break into suspected criminals’ iPhones. A cottage industry has formed in response to develop tools like Cellebrite to help hackers crack the encryption protecting Apple’s devices.
Government agents now regularly pay to use these tools. Most memorably, the FBI reported paid hundreds of thousands of dollars to Cellebrite in order to break into the San Bernardino shooter’s iPhone 5c.
Apple, in turn, treats such exploits as it would any other, by seeking to close loopholes and safeguard the privacy of Apple users against all hackers.
A recently discovered Apple security feat has been turning heads. It appears that with iOS 12, Apple has successfully crippled GrayKey, a hacking device that until recently, was able to break into locked iPhones for a hefty sum—sometimes charging as much as $15,000. On iOS 12 devices, GrayKey is only able to extract unencrypted data and some metadata, effectively rendering it useless.
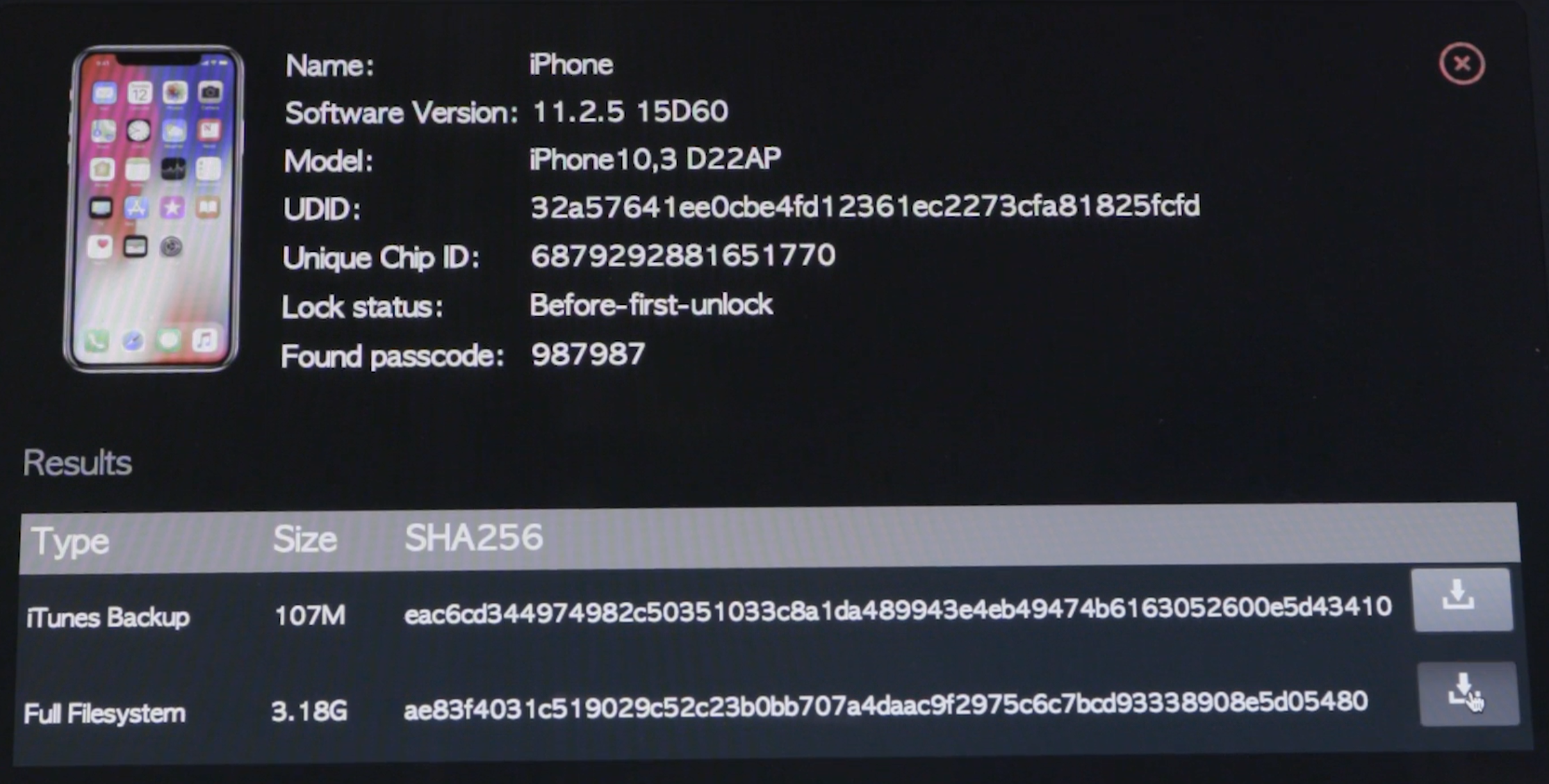
Law enforcement agents have taken notice of the latest development in the contest between Apple and hackers. John Sherwin, a police captain in Minnesota, has corroborated reports that Apple had essentially killed GrayKey to Forbes’ Thomas Brewster, who broke the story.
“That’s a fairly accurate assessment as to what we have experienced”, Sherwin said.
Evidently, no one outside of Apple is yet aware of how the company did it. Vladimir Katalov, a cybersecurity expert with Elcomsoft who has established a track record of uncovering flaws in Apple devices, also admitted that he was at a loss.
“No idea. It could be everything from better kernel protection to stronger configuration-profile installation restrictions,” he said to Forbes. The kernel is the core part of the operating system, from which the rest of iOS launches. Configuration profiles typically allow individuals and companies to customize the ways in which iOS apps work.”
Though Apple seems to have gotten the upper hand now, it’s safe to assume that its security measures are not perfect.
“Give it time and I am sure a ‘workaround’ will be developed … and then the cycle will repeat”, Sherwin added. “Someone is always building a better mousetrap, whether it’s Apple or someone trying to defeat device security.”
Apple CEO Tim Cook, meanwhile, has been publicly urging government officials in Europe and Australia to support rather than undermine his company’s security efforts.






