This Cool New iOS 14 ‘BlastDoor’ Will Protect You from Dangerous iMessages
 Credit: guteksk7 / Shutterstock
Credit: guteksk7 / ShutterstockToggle Dark Mode
Over the past few years, malicious text messages have become a very common method for hackers to launch malware attacks against iPhone users, but now it looks like Apple has quietly baked some hard-line security into iOS 14 to help make sure that what happens in your Messages app stays in your Messages app.
For years, Apple has been playing a cat-and-mouse game with these kinds of bugs, which largely began as pranks, allowing people to send weird messages that would cause their friends’ iPhones to crash, but they eventually became much more serious, with bugs that could have allowed hackers to run malicious code on your iPhone by simply sending a text message that you had to do nothing more than simply look at.
While Apple has usually been fairly quick to patch these vulnerabilities, as of iOS 14 it appears to have decided to take a more proactive approach by isolating the Messages app even more strictly from the rest of the operating system.
As reported by ZDNet, a security researcher with Google’s Project Zero — the same group responsible for discovering previous text message vulnerabilities — has found an entirely new security framework in iOS 14 after digging deeper into the code.
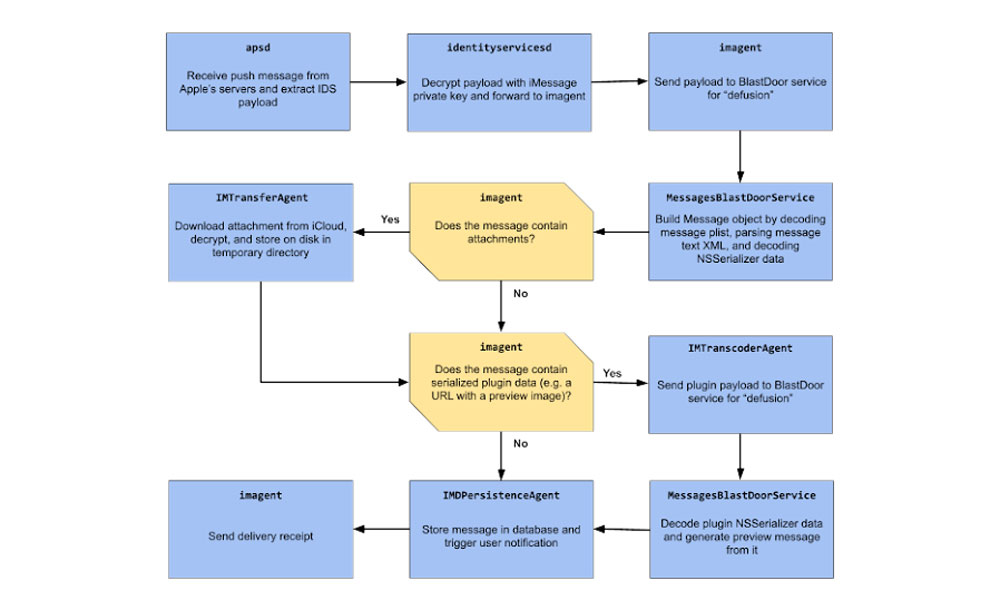
Dubbed BlastDoor, the new iOS security feature is designed to analyze incoming message content in a completely secure and isolated environment, akin to physically taking a suspicious parcel into a secure room to check for explosives hidden inside.
What’s notable is that Apple hasn’t gone out of its way to advertise this new feature; the Google researcher, Samuel Groß, happened across it while trying to determine why KISMET — a serious exploit discovered last year by The Citizen Lab at the University of Toronto — had actually been neutered by “new security protections” in iOS 14.
Although iOS has had “sandboxing” mechanisms in place from the very first days of the App Store — an important security feature that forces apps to run in their own isolated spaces, preventing them from interacting with each other or the operating system at large — the new BlastDoor feature goes even deeper, effectively creating a sandbox within a sandbox.
How BlastDoor Works
As Groß explains, BlastDoor operates exclusively within the Messages app, taking all incoming messages and moving them into a secure area for “defusion” before they’re passed through to the main Messages app.
Within this “blast-proof” area, any code that happens to run is completely restricted from interacting even with the actual Messages app, much less the rest of iOS. This effectively neuters any malicious code that may be contained in an SMS text message or iMessage.
Since no text message should ever contain any executable code, it’s fairly easy for Apple to draw a line in the sand; it doesn’t need to worry about analyzing the code to see if it’s malicious — it merely has to test for the existence of any executable code at all.
It’s not just BlastDoor either; while that’s the strongest of the sandboxed services, there are actually seven other security checkpoints that an incoming text message travels through before it’s presented to the user, with all of them now being properly sandboxed from the main Messages app, and even from each other.
While the cat-and-mouse game won’t end entirely, as hackers try to figure out a way to break out of the BlastDoor region, it’s going to be much more challenging as Apple has locked down pretty much everything it possibly can — there’s no outbound network access, no interaction with the traditionally vulnerable IOKit drivers, and virtually no file system interaction available. Just like a real-world blast container, if the code in an incoming iMessage blows up, the explosion won’t travel beyond the BlastDoor sandbox.
Overall, these changes are probably very close to the best that could’ve been done given the need for backwards compatibility, and they should have a significant impact on the security of iMessage and the platform as a whole. It’s great to see Apple putting aside the resources for these kinds of large refactorings to improve end users’ security.
Samuel Groß, security researcher, Google Project Zero
Groß also commended Apple for going on the offensive in building a proactive security framework into iOS 14, noting that BlastDoor actually highlights the value of making structural improvements to security rather than simply focusing on fixing individual bugs.